Welcome to the Part 3 out of 3 discussing the terms, technologies and concepts related to Symantec Endpoint Protection and Symantec Security Software. In the series you will find description and explanation of several SEP related technologies, tools and concepts alongside of the relevant links to Symantec KB articles. The terminology articles are based upon the available official documentations and publications from Symantec KBs and Implementation Guides for SEP. Any comments or ideas what should be included in the series are welcome. I hope this series will be informative to you.
The Series consists of following articles:
Symantec Endpoint Protection Terminology Guide - Concepts, Technologies, Terms - Part 1 (A-G)
Symantec Endpoint Protection Terminology Guide - Concepts, Technologies, Terms - Part 2 (H-R)
Symantec Endpoint Protection Terminology Guide - Concepts, Technologies, Terms - Part 3 (S-Z)
This is the third part of the series concerning the following terms:
SAV for Linux (SAVFL) - software designed to provide Antivirus protection on Linux OS. Symantec AntiVirus for Linux includes real-time antivirus file protection
through Auto-Protect scanning, and file system scanning via manual and scheduled scans. Symantec AntiVirus for Linux requires a specific kernel on the system before installing Symantec AutoProtect package or otherwise you should compile your own kernel with our AutoProtect to ensure it will function properly
Best practice to install Symantec Antivirus for Linux
http://www.symantec.com/docs/TECH150596
System requirements for Symantec AntiVirus for Linux 1.0
http://www.symantec.com/docs/TECH101598
SAV for Linux Scanning Best Practices: A (Somewhat) Illustrated Guide
https://www-secure.symantec.com/connect/articles/sav-linux-scanning-best-practices-somewhat-illustrated-guide
SAV for Linux: A (Somewhat) Illustrated Guide Part 2
https://www-secure.symantec.com/connect/articles/sav-linux-somewhat-illustrated-guide-part-2
SAV for Linux: A (Somewhat) Illustrated Guide Part 3
https://www-secure.symantec.com/connect/articles/sav-linux-somewhat-illustrated-guide-part-3
SAVFL Reporter - provides log records and inventory information to the Symantec Endpoint Protection Manager via its legacy reporting channel. This allows you to monitor and report on SAVFL client activities from the Symantec Endpoint Protection Manager console. Important note is that installing SAVFL and SAVFL Reporter will not cause the Linux machines to be displayed on the SEPM's clients tab.
Symantec AntiVirus for Linux (SAVFL) Reporter 1.0.10 Release Notes
http://www.symantec.com/docs/DOC3474
SAV for Linux: A (Somewhat) Illustrated Guide Part 4: SAVFL Reporter
https://www-secure.symantec.com/connect/articles/sav-linux-somewhat-illustrated-guide-part-4-savfl-reporter
How to enable the 12.1 Symantec Endpoint Protection Manager (SEPM) to receive logging from legacy clients
http://www.symantec.com/docs/TECH157463
Security Virtual Appliance (SVA) - is a Linux-based virtual appliance that you install on a VMware ESX/ESXi server. The Security Virtual Appliance integrates with VMware's vShield Endpoint. The Shared Insight Cache runs in the appliance and lets Windows-based Guest Virtual Machines (GVMs) share scan results. Identical files are trusted and therefore skipped across all of the GVMs on the ESX/ESXi host. Shared Insight Cache improves full scan performance by reducing disk I/O and CPU usage.
About the Symantec Endpoint Protection Security Virtual Appliance
http://www.symantec.com/docs/HOWTO81080
VMware software requirements to install a Symantec Security Virtual Appliance
http://www.symantec.com/docs/HOWTO81081
Installing a Symantec Endpoint Protection Security Virtual Appliance
http://www.symantec.com/docs/HOWTO81083
Configuring the Symantec Endpoint Protection Security Virtual Appliance installation settings file
http://www.symantec.com/docs/HOWTO81082
SEP Support Tool (SST) - is a utility designed to diagnose common issues encountered with Endpoint Protection and the Endpoint Protection Manager. The tool can be used as well to proactively to ensure that the target machine is ready to install the Endpoint Protection manager or client. This is an older version of a troubleshooting tool (designed mainly for SEP 11.x), currently replaced by Symhelp tool.

