|
Larry Lieberman is a busy guy. He's been on the city council of University City, Missouri for decades, and he's always been extremely responsive to his constituents. But email has really changed his life. Instead of writing letters or calling, nowadays his constituents send him email - a lot of email. Every day, his inbox fills with questions, praise, complaints, and requests, and Larry answers it all using his email client of choice - Microsoft Outlook.
But then one day Larry got the virus.
He knows it was his fault: "I was so busy that week, and I just didn't realize that my anti-virus subscription was expiring. I didn't know I had a problem until I started getting email from people telling me that I had sent them a virus. It was embarrassing." It turns out that Larry's anti-virus subscription had expired on Tuesday. By Thursday, he was infected with the W32.Badtrans.B@mm worm.
Fortunately, that virus isn't as serious as many. Instead of erasing his hard drive or damaging data, it sent copies of itself to other people in his address book (although it was supposed to install a keylogger, subsequent examination turned up negative). Still, it was a wake-up call for Larry. Besides updating his anti-virus software, he also asked a consultant to harden his Outlook installation in order to prevent any future security lapses.
Larry's story is not unique. Millions of Outlook users around the world, in homes, organizations, and businesses, have had to face the insecurities inherent in their email program, sometimes painfully. In fact, SecurityFocus reports that there were nineteen security vulnerabilities reported for Outlook 2000 over the last three years (there have been nine reported for Outlook 2002 in just the past year). Fortunately, there are many things they can do to protect themselves. The important thing is to be proactive instead of reactive. If Outlook users do nothing, they will face the consequences - it's just a matter of time.
This article is the first part of a two-part series that will help readers to secure their Outlook email clients. This installment will offer a brief overview of Outlook, as well as a guide to configuring it securely.
Many Different Outlooks
It's important to understand that Microsoft has released many versions of Outlook, which makes it more difficult for you to take precautions. You can verify which version you're using by selecting the Help menu and then choosing "About Outlook".
There have been four major versions of Outlook:
- 97 - the first one, included with Office 97
- 98 - a free upgrade to correct the deficiencies of 97
- 2000 - bundled with Office 2000
- 2002 - found in Office XP.
Outlook 97/98/2000 must be run in one of two modes: Internet Mail Only (IMO) or Corporate Workgroup (CW). Use CW if you connect to a Microsoft Exchange server for email, calendaring, and shared contacts, and IMO if you just want to use the standard email protocols like POP, SMTP, and IMAP (to make things really confusing, note that an IMO-configured Outlook can still connect to an Exchange server, just without all the shared features, while a CW-configured Outlook can also use standard email protocols like POP and SMTP, but not IMAP). Note that this division between CW and IMO was removed in Outlook 2002; however, along with that removal went several other useful features.
That makes a total of seven versions of Outlook, each with its own features and peccadilloes! And apparently Microsoft is planning a complete overhaul of Outlook's interface and functionality for the next release of Office, slated for sometime in 2003, which would bring us up to eight different Outlooks.
It would take a lot of words to cover the ins and outs of security for all these different versions. In writing this article, I used Outlook 2000, so all screenshots and instructions will focus on that release. My counsel will help all users of Outlook, no matter what version they use. Still, some of the advice offered here may not apply to you, or it may need to be changed slightly to work with your particular installation of Outlook. Prepare to be flexible.
Configuring Outlook Correctly
The first and most obvious thing a user can do is to set Outlook's preferences in ways that make sense for security. To get started, open Outlook, select the "Tools" menu, and then choose "Options". In the Options window that is now open, select the "Security" tab:
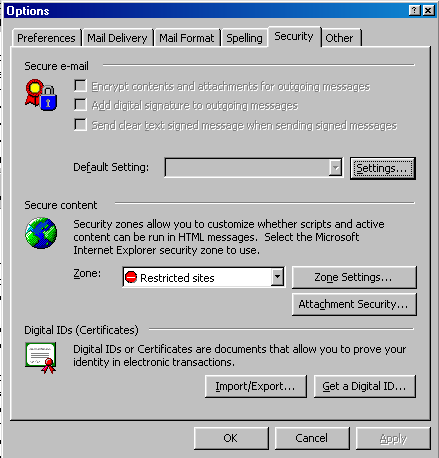
Figure 1: Select the "Security" tab in the Options window.
Before we go any further, we need to briefly cover a few terms that will occur throughout this article. "Plugins" are small software programs that enable your Web browser and email client to view special content, like sounds, animations, and movies. To use a plugin, you must first download and install it. Macromedia's Flash, which allows you to view animated movies and images, is one of the most common plugins on the Internet.
"Scripts" are small programs, typically written in JavaScript or VBScript, that run in your Web browser or email client and allow programmers to change the functionality of those programs. For example, if you've ever filled out a form and pressed "Submit", only to have a small box pop up warning you that you neglected to fill in your email address, then you probably just interacted with some JavaScript.
"Cookies" are small text files that track the Web sites you visit and the emails you read. Some cookies are necessary: if you enjoy being able to log in to The New York Times Web site without having to enter your username and password every single time, then you have cookies to thank. However, as has been well documented, they can be misused by over-eager marketers and spammers.
"ActiveX controls" are basically small programs that are just like any other Windows program, except that they work over the Internet. This means that ActiveX controls can do very nasty things to your computer if you're not careful. For instance, it is quite possible to install and run an ActiveX control that will erase important data, or capture sensitive information and post it to some bad guy somewhere. Microsoft's security model for ActiveX controls involves "signing", which means that the author of an ActiveX control verifies that he is who he says he is. If you agree to allow signed ActiveX controls to install and run on your computer, then any control that states that it is authentic can run. The problems with this sort of "trust me" security should be obvious. Just to complicate things, Microsoft now forces all plugins written for Internet Explorer 6, which Outlook uses to view HTML email, to use ActiveX as their delivery mechanism.
Finally, "Java applets" are programs designed to run inside a Java Virtual Machine (JVM) on your computer. If you don't have Java installed, then you can't run Java applets. The JVM is more secure than ActiveX because it only allows programs to run inside a sandbox that restricts what they can do while preventing them from accessing key system resources. Microsoft is not very fond of Java, as it was created and is overseen by Sun, a bitter rival. So Microsoft has done all it can to demote Java while promoting its own ActiveX technology.
Got all that? Good. Now back to configuring Outlook.
Secure Content
On the "Security tab" of the Options window, take a look at the middle section, "Secure content". This is an important configuration, as it controls what your email program does with content that can cause problems, such as ActiveX controls, plugins, cookies, and scripts. First, change your zone to "Restricted sites".

Figure 2: Set zone to "Restricted sites"
Leaving your zone set to "Internet" is just too permissive, as it still allows you to run ActiveX controls and plugins while letting scripting operate indiscriminately. On the other hand, setting it to "Restricted sites" doesn't fix everything, as Microsoft's definition of restricted sites continues to leave the system wide open to ActiveX controls and scripting. You still need to customize your settings, so select the "Zone Settings ..." button. You will now see a dialog box warning that any changes you make are going to affect not just Outlook, but also Internet Explorer and Outlook Express. Due to the way in which Microsoft ties together all of its programs, changes made in one program may have ramifications for other programs. That's okay in this instance, as you really should batten down the hatches in all of your Microsoft-provided Internet programs.
After choosing "OK", you will be presented with the Security window, which lists the various "zones" along the top. Choose "Restricted sites" and then select the "Custom Level ..." button.
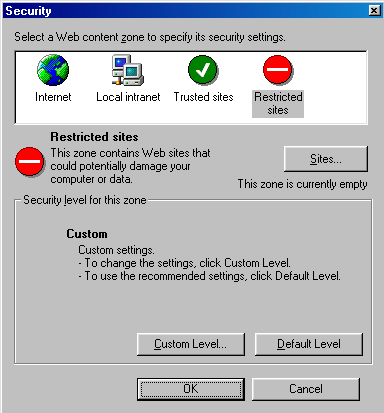
Figure 3: Security zones with "Restricted sites" chosen.
Once the "Security Settings" window is open, I recommend setting everything to "Disable", except the following, which you should set to "Prompt":
- Script ActiveX controls marked safe for scripting - You need to be very careful here. As stated above, whether or not an ActiveX control is safe for scripting is determined by the author of the control. As a result of setting this preference, viewing an email with an ActiveX control in it will result in a popup window opening up to ask you if you wish to install the control. Read this window carefully! If there is a good reason to install the control, then do so. If not, don't. I would err on the side of caution.
- Font download - Fonts are generally safe, so there isn't much to worry about here, but it's good to know if a site or email wants to install one. Obviously, if you can't read Chinese, you probably shouldn't bother installing a Chinese font package.
- Display mixed content - Mixed content occurs when a Web page uses both secure (https) and insecure (http) content. Again, this preference is mostly for informative reasons. If an email contains content coming from both secure and insecure sites, you should ask yourself why that is. And if the email contains a form that says that it is secure, setting this to "Prompt" will let you know that you could be sending data in a non-secure form as well.
- Drag and drop or copy and paste files - This refers to the ability of user to grab files that exist inside of Web pages and HTML-based email and either drag or paste them onto your computer. Needless to say, this is a fantastic way to spread viruses and other malicious content.
- Submit nonencrypted form data - This preference controls whether you can submit a form using only http instead of https. Some HTML emails have forms in them. If the form contains sensitive data, it should be submitted using the secure https instead of the insecure http. By setting this preference to "Prompt", you will be notified if the form is insecure.
In addition, make sure that the "Software channel permissions" are set to "High safety", and "Logon" is set to "Prompt for user name and password". The "Software channel permissions" setting governs the automatic downloading of software from "channels", or subscription-based Web sites. Microsoft has pretty much abandoned this idea, so you don't need to worry too much about this anymore, but by setting the permission to "High safety" you will exercise as much control as you can over any such downloads. The "Logon" setting affects how your computer authenticates you with sites that require a username and password. Other settings don't give you fine-grained control when logging in, in some cases automatically logging you in with the name and password you use to sign in to Windows. By changing this setting to "Prompt", you will always be asked to enter a username and password.
Once you're finished securing everything, select "OK" to close the window, and then choose "OK" to close the Security window.
You should now be back on the Options window. Now select the "Attachment Security ..." button. When that Window opens, choose the "High" option. This warns you if any attachment will present a security issue.

Figure 4: The "Attachment Security" window
Note that the "Attachment Security..." button only appears in versions of Outlook prior to Outlook 2002. With Outlook 2002, Microsoft changed how attachments are handled, so the user no longer gets that choice.
Next Time...
Well, we've configured Outlook, but there's plenty more to come. Join me for the second part of this article in a few weeks, when we continue our quest to make Outlook secure.
Scott Granneman is a senior consultant for Bryan Consulting Inc. in St. Louis. He specializes in Internet Services and developing Web applications for corporate, educational, and institutional clients.
|