Hello,
This article will demonstrate how to configure liveupdate to run client updates.
Some time customers may get confuse with these settings, they may feel these settings are applicable between SEP client and SEP Manager communication but it's not true.
It's very important to go through the following note which is available at the start of the page.
Important note: Enable the scheduling of automatic downloads from liveupdate servers. The schedule settings do not control downloads from the default management server, from Group Update Providers, or from third party content management tools. Downloads from the default management server depends upon heartbeat interval and selected mode. (Push mode or Pull mode)
1) Enable Liveupdate Scheduling:
-
Click and then click .
-
On the LiveUpdate Settings tab, right-click the policy that you want, and then click .
-
Under Windows Settings, click .
-
Check .
-
Specify the frequency
You can select this option as per business requirement, By default it's set to every 4 hours.

2) Retry Window:

Set the maximum retry allowed after a failed schedule update. If the maximum time is reached before the update has run, the computer will wait for hthe next scheduled time to try again.
If you select any frequency other than , specify the .
3) Download Randomization Option:
If you selected Continuously or Every "XX" hours then this option is grayed out by default.
Check the screen-shot.
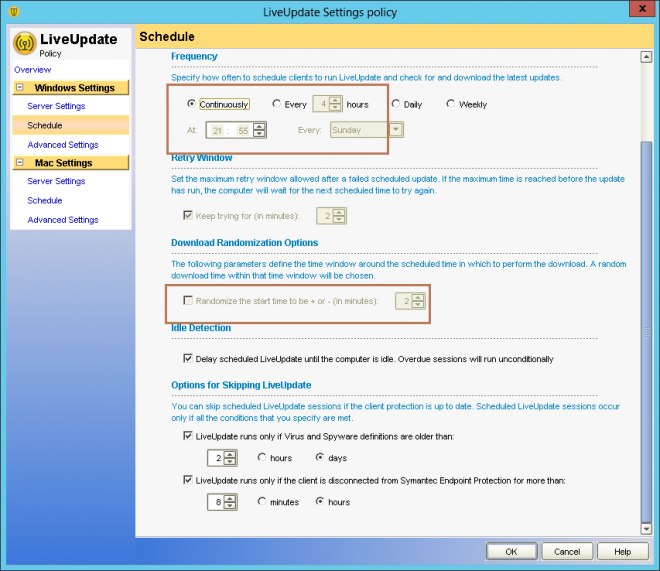
If you selected Daily or Weekly option then you can configure download randomization options.
For Daily you set it to minimum 1 days & maximum 12 days
For Weekly you can set it to minimum 1 days & maximum 3 days

Your network might experience traffic congestion when multiple client computers attempt to download content from a LiveUpdate server. You can configure the update schedule to include a randomization window. Each client computer attempts to download content at a random time that occurs within that window
4. Idle Detection:

To ease client computer performance issues, you can configure content downloads to run when client computers are idle. This setting is on by default. Several criteria, such as user, CPU, and disc actions, are used to determine when the computer is idle.
If Idle Detection is enabled, once an update is due, the following conditions can delay the session.
After one hour, the blocking set is reduced to CPU busy, Disk I/O busy, or no network connection exists. Once the scheduled update is overdue for two hours, as long as a network connection exists, the scheduled LiveUpdate runs regardless of idle status
To configure client updates to run when client computers are idle
To configure client updates to run when client computers are idle.
-
Click.
-
Under Policies, click .
-
On the LiveUpdate Settings tab, right-click the policy that you want to edit, and then click .
-
Under Windows Settings, click .
-
Check .
Reference: http://www.symantec.com/docs/HOWTO55289
5. Options for skipping liveupdate:

To save bandwidth, Symantec Endpoint Protection clients can be configured to only run scheduled LiveUpdates from the Symantec LiveUpdate server if one of the following conditions is met
-
Virus and spyware definitions on a client computer are more than two days old. Maximum duration can be 31 days.
-
A client computer is disconnected from Symantec Endpoint Protection Manager for more than eight hours. Maximum hours can be 24 hours
Following KB's can be helpful as well:
Randomizing content downloads from a LiveUpdate server
http://www.symantec.com/docs/HOWTO55174
Configuring the LiveUpdate download schedule for client computers
http://www.symantec.com/docs/HOWTO55287
Configuring client updates to run when definitions are old or the computer has been disconnected
http://www.symantec.com/docs/HOWTO55293