The Symantec Endpoint Protection Support Tool
http://www.symantec.com/docs/TECH105414
SEPprep - is a unsupported tool that is designed to uninstall any competitive product automatically. This tool can also launch another application before or after removing all competitive products. Therefore you can configure this tool to first remove all competitive products (including Norton products) and then launch the SEP installer automatically and silently.
SEPprep competitive product uninstall tool
http://www.symantec.com/docs/TECH148513
SERT - Symantec Endpoint Recovery Tool - is a bootable CD utility that can scan and remove malware from an infected computer. SERT is useful in situations where computers are too heavily infected for the Symantec Endpoint Protection client installed upon them to clean effectively. It is also necessary against specific threats which have the ability to completely hide from Windows.

How To Use the Symantec Endpoint Recovery Tool with the Latest Virus Definitions
http://www.symantec.com/docs/TECH131732
Symantec Endpoint Recovery Tool (SERT)
https://www-secure.symantec.com/connect/videos/symantec-endpoint-recovery-tool-sert
Symantec Endpoint Recovery Tool (SERT)
https://www-secure.symantec.com/connect/articles/symantec-endpoint-recovery-tool-sert
How to make the Symantec Endpoint Recovery Tool boot from a USB memory stick
http://www.symantec.com/docs/TECH131578
Shared Insight Cache (SIC) - the tool improves scan performance in virtualized environments by not scanning files that a Symantec Endpoint Protection client has determined are clean. When the client scans a file for threats and determines it is clean, the client submits information about the file to Shared Insight Cache. When any another client subsequently attempts to scan the same file, that client can query Shared Insight Cache to determine if the file is clean. If the file is clean, the client does not scan that particular file. If the file is not clean, the client scans the file for viruses and submits those results to Shared Insight Cache.

About the Symantec Endpoint Protection Shared Insight Cache tool
http://www.symantec.com/docs/HOWTO55311
How Shared Insight Cache works
http://www.symantec.com/docs/HOWTO55318
Network-based Shared Insight Cache - Best Practices and Sizing guide
http://www.symantec.com/docs/TECH174123
Installation and Configuration of SEP Shared Insight Cache
http://www.symantec.com/docs/TECH185897
Smart DHCP - A smart traffic filtering option that allows a Dynamic Host Configuration Protocol (DHCP) client to receive an IP address from a DHCP server while protecting the client against DHCP attacks from a network. If a Symantec Protection Agent sends a DHCP request to a DHCP server, it waits for five seconds to allow for an incoming DHCP response. If a Symantec Protection Agent does not send a DHCP request to a DHCP server, then Smart DHCP does not allow the packet. Smart DHCP does not block packets. It simply allows the packet if a DHCP request was made. Any other DHCP blocking or allowing is done by the normal security rule set. See also Dynamic Host Configuration Protocol (DHCP).
SEP Client Firewall Rules Policies (Network Threat Protection/NTP) for finding clients using non-approved DHCP/DNS servers
http://www.symantec.com/docs/TECH161639
Smart DNS - A smart traffic filtering option that allows a Domain Name System (DNS) client to resolve a domain name from a DNS server while providing protection against DNS attacks from the network. This option blocks all Domain Name System (DNS) traffic except outgoing DNS requests and the corresponding reply. If a client computer sends a DNS request and another computer responds within five seconds, the communication is allowed. All other DNS packets are dropped. Smart DNS does not block any packets; blocking is done by the normal security rule set.
SEP Client Firewall Rules Policies (Network Threat Protection/NTP) for finding clients using non-approved DHCP/DNS servers
http://www.symantec.com/docs/TECH161639
SONAR - is a real-time protection that detects potentially malicious applications when they run on your computers. SONAR provides "zero-day" protection because it detects threats before traditional virus and spyware detection definitions have been created to address the threats. SONAR uses heuristics as well as reputation data to detect emerging and unknown threats. SONAR provides an additional level of protection on your client computers and complements your existing Virus and Spyware Protection, intrusion prevention, and firewall protection. SONAR replaces the Truscan heuristic protection from SEP 11.x Version.

About SONAR
http://www.symantec.com/docs/HOWTO81392
Managing SONAR
http://www.symantec.com/docs/HOWTO81373
Sylink Monitor - is a utility that provides an alternative to manual enabling of sylink debugging on SEP clients. Currently the use if the tool is no longer recommended as the same type of logging with even more configuration options may be collected with SymHelp tool.
