Contributors: Zhe Liu and QuBo Song
With each new iOS release, a large number of users wait eagerly for the corresponding and inevitable jailbreak solution. Although jailbreaking compromises the security of the device, users resort to it because it allows them to install a wider variety of apps—including those that are not vetted by Apple—and often uses restricted APIs.
Symantec mobile researchers have come across a scam that takes advantage of users looking for an early jailbreak implementation. Scammers are spