On June 19, we came across an interesting e-card spam campaign. E-card spam typically distributes malware; however this campaign simply redirects the user to a “get rich quick” website.
This campaign’s emails are very basic. The messages are sent from a spoofed 123greetings.com email address and contain one sentence and a link.
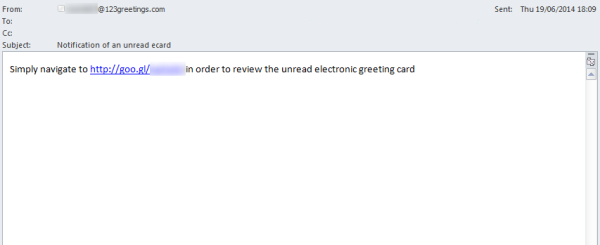
Figure 1. E-card spam campaign email
After looking at the header for one of the emails, we saw that the email appears to have been sent from an Amazon IP address. This is most likely an attempt to trick anyone that reads the header into thinking the email is legitimate. However, the IP address actually resolves to a DNS name that is not associated with Amazon.
In the body of the emails, the spammers use URL shorteners to redirect victims to their site. In this example, the spammers used Google’s URL shortening service. Normally, 123greetings does not use URL shorteners for its e-card service. Instead, it provides a URL which contains its own domain name.
The link directs users to a Web page that mimics the appearance and domain name of 123greetings. According to records on WhoIs, this domain was registered on June 17 in Panama. Additional details were hidden by WhoIsGuard privacy.
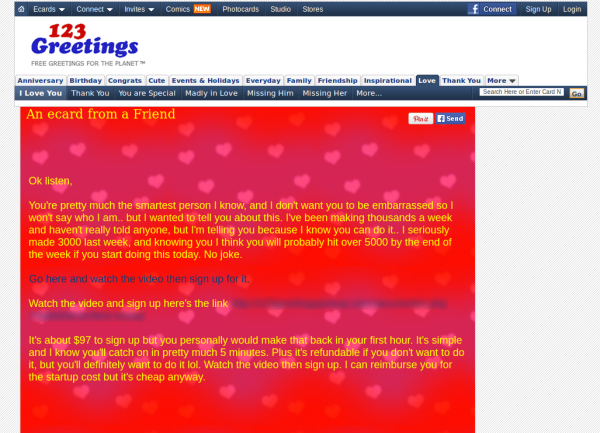
Figure 2. Fake 123greetings website
The fraudulent e-card page offers details on a “get rich quick” scheme, which promises that the user will make thousands of dollars within one week if they pay US$97. The scam encourages the user to click on a link to sign up. While this is not new technique, the spammer tries to make this campaign seem more legitimate by using 123greetings’ branding.
The link on this webpage redirects users to different remote locations several times before they end up at the “get rich quick” website, which asks the user for their contact details. The spammer will then contact the user, most likely through automated telephone messages or additional emails, to convince the user to sign up and pay to take part in the alleged scheme. As an added bonus, the spammer may use the obtained contact details to target the user with more spam.

Figure 3. “Get rich quick” spam site
We have also seen spam with a slight variation of this campaign. In this campaign, the e-card link sends users to a fake BBC news article. The spammer is once again hoping to convince the user that this scam is legitimate, before they redirect the user to the “get rich quick” website.
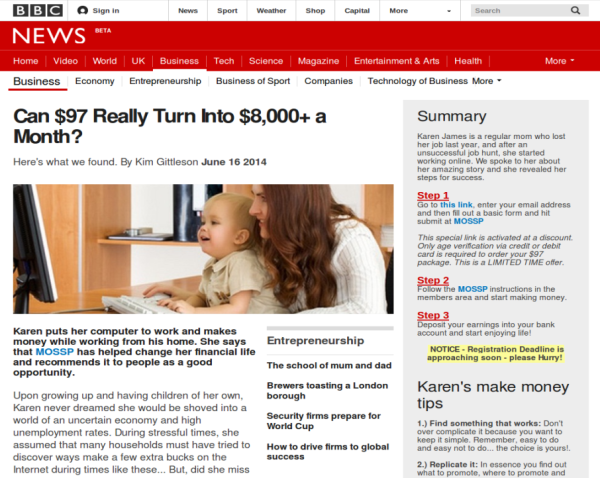
Figure 4. Fake BBC news article for “get rich quick” scheme
For the fake news article, the scammer registered another domain that resembles the legitimate BBC domain name. This fake news article promises that the user will be able to make more than US$8,000 a month by paying $97 in advance. The site also contains links to news articles hosted on the legitimate BBC news website in order to make the scam look more authentic. The scammer obviously scraped these links at the time they constructed this fraudulent site. The webpage eventually encourages the user to click on a link which directs them to the “get rich quick” spam site.
Symantec advises users to adhere to the following security best practices:
- Exercise caution when receiving unsolicited, unexpected, or suspicious emails
- Avoid clicking on links in unsolicited, unexpected, or suspicious emails
- Avoid opening attachments in unsolicited, unexpected, or suspicious emails
- Keep security software up-to-date
- Update antispam signatures regularly