How to enable Sylink debugging for the Symantec Endpoint Protection 11.x and 12.1 client in the Windows Registry
http://www.symantec.com/docs/TECH104758
SylinkDrop - tool used for replacing the communication settings (sylink.xml file) on SEP clients. Available versions for PC and Macintosh. Another tool that may be used to achieve the same goal would be Sylink Replacer or push of the communication settings directly from SEPM to the client machines.
SylinkDrop or SylinkReplacer fails to assign Symantec Endpoint Protection clients to a new Client Group
http://www.symantec.com/docs/TECH103041
Recovering client communication settings by using the SylinkDrop tool
http://www.symantec.com/docs/HOWTO55428
Sylink Replacer - an utility designed to replace Sylink.xml files in existing Symantec Endpoint Protection (SEP) clients. Utility provides a much more automated and scalable solution for replacing communication settings in comparison to Sylink Drop. Currently if possible (only SEPM 12.1 RU2 and higher) it is recommended to use Communication Update Package Deployment from SEPM instead of Sylink Replacer.
Using the "SylinkReplacer" Utility
http://www.symantec.com/docs/TECH105211
The Sylinkreplacer tool for connecting SEP clients to a SEPM
https://www-secure.symantec.com/connect/downloads/sylinkreplacer-tool-connecting-sep-clients-sepm
Symantec Antivirus Corporate Edition (CE) 10.x - legacy Symantec Antivirus solution. Product reached its End-of-Support-Life (EOSL) on July 4, 2012 and was replaced by newer SEP 11.x and SEP 12.1 software solutions. Depending on the version old legacy SAV CE may be directly upgraded either to SEP 11.x or 12.1 - please consult relevant migration documentation for supported upgrade paths.
End of Life announcement for Symantec AntiVirus Corporate Edition and Symantec Client Security
http://www.symantec.com/docs/TECH178551
Frequently asked questions about Symantec AntiVirus 10.x End of Support Life
http://www.symantec.com/docs/TECH184999
How to request a virus definition extension for Symantec AntiVirus 10.x Corporate Edition beyond its End-of-Support-Life date
http://www.symantec.com/docs/HOWTO73168
Symantec Endpoint Protection Enterprise Edition 11.x / 12.1 - Symantec Endpoint Protection is a client-server solution that protects laptops, desktops, Mac computers, and servers in your network against malware such as viruses, worms, Trojan horses, spyware, and adware. Additionally it is able to provide protection against even the more sophisticated attacks that evade traditional security measures such as rootkits and zero-day attacks.
The suite comprises of Antivirus / Antimalware protection, Firewall, IPS and Application and Device Control. In 12.1 version SEP is built on multiple additional layers of protection, including Symantec Insight and SONAR both of which provide protection against new and unknown threats. For more information about the respective SEP features please look up the specific terms in this series of articles.
The most recent SEP 12.1 version is 12.1 RU3. Latest version of Symantec Endpoint Protection 11.x is 11 RU7 MP3 - please note that the next (and at the same time the last SEP 11.x version in the series) will be SEP 11 RU7 MP4 - after this release SEP 11.x will reach End of Support on 2014-09-27.

Symantec Endpoint Protection
http://www.symantec.com/endpoint-protection
Release Notes and System Requirements for all versions of Symantec Endpoint Protection and Symantec Network Access Control
http://www.symantec.com/docs/TECH163829
Symantec™ Endpoint Protection, Symantec Endpoint Protection Small Business Edition, and Symantec Network Access Control 12.1.3 Release Notes
http://www.symantec.com/docs/DOC6549
New fixes and features in Symantec Endpoint Protection 12.1.3
http://www.symantec.com/docs/TECH206828
What's new with Latest Symantec Endpoint Protection SEP 12.1.RU3
https://www-secure.symantec.com/connect/blogs/whats-new-latest-symantec-endpoint-protection-sep-121ru3
Latest Symantec Endpoint Protection Released - SEP 12.1.RU3
https://www-secure.symantec.com/connect/forums/latest-symantec-endpoint-protection-released-sep-121ru3
Upgrading or migrating to Symantec Endpoint Protection 12.1.3 (RU3)
http://www.symantec.com/docs/TECH206823
Symantec Endpoint Protection Manager - centralized management console for Symantec Endpoint Protection Clients. From within the SEPM Manager it is possible to distribute settings, policies, content and product updates to the managed SEP clients. It allows for detailed logging and reporting collected from all managed clients. The manager can be accessed either locally through java-based console or remotely via web-based console or remote java-based console. To note is that the local java-based console does not require separate Java installation as it is already integrated with the manager. SEPM uses by default an integrated embedded database, but if configured it can take avail of a remote SQL Server Database. From the advanced SEPM installation / configuration options it is supported to use several SEPM Servers in Replication, Failover or Load-Balancing modes. It is recommended to review the sizing and scalability best practices before installing SEPM as it has certain installation and later on space and bandwith requirements.

