
Last week, Adobe released an emergency patch to address a critical vulnerability (CVE-2016-1019) in Flash Player. The type confusion vulnerability is currently being actively exploited in the wild. Symantec has observed that exploit kits (EKs), including but not limited to Magnitude and Nuclear, have already started exploiting the vulnerability.
CVE-2016-1019 is expected to work on Flash versions 20.0.0.306 and earlier. Due to security enhancements introduced by Adobe, the exploit is not expected to work on versions 21.0.0.182 and later.
Magnitude’s delivery chain
For our analysis of this exploit we looked specifically at the Magnitude EK. Magnitude’s delivery chain starts with sending a script that initially identifies the dimensions of the screen and the screen’s color depth. This later leads to another website that responds with a script that checks the computer’s environment.
When Magnitude delivers CVE-2016-1019, it starts by sending a small Flash file. This file loads the main exploit (Exp.CVE-2016-1019) for CVE-2016-1019. To take advantage of the vulnerability, Magnitude hides the SWF file that helps trigger the vulnerability under a separate “DefineBinaryTag”. We have seen this technique used in other EKs as well.

Figure 1. Embedded Flash file that helps trigger the vulnerability
The exploit then checks the Flash Player's capabilities to determine how to proceed, based on the operating system the computer is running.
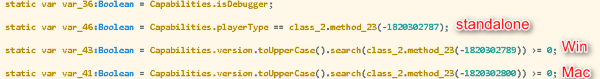
Figure 2. Exp.CVE-2016-1019 checks for Flash Player capabilities before proceeding
As with many exploits we have seen in the past, this one from Magnitude also modified a previously created ByteArray’s length to “0xFFFFFFFF”. Doing this allowed the code to achieve arbitrary read/write capabilities anywhere in memory.
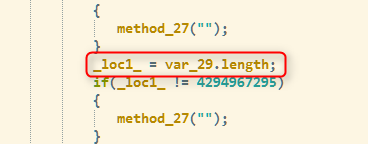
Figure 3. ByteArray size modified to “0xFFFFFFFF”
Figure 3 shows that “var_29” is the ByteArray modified to “0xFFFFFFFF”. This same ByteArray is used to harvest the APIs needed to execute the shellcode. Figure 4 shows the part of the exploit that helps to find the address of the “VirtualProtect” API.
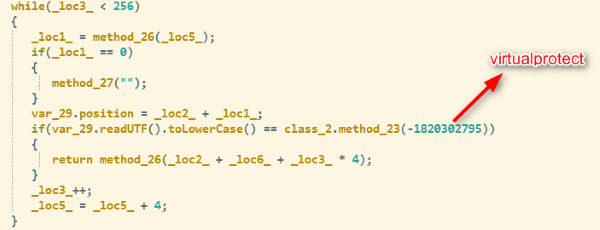
Figure 4. Exploit portion that helps find the “VirtualProtect” API address
Later, the memory area where the shellcode resides is made “RWX”, and the execution is transferred to the shellcode.
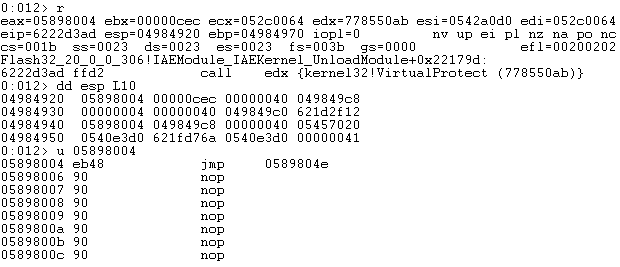
Figure 5. Memory pointing to shellcode made “RWX”
When the shellcode starts executing, it then downloads and executes Trojan.Cryptolocker.AH from a different server to where the EK is hosted.
The time it takes cybercriminals to incorporate new exploits into their kits is getting shorter. EK operators know that time is of the essence if they are to take advantage of unpatched computers. This further emphasizes the importance of keeping software up to date, as a fully patched computer is bad news for an exploit kit.
Mitigation
Symantec recommends that users download the current version of Adobe Flash Player to help protect against this vulnerability. Users who do not have the latest version of Flash Player installed face the risk of malware exposure.
Protection
Symantec and Norton products protect customers from this threat with the following detections:
Antivirus:
Intrusion prevention system: