|
This is the fourth and final installment in a series devoted to protecting users' privacy on the Internet. So far in this series, we've examined privacy issues concerning hardware, software, and e-mail. In this article, we will look more generally at our usage of the Internet. The Internet offers all of us unparalleled access to information, but it also brings with it unique threats to our privacy. This article will examine some of the ways you can protect yourself.
Web Browser Settings
The Web browser is a tool many people use without ever really thinking about how it can reveal information about them. In the previous article in this series, I discussed several features of your browser that you should use to protect your personal information. However, there are a few more that bear examining.
If you use Internet Explorer version 5 or above, you should think about whether or not you wish to enable the AutoComplete feature. Autocomplete allows IE to remember previous entries you've made for Web addresses, forms, and even passwords. When you start to re-enter the same information on subsequent visits, the Autocomplete feature will offer the complete text, thus saving you the trouble of typing out text repeatedly. This undoubtedly makes using IE easier; unfortunately, anyone sitting down at your computer will be able to easily see where you've been on the Web and, worse yet, impersonate you at Web sites that require you to input information. While some people find the convenience worth the obvious risk, it's a tradeoff you need to weigh carefully.
If you want to disable AutoComplete, you need to go to two places. First of all, open IE and select the Tools menu, then choose "Internet Options ..." and the "Advanced" tab. Scroll down and uncheck the box next to "Use inline AutoComplete for Web addresses".
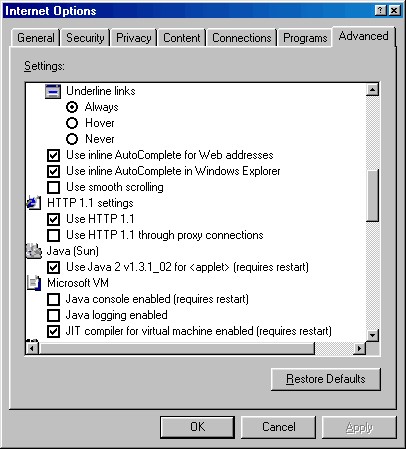
Fig. 1: Inline Autocomplete for Web addresses
Next, without closing the "Internet Options ..." dialog box, select the "Content" tab and then the "AutoComplete ..." button. Here you check or uncheck the boxes next to the items you want AutoComplete to remember: "Web addresses", "Forms", and "User names and passwords on forms". If you decide to check next to "User names and passwords on forms", make sure you also check "Prompt me to save passwords" so you can tailor your choices for each Web site. Click "OK" to close the dialog box, and you're done.

Fig. 2: Choices for Autocomplete
The other Web browser with substantial market share is Netscape and the open source wunderkind it's based upon, Mozilla. Netscape 6.2 , like Internet Explorer, will store your passwords if you'd like. Simply open Netscape and select the Edit menu, choose "Preferences ...", then "Privacy & Security", and "Passwords". Check or uncheck the box next to "Remember passwords", depending upon your certainty that your machine is secured. If you decide to enable "Remember passwords", make sure that you also check "Use encryption when storing sensitive data" in order to prevent snoopers from accessing your Netscape files, thereby gaining the keys to the kingdom. Furthermore, make sure you use a good password, which will be discussed below.

Fig. 3: Mozilla/Netscape password preferences
Privacy policies
The combination of the tips given in the previous articles and the advice given above will go a long way to securing your privacy while using your Web browser; however, there are still Internet privacy issues that users should be aware of, such as privacy policies. Privacy policies are statements made by the owners of the Web site stating what will and will not be done with the personal information that users disclose when visiting that site.
If you want to reduce the amount of your personal information that is sold to on-line advertisers - if you want, in other words, to lessen the data that marketers gather about you - you need to read the privacy policies on the Web sites you visit. I know this is tedious. I know many of them are written in a way that normal human beings don't write. But it is vital, nonetheless.
You also need to read the news at Wired, CNET, and other places in order to keep up with the changes companies make in their privacy policies. Businesses have a nasty habit of "revising" their policies in a way that benefit them at the expense of their users.
Some Examples of Changing Policies
For instance, AOL pulled a fast one in November 1999. In early 1998, AOL unveiled sweeping policies designed to preserve the privacy of its users. Among the options detailed in the new policy was the ability for users to opt-out of direct marketing pitches from AOL's partners, whether delivered via the Web, e-mail, postal mail, or telephone. Eighteen months later, AOL sent a mass e-mail to its users informing them that their "marketing preferences" were not permanent, as might be expected, but would instead expire in a few weeks. If a user wanted to block the junk, he would have stipulate this preference every year. If a user doesn't get around to resetting preferences every year, then his settings are automatically set to "Yes", as in: "Yes, please send me as much junk mail and telemarketer calls as possible".
eBay has also engaged in this sort of chicanery. In January 2001, eBay sent e-mails to thousands of customers, informing them of a newly discovered bug. When someone registers with eBay as a buyer or seller, she has to fill out several screens of information. One of those screens concerns whether the new eBay customer wants to receive e-mail and telephone offers from eBay and its partners. The series of questions are supposed to default to "Yes"; however, the bug eBay discovered had caused the default to set to "No". Apparently panicked that some people were missing out on junk mail and telemarketing calls, eBay helpfully reset users' settings to "Yes" and then sent the e-mails giving people two weeks to change their settings.
Most recently, Yahoo has been embroiled in controversy since it "revised" its privacy policy. In late March, Yahoo sent e-mails to the millions of people who had registered to receive one service or another. At the time they registered, users were asked once to state if they wished to accept or reject marketing offers from Yahoo and related companies. Now, the e-mails stated, users would have to choose "Yes" or "No" to a range of questions and offers. Further, Yahoo had set every user's preferences to "Yes", even if a user had previously said "No". Users would have sixty days to change their preferences before the deluge of spam would begin. Finally, Yahoo reserved the right to add additional marketing offers at any time in the future, and those would also default to "Yes".
If you are registered with Yahoo and would like to change your "marketing preferences", head over to Yahoo's Profile Center and log in with your Yahoo username and password. Select "Edit your marketing preferences" from the "Member Information" section and then make your choices. "No" to everything is proving to be a common preference.
Don't trust TRUSTe
Remember, just because a site has a privacy policy doesn't mean that the policy is in your best interest. Similarly, another "assurance" to take with a grain of salt is the TRUSTe seal. TRUSTe is a nonprofit company whose seal is supposed to ensure that a company clearly states a privacy policy and lives by the principles set in that policy. Unfortunately, TRUSTe is a paper tiger. Dependent upon the fees it receives from companies it audits, and lacking any enforcement mechanism or ability to set a penalty on violators, TRUSTe time and time again has done nothing when its clients do things that are damaging to the privacy of their users. The proof? Go to the privacy policy pages at AOL, eBay, and Yahoo. What unifies them? A TRUSTe seal of approval. Still have faith in TRUSTe?
Use Secure Passwords
The final key aspect to keeping privacy secure on the Internet involves the method we use to identify ourselves: passwords. A poor password is an invitation to a buffet of your personal information. Unfortunately, the vast majority of people not only issue an invitation, they hand deliver it and request an RSVP.
A recent study conducted in Britain found that 50% of computer users use the name of a family member, significant other, or pet in coming up with a password, and another 30% use the name of someone in music, movies, or sports. Another 10% tend to pick words having to do with fantasies, often sexual in nature. That leaves about 10% of users who choose a cryptic and, therefore, hard to crack password.
Since this poor pattern of password construction is well known, a cracker may require very little information about a person's life and habits before he can begin trying to get into a user's Internet accounts, e-mail, bank accounts, and so on. For instance, given a group of people who live in St. Louis and love baseball, you can be sure that several of them will have "Cardinals" as a password.
There's a simple solution to this problem. First, never leave your password set to the default that was assigned to you. It's shocking how many people get a new account on a computer network and never bother to change their password from the one given to them - and too often that default is "password".
Second, and this bears repeating over and over, choose a good password. Don't use your name - even backwards. Don't use your dog's name. Don't use your husband's name. Don't use the kind of car you drive. And so on.
Here's a couple of hard and fast rules for what not to use:
- Anything found in a dictionary. Not even words joined together, like "bigredtruck".
- Anything found in a foreign dictionary, unless it is a language spoken by fewer than 250 people worldwide.
- Anything that consists only of numbers. With modern password cracking tools, "7639" is just not a hard password to crack. You weren't going to use your banking PIN, were you? Never!