Installing Symantec Endpoint Protection Manager
http://www.symantec.com/docs/HOWTO80785
Upgrading or migrating to Symantec Endpoint Protection 12.1.3 (RU3)
http://www.symantec.com/docs/TECH206823
How to install the Symantec Endpoint Protection Manager(s) for replication
http://www.symantec.com/docs/TECH105928
Symantec Endpoint Protection Sizing and Scalability Best Practices White Paper
http://www.symantec.com/docs/DOC4448
Symantec Endpoint Protection 12.1: Best Practices for Disaster Recovery with the Symantec Endpoint Protection Manager
http://www.symantec.com/docs/TECH160736
How to move Symantec Endpoint Protection Manager 12.1 from one machine to another
http://www.symantec.com/docs/TECH171767
Symantec Endpoint Protection SBE 12.1 - Symantec Endpoint Protection Small Business Edition incorporates many of the features from Symantec Endpoint Protection Enterprise Edition. It is designed for small-to-medium businesses with up to 250 clients. Same as the full version the SBE protects against malware such as viruses, worms, Trojan horses, spyware, and adware. Please review the release and implementation documentation about SBE version as several of the features and functionalities included natively in 12.1 EE may be missing in 12.1 SBE edition. From the most importart differences to mention:
■ no SQL Database support
■ no Application and Device Control feature
■ no Host Integrity enforcement
■ no Shared Insight Cache support
■ no AD Synchronisation option
■ does not include several other components such as Risk Tracer, Virtual Image Exception, Group Update Providers
■ includes some limitations regarding the available management options in the SEPM GUI
Feature comparison between SEP 12.1 SBE and EE
https://www-secure.symantec.com/connect/articles/feature-comparison-between-sep-121-sbe-and-ee
Installing and configuring Symantec Endpoint Protection Small Business Edition
http://www.symantec.com/docs/TECH91893
Symantec™ Endpoint Protection, Symantec Endpoint Protection Small Business Edition, and Symantec Network Access Control 12.1.3 Release Notes
http://www.symantec.com/docs/DOC6549
Knowledgebase Articles for Symantec Endpoint Protection SBE 12.1. RU3
https://www-secure.symantec.com/connect/blogs/knowledgebase-articles-symantec-endpoint-protection-sbe-121-ru3
Symantec Endpoint Protection SBE 2013 - Symantec Endpoint Protection Small Business Edition 2013 offers simple, fast and effective protection against viruses and malware. It is available as a cloud-managed service which means there are no additional hardware requirements for the management layer as all administrative task are executed from a web-based console. SBE 2013 has as well an option available for on-premise management application in case this is more preferable to cloud-managed one. Similar to other SEP 12.1 solution as SBE and Enterprise Edition the SBE 2013 offers an unified security solution with a variety of features like Antivus and Antimalware protection, Firewall, heuristic Sonar protection, etc.
