Using ADC to block Chrome extensions
There may be situations where you wish to block end-users from utilizing a specific Google Chrome browser extension. This can be accomplished, fairly easily, via Application and Device Control in Symantec Endpoint Protection. The first part of this process is identifying not just the extension to block, but more importantly the unique ID associated with the extension. Below are the steps to find this UID and put the rule in place.
Find the Chrome Extension UID:
1) Open up Chrome and type in chrome://extensions in the URL bar, or go to Settings > Extensions.
2) Enable "Developer Mode" by checking the checkbox top right.

3) Open up the Chrome Web Store via the "Get more extensions" hyperlink.
4) Search for the extension(s) you wish to block.
5) Click on the "Add to Chrome" button to install the extension.
6) Confirm you wish to install by clicking the "Add extension" button in the new prompt.
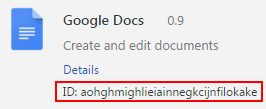
7) Return to the chrome://extensions page and locate the extension in question.
8) Note that with "Developer Mode" enabled you will now see an ID: parameter. The string value listed is what we are after.
Create your new ADC block policy:
1) Within the SEP Manager console click on Policies then highlight Application and Device Control.
2) Either edit an existing policy or create a new one.
3) Within the policy, visit the "Application Control" section and add a new rule set.

4) Give your rule a meaningful name. (e.g. Block Chrome Extensions)
5) To the right under Properties, click "Add..." and either assign the * wildcard or the process name chrome.exe, click "OK".

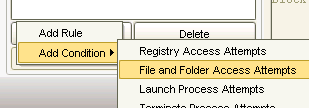
6) At the bottom, under "Rules" click the "Add..." button, then "Add Condition", finally selecting "File and Folder Access Attempts".
7) Again provide a meaningful name, then click "Add..." to the right under properties.
8) For the "File or Folder Name To Match" field use the following path with the Chrome extension ID appended:
- %systemdrive%\Users\*\AppData\Local\Google\Chrome\User Data\Default\Extensions\aohghmighlieiainnegkcijnfilokake
- Alternatively, you could use an asterisk (*) wildcard in place of the extension ID to block all Chrome extensions.
9) Leave the option to "Use wildcard matching" enabled and click OK
10) At top, switch to the "Actions" tab and set the Read Attempt as well as Create, Delete or Write Attempt options to "Block access"

11) Additionally you can set your notification and logging options as needed.
12) Save the policy and assign to a test group to ensure that attempts to install the configured extension are blocked.
Things to consider:
- Test, test and test again. ADC is a very powerful tool, but if configured incorrectly it can ruin your day.
- Keep in mind that pre-existing extensions will not be blocked properly with this policy
- This is meant only to prevent future extension installation.
- Chrome users will be able to disable or delete an extension from within the browser, but the files will be left untouched on the system as ADC won't allow access.
- The extension ID may change when it is updated on the Google Web Store, so you may have to revise or add to the block rule.
- A similar configuration can be used with other browsers, but will require tweaking to the file/folder path and how extensions are identified.