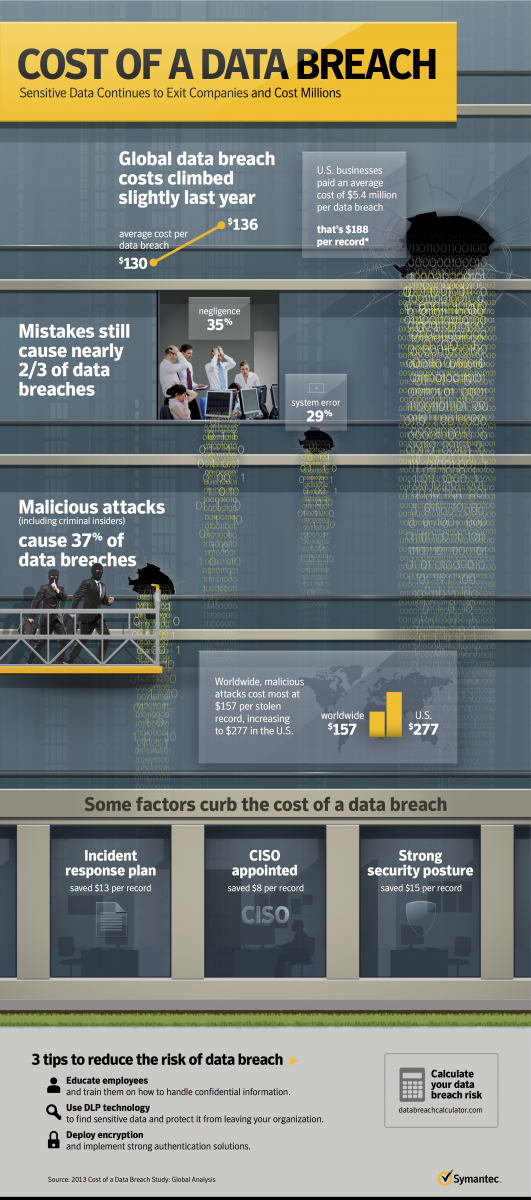
If it seems as if every week there is another story in the news about a data breach, you aren’t mistaken. Around the world, companies are experiencing an unprecedented number of data breaches and cyber-attacks. According to Symantec’s Internet Security Threat Report, the total number of breaches in 2013 increased by 62 percent compared to 2012 with 253 total breaches, at least eight of which exposed more than 10 million identities. In total, over 552 million identities were breached in 2013, putting consumer’s credit card information, medical records, financial information, email addresses, online credentials, and other personal information at risk.
Data breaches are most often associated with nefarious outside attackers hacking into an organization’s network, but hackers aren’t the only source of leaked information. While hacking continues to be the leading cause of data breaches, comprising 35 percent of data breaches in 2013, accidental exposure (29 percent) and theft or loss (27 percent) followed closely behind. All in all, today’s massive breaches highlight the importance of having defenses in place to keep intruders out as well as systems setup to stop sensitive information from leaving the network.
No matter the type of breach, one thing remains consistent in stopping them: having strong protections at the endpoint. As the network perimeter continues to get more dispersed, evolved endpoint protection becomes an imperative.
Keep the Attackers Out
Antivirus alone is not enough to defend your business against these types of attacks. Relying on just antivirus can leave your data exposed, and traditional endpoints, such as desktops and laptops can be a vulnerable entryway for breaches.
To keep cyber threats from penetrating critical systems, companies must look for endpoint security solutions that prevent targeted attacks and advanced persistent threats with intelligent security and layered protection that goes beyond antivirus.
Symantec Endpoint Protection goes beyond antivirus to provide layers of protection at the endpoint, from our unique Insight reputation and SONAR behavioral technologies to firewall, intrusion prevention and granular policy control features. We leverage the collective wisdom of the world’s largest Global Intelligence Network (GIN), which gathers data from hundreds of millions of users and sensors. Derived from the GIN, our Insight technology accurately identifies file reputation by analyzing key file attributes, such as age, source, and prevalence, and can reduce scan overhead by up to 70% by only scanning at-risk files, effectively defending against new, mutating malware on the endpoint without compromising performance. In addition, Symantec’s SONAR technology monitors file behaviors as they execute in real-time. Together, Insight and SONAR successfully stop targeted attacks, advanced persistent threats, and zero-day threats.
Protection from Loss and Theft
There are numerous security solutions to protect your data from attackers trying to get in, but none can help if your devices are physically lost or stolen. This is where endpoint encryption is essential. Endpoint encryption is the best way to protect the data on laptops, desktops and removable media when a device goes missing, because even if the device is lost, the data remains safe and unusable.
Endpoint encryption uses a pre-boot passphrase to protect a machine, so that nothing on the machine can start or boot-up until the correct passphrase is entered. Without the passphrase, the information on the device remains scrambled, preventing outsiders from accessing the data on the machine. Our newly released Symantec Endpoint Encryption solution, offers strong disk and removable media encryption that allows organizations to protect sensitive data from loss or theft, with an intuitive central management platform that helps administrators prove a device was encrypted should it go missing.
Encrypting confidential information is an easy way to protect your organization from a potentially costly data breach. In addition to the financial costs, which rose by 15 percent last year to an average cost of $3.5 million dollars in 2013, there are severe business repercussions. Breach notification laws require organizations to personally notify potentially affected victims, alerting them to what went missing and what could have been exposed. Afterwards, many victims feel they are owed identity theft protection (63 percent) and credit monitoring services (58 percent), all taking a combined toll on the offending organization. It’s important to be prepared and protected before problems like these arise, because for companies it’s no longer a matter of “if” but “when” they will experience a breakdown in data security.
By combining Symantec Endpoint Protection with Endpoint Encryption customers create an endpoint security solution that mitigates pervasive software attacks and encompasses physical security from loss or theft. For more information on our recent product releases check out the following blogs:
Want to learn more about how to keep endpoint data secure in the midst of mega breaches? Please sign up for our webcast with Symantec security expert, Kevin Haley: https://symantecevents.verite.com/32430/183000