Symantec Endpoint Protection Small Business Edition 2013
http://www.symantec.com/endpoint-protection-small-business-edition-2013
Quick Start Tips for SEP Small Business Edition 2013
https://www-secure.symantec.com/connect/articles/quick-start-tips-sep-small-business-edition-2013
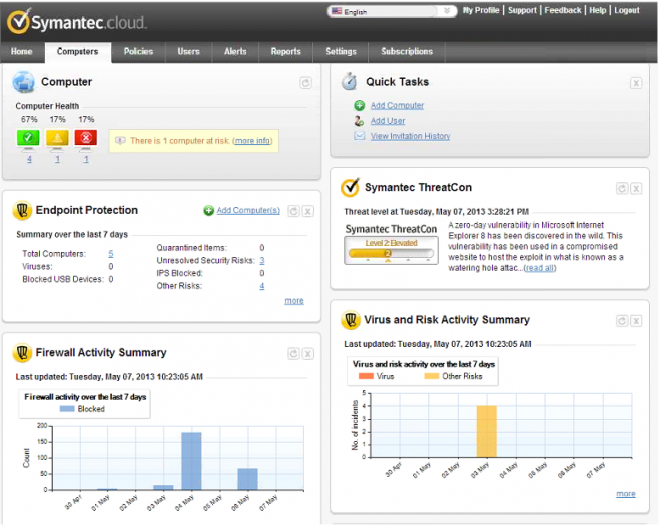
(Customized Home Page of the Symantec Endpoint Protection SBE 2013 management on the Symantec.cloud portal)

(SEP SBE 2013 Client profile overview on Symantec.cloud)
Symantec Protection Center (SPC) - a centralized security management console that allows organizations to identify emerging threats, prioritize tasks and accelerate time to protection based on relevant, actionable intelligence. Protection Center is a free product, available at no additional charge for existing Endpoint Protection 12 customers. Protection Center allows for management of Symantec Endpoint Protection together with other Symantec products in a single environment. Symantec Endpoint Protection is integrated with Protection Center by means of a series of Web services. Protection Center incorporates early warning notifications from the
Symantec Global Intelligence Network, which is one of the world’s largest commercial cyber intelligence communities.
Symantec Protection Center
http://www.symantec.com/page.jsp?id=protection-center
About Symantec Endpoint Protection and Protection Center
http://www.symantec.com/docs/HOWTO55225
About setting up Symantec Endpoint Protection in Protection Center
http://www.symantec.com/docs/HOWTO55231
Symantec Protection Suite (SPS) - a budled product of Symantec Security Software, available both in Small Business Edition as well as Enterprise editions, comprising of following components:
■ Endpoint Protection
■ Endpoint Protection for Macintosh
■ Antivirus for Linux
■ Mail Security for Microsoft Exchange
■ Mail Security for Domino
■ Messaging Gateway
■ System Recovery Desktop Edition
■ Symantec Protection Center
■ Web Gateway
SPS provides multiple layers of protection for endpoint security, messaging security, web, data loss prevention, and data and system recovery, allows as well for deployment of integrated essential endpoint and messaging security technologies as unified solutions with coordinated management.

Symantec Protection Suite Enterprise Edition
http://www.symantec.com/protection-suite-enterprise-edition
Compare Antivirus Software & Security Products
http://store.symantec.com/antivirus-comparison
Protect More, With Less - See How Symantec Protection Suite Can Do It
http://www.symantec.com/tv/products/details.jsp?vid=1211579625001
Symantec Vulnerability Protection - SEP browser add-on known previously under the name of "Browser Intrusion Prevention" and is a new advanced protection feature included with the SEP 12.1 client. This technology works in conjunction with, but is separate from the Client Intrusion Detection System (CIDS) used by the client firewall-based IPS engine in SEP.
Enabling or disabling network intrusion prevention or browser intrusion prevention
http://www.symantec.com/docs/HOWTO80887
Supported Browser versions for Browser Intrusion Prevention
http://www.symantec.com/docs/TECH174537
Expected behavior of Browser Intrusion Prevention
http://www.symantec.com/docs/TECH172174
SymHelp - tool used for both SEP client and SEPM Server troubleshooting but not exlusively. The complete list of Symantec products it is used for consist of Backup Exec, Symantec DLP, SEP and SEPM, Symantec Mail Security, Symantec System Recovery. Symhelp is a new version (designed for SEP 12.1 RU2 and higher) that replaces the old Symantec Support Tool. SymHelp may be downloaded directly from the SEP GUI - by going into Help -> Download Support tool -> this redirects directly to the Symantec Article mentioned below in the reference.