Principles of Good Passwords
There are two principles that you need to apply in coming up with a good password. Number one, it should include a mixture of capital letters, small letters, numbers, and symbols. And number two, it should be easy to remember, but hard to guess. For instance, the password "&y5#@LNa0" meets the first principle, but not the second (at least for me ... maybe that combination means something to you). On the other hand, "Marian" - the name of a relative who died in infancy back in the 1930s - satisfies principle two, since it's easy for me to call up that name in my mind, and few people outside of my immediate family know of this bit of genealogy, but it dismally fails principle one (by the way, I don't actually use "Marian" as a password, so don't bother trying it against me).
How to Create a Good Password
But here's a handy way to combine the two principles together to form a great password. Take a favorite song that means something to you. Let's use as an example the great Elvis Presley song "Suspicious Minds". The first line is "We're caught in a trap, I can't walk out". Take the first letter of each word, and you have "Wciat,Icwo". Now think of a date that means something to you. I'll use the year my parents were married, 1957. Add the digits to your password-in-development, and you get "19Wciat,Icwo57". That's a good password!
"19Wciat,Icwo57" is a good password because it has a mixture of capital and small letters, numbers, and symbols. If you want to add more symbols, use parentheses, like this: "(19Wciat,Icwo57)". This password is impossible to guess, but it's actually very easy to remember. I know the first line of "Suspicious Minds" by heart, and I certainly know the year my parents got married. As long as I can remember what I need to remember - the first line of a song and a date - I can recall my password. And let me assure you, after you've typed this password a dozen times or so, your muscle memory will kick in and you'll find it even easier to use.
If you really want to make it easy to remember your new and effective password, print out the lyrics to "Suspicious Minds" and hang them in your cubicle, next to your other poems and pictures. If anyone sees them, they'll think you're an Elvis fan. If someone bent on mischief happened to see the lyrics posted in your cubicle, he might try out "Elvis" and "SuspiciousMinds" and "Graceland" in his quest to guess your password. But unless he's read this very article and knows that you have sworn to live your life by its principles, he would never guess that you had taken the first letter of each word in the first line and used that as the basis for your password. (For a more in-depth look at developing strong passwords, please see the SecurityFocus article The Simplest Security: A Guide To Better Password Practices.)
Guard Against Social Engineering
One final word about passwords: guard them vigilantly. Do not give them out to anyone. A common hacking technique is that of social engineering. It's common because it is so amazingly effective. Basically, a cracker calls the unsuspecting computer user on the telephone, and a conversation similar to the following ensues:
Bad guy: "Hi, is this Denise?"
Denise: "Yup, that's me!"
Bad guy: "Denise, this is Joe at your ISP. We've calling all of our customers to verify the information we have for their accounts. In particular, we need your username and password. Can you go ahead and give them to me?"
Denise: "Sure! My username is "denise" and my password is "1234". I hope that helps you out!"
Bad guy: "It sure does. Thanks, Denise. I appreciate it."
Within half an hour, the cracker has started making Denise's life a living hell.
You might think that the preceding exchange is a joke; unfortunately, it's not. Recently, the Milwaukee Journal-Sentinel reported that a 16-year-old boy used a program he found on the Internet to send bogus e-mails to AOL users telling them that their billing information had been deleted, and that they needed to provide their credit card information at a Web site set up by the company. Needless to say, the boy had created the Web site, which was in no way affiliated with AOL. Over 200 people fell for the scam, netting the boy between 10 and 15 credit card numbers each day, which he used to purchase over $1500 worth of stuff, including a DVD player, athletic shoes, computer equipment, and a marijuana bong, or water pipe.
When arrested, the boy told police that he got away with it because people are "dumb". Further, he asserted that "They should thank me" because "I was teaching them a lesson". I'll let you decide the truth of his statements. But if a stoner kid barely able to drive can bilk a couple of hundred people out of their credit card numbers, that should tell you something.
Conclusion
Over the course of this series, we've covered a lot of information. Sometimes it might seem overwhelming trying to plug all the holes in the dike surrounding our privacy. Each of us, however, has to decide just what we consider sacrosanct and what we consider expendable. I hope that the information presented in this series has helped you realize the threats that are out there, and given you some solutions and counterbalances to those threats. Education is the key to defending against such threats, so it is my sincere hope that you've gained some modicum of knowledge from these articles that will help you in your fight to protect your privacy.
|