
Earlier this year, Symantec blogged about Infostealer.Bankeiya, a Trojan that was specifically targeting users in Japan through the Microsoft Internet Explorer Use-After-Free Remote Code Execution Vulnerability (CVE-2014-0322). Bankeiya monitors and steals confidential information specific to Japanese online banking sites.
A few months after our first blog, Symantec noticed that Infostealer.Bankeiya had resurfaced and was infecting more online banking customers in Japan. While it is unclear exactly how much money was stolen by Bankeiya, there is no doubt that its previous success contributed to this comeback. Yesterday, Symantec released a blog on a new variant of this malware (Infostealer.Bankeiya.B) that takes advantage of a vulnerability in Adobe Flash Player.
Who needs vulnerabilities
The attackers behind this malware don’t seem to have any intentions of quitting any time soon and have now started spreading Bankeiya without the use of a vulnerability.
Buffalo, a Japanese computer peripheral company announced today (Japanese language) that some of their driver installers, that were publically distributed on their website, were compromised and injected with malware. Symantec can confirm that the malware in question is Infostealer.Bankeiya.B.
According to the Buffalo release, the files were compromised early on the morning of May 27, 2014, Japan time. The company then shut down the download site from 13:00 on the same day. Ten files were compromised and downloaded a total of 856 times from 540 unique IP addresses.
The installers were modified in two ways. In the first example, a self-extracting RAR file called setup.exe was modified to execute a malicious .dll file during the installation process. The .dll file is a Trojan which drops another .dll that downloads and installs Infostealer.Bankeiya.B from a remote location. The digital signing certificate is broken due to the file being modified.
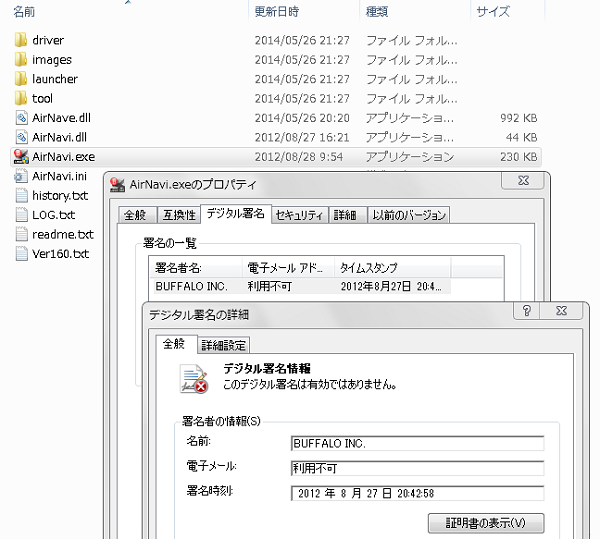
Figure 1. Broken digital certificate of the modified file
In the second method, a Buffalo installer is included within Infostealr.Bankeiya.B and Infostealer.Bankeiya.B is made to look like a legitimate installer. This means that running the installer will drop the setup.exe file for the legitimate driver as well as a component of the Trojan that drops a malicious .dll which downloads the main component of Infostealer.Bankeiya.B.
When the compromised installers are executed, a Chinese language WinRAR user interface is displayed (Figure.2).

Figure 2. Chinese language WinRAR interface displayed when compromised driver installer is executed
Protection
Symantec detects all the malicious components as Infostealr.Bankeiya.B.
Symantec advises users who may be affected by Bankeiya to scan your computer immediately with up-to-date security software and change your online banking passwords.