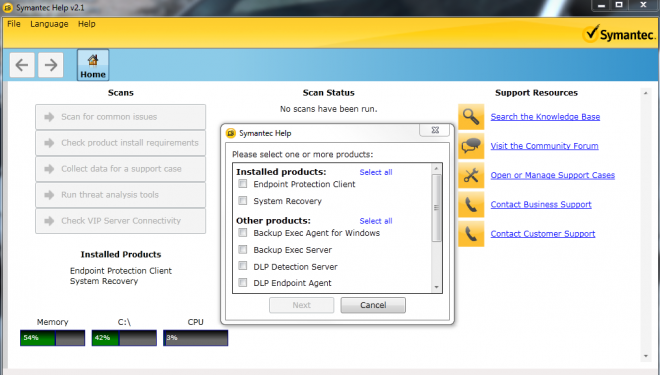
Symantec Help (SymHelp)
http://www.symantec.com/docs/TECH170752
About Symantec Help (SymHelp)
http://www.symantec.com/docs/TECH170735
Symantec Help (SymHelp) FAQ
http://www.symantec.com/docs/TECH203496
System Lockdown - System Lockdown allows administrators to tightly control which applications users running the SEP Client can execute. The approved applications are contained in a so-called fingerprint list which contains checksums and locations of all applications that are approved for use. Implementing System Lockdown is a two step process. First, a fingerprint list needs to be created, and then this fingerprint list needs to be imported into the Symantec Endpoint Protection Manager for use in Client Policies. You can use system lockdown to control applications in the following ways:
■ Control all the applications that can run whether or not the user is connected to the network.
■ Block almost any Trojan horse, spyware, or malware that tries to run or load itself into an existing application.

How to configure System Lockdown in Symantec Endpoint Protection 11.0
http://www.symantec.com/docs/TECH102526
Configuring system lockdown
http://www.symantec.com/docs/HOWTO80848
About system lockdown
http://www.symantec.com/docs/HOWTO27322
System lockdown prerequisites
http://www.symantec.com/docs/HOWTO27321
How to configure System Lockdown to allow Microsoft Security Updates
http://www.symantec.com/docs/TECH103977
Tamper Protection - provides real-time protection for Symantec applications, drivers and services. It prevents Symantec processes from being attacked or affected by non-Symantec processes, such as worms, Trojans, viruses, and security risks. Tamper Protection blocks as well registry changes for the keys related to Symantec Endpoint Protection.
What should I do when I get a Tamper Protection Alert?
http://www.symantec.com/docs/TECH97931
Third Party Management (TPM)- an alternative to allow third-party content distribution solutions to update the managed SEP clients instead of usual updates from SEPM/GUP or Livedupdate Servers. The setting may be activated in the Liveupdate policy. Third Party Management setting activation is required if the SEP client is to be updated with a .jdb file containing virsu definitions. Third Party Management is not required for defintions updates performed with use of Intelligent Updater.
How to manually update definitions for a managed Symantec Endpoint Protection Client using the .jdb file
http://www.symantec.com/docs/TECH104363
Configuring a LiveUpdate Settings policy to allow third-party content distribution to managed clients
http://www.symantec.com/docs/HOWTO80943
Enabling third-party content distribution to managed clients with a LiveUpdate Settings Policy
http://www.symantec.com/docs/HOWTO27639
Third Party Security Software Removal- a new feature of SEP installer introduced in SEP 12.1 RU1 MP1 and further enhanced in 12.1 RU2. When the feature is being activated for the installation package, Symantec Endpoint Protection can perform security software removal as part of its installation process. Installation packages that are deployed with this feature will remove any currently installed security software from several third-party vendors. For list of supported security software by this feature refer to the below documentation.
About the third-party security software removal feature in Symantec Endpoint Protection 12.1 RU1 MP1 and later
http://www.symantec.com/docs/TECH178757
Third-party security software removal support in Symantec Endpoint Protection 12.1.2 and later
http://www.symantec.com/docs/TECH195029
Threat Analysis Scan - a new feature included in Symhelp since version 2.1.22.177, that can help to identify suspicious files on a system. This new feature replaces the previously known Load Point Analysis and Power Eraser tools. The Threat Analysis Scan can help to identify the following types of malware:
- New variants of existing threats that are not detected by the current definition sets
- Fake antivirus applications and other rogueware
- Rootkits
- System settings that have been tampered with maliciously
Because the Threat Analysis Scan uses aggressive heuristics to detect these threats, there is a risk that it can select some legitimate programs for removal. A system does not have to be online in order for a Threat Analysis Scan to be run. However, the Threat Analysis Scan will have to be completed on another system with access to the internet before the report results can be viewed.
