In order to be able to boot affected machine using the Recovery CD, you need to create first custom Windows PE iso, which can be then burned on CD. Here is the document which describes in details the process of customizing the Windows PE:
How to Customize Windows PE 4.0 and above using Symantec Encryption Desktop 10.3.2 and PGPRecoveryGUI.exe
https://support.symantec.com/en_US/article.HOWTO95227.html
Once machine is booted from that iso, so you see the command-line window with the path "X:\windows\system32", follow the below steps:
1. Run pgpwde --enum in order to check what is the disk number for the encrypted boot drive:

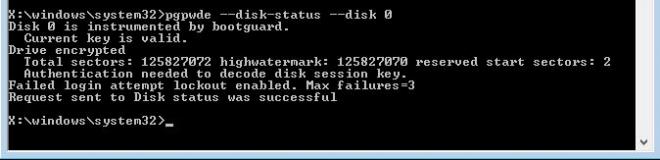
2. Assuming that the affected drive is "0", run pgpwde --disk-status --disk 0 in order to see the status of the disk - is it encrypted, decrypted, instrumented:
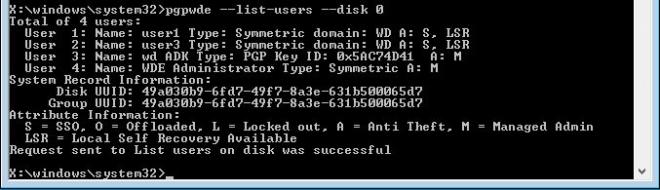
3. Check if there are users assigned to this disk - passphrase for any of that assigned user would be used for the decryption:
4. Next command to run is the decryption command: pgpwde --decrypt --disk 0 --interactive. Once this is executed, you will be prompted for passphrase. Once the correct is inserted, the decryption process will start:

It might happen, that the error will be displayed after executing the decrypt command (for example, if wrong passphrase was specified). It is possible to check if the known passphrases are correct. To do that, command pgpwde --auth --disk 0 --interactive needs to be executed. In the screenshot there were 2 attempts - the first one was incorrect password (error -11500), and the second was the correct one, so it can be used for decryption:

5. In order to see the decryption status, the command from step 2 needs to be run periodically. The value next to "lowwatermark" indicates how many sectors have been decrypted so far, while "highwatermark" specifies how many sectors were originally encrypted. You will notice that "lowwatermark" will be higher each time the command is executed:

6. It is possible to use also Whole Disk Recovery Token (WDRT) to decrypt the drive. It is done by running the following command, assuming that "1QAZ2-WSX3E..." is the token value: pgpwde --decrypt --disk 1 --recovery-token "1QAZ2-WSX3E-DC4RF-V5TGB-6YHN7-UJM" --aa Token can be taken from the Symantec Encryption Management Server (SEMS) console in case of managed Symantec Encryption Desktop (SED). In case of unmanaged SED, the WDRT token is generated when the encryption starts and is displayed in the window so end users are prompt to save it in a secure place.