About the Threat Analysis Scan
How to run the Threat Analysis Scan in Symantec Help (SymHelp)
Truscan- a legacy proactive threat protection technology from SEP 11.x that was replaced in SEP 12.1 by the SONAR functionality - used to facilitate detections of new and unknown risks. By default, Truscan scans detect the processes that behave like Trojan horses and worms or processes that behave like keyloggers. Same as newer SONAR, Truscan looks at the behavior of active processes at the time that the scan runs. The scan engine looks for behavior such as opening ports or capturing keystrokes. If a process involves enough of these types of behaviors, the scan flags the process as a potential threat. The scan does not flag the process if the process does not exhibit suspicious behavior during the scan.
Understanding TruScan proactive threat detections
http://www.symantec.com/docs/HOWTO27054
Unmanaged Detector - a dedicated SEP client that works on a local network and looks at ARP traffic on that subnet to determine whether found machines in the subnet are running SEP already. The collected data is then forwarded to the Unmanaged Detector’s SEPM which compares the IP address and MAC address of detected systems against its known list of managed endpoint clients and reports on the unmanaged endpoint clients. An unmanaged detector is configured by right-clicking a managed SEP client in the Clients page of the SEPM console, and selecting "Make unmanaged detector". In order to act as an unmanaged detector, SEP clients must have Network Threat Protection (NTP) enabled and be in Computer Mode. User Mode clients or clients without the firewall component (NTP) cannot act as unmanaged detectors.
Best Practices: When to use the "Find Unmanaged Computers" or "Unmanaged Detector" features in Symantec Endpoint Protection 11.0
http://www.symantec.com/docs/TECH104340
Configuring a client to detect unmanaged devices
http://www.symantec.com/docs/HOWTO80763
SEP 12.1 - What does it mean to set a client as an Unmanaged Detector?
http://www.symantec.com/docs/TECH183746
What does it mean to set a client as an Unmanaged Detector?
http://www.symantec.com/docs/TECH105722
Unmanaged SEP Client - standalone SEP Client is administered directly by the end-user and is not reporting to the SEPM Server at all. An unmanaged client cannot be administered from the console. The primary computer user must update the client software, security policies, and virus definitions on the unmanaged client computer.

About managed and unmanaged clients
http://www.symantec.com/docs/HOWTO81263
Difference between a managed Symantec Endpoint Protection (SEP) Client and an Unmanaged SEP Client
http://www.symantec.com/docs/TECH185894
Installing an unmanaged client
http://www.symantec.com/docs/HOWTO81309
How to create an Unmanaged client from within the Symantec Endpoint Protection Manager
http://www.symantec.com/docs/TECH176907
Virtual Client Tagging - a new feature introduced in SEP 12.1. The feature in enabled by default on Symantec Endpoint Protection Manager and allows the SEPM to automatically identify and manage virtual clients. With Virtual Client Tagging the administrators can check in the properties of each SEP clients (from SEPM console) if the client at hand is virtualized or not.
Best practices for virtualization with Symantec Endpoint Protection 12.1, 12.1 RU1, and 12.1 RU1 MP1
http://www.symantec.com/docs/TECH173650
Virtual Image Exception (VIE) - a tool is designed specifically for environments leveraging virtualization technologies where a single baseline image is used to deploy many identical or nearly identical Virtual Desktop Infrastructure (VDI) clients. The VIE tool is used to add a new Extended File Attribute (EFA) value to all existing files on a machine before imaging. The EFA value remains valid until the file is modified. The Symantec Endpoint Protection (SEP) 12.1 client checks for this attribute before scanning files and skips scanning any files that are marked as "known good" by the VIE tool. Scans on VDI clients created with images processed by the VIE tool will experience lower I/O load, CPU usage, and network bandwidth usage during scheduled and manual scans.

About the Symantec Virtual Image Exception tool
http://www.symantec.com/docs/TECH172218
Using the Virtual Image Exception tool on a base image
http://www.symantec.com/docs/HOWTO55325
Web Console for SEPM - remote console that allows for a remote management of Symantec Endpoint Protection Manager from a web browser. Web console can be launched from SEPM Web Access (http://[servername]:9090). When you log on remotely, you can perform the same tasks as administrators who log on locally. What you can view and do from the console depends on the type of administrator you are.

Logging on to the Symantec Endpoint Protection Manager console
http://www.symantec.com/docs/HOWTO81152
How to install Web Console (Java Console) for Symantec Endpoint Protection Manager
http://www.symantec.com/docs/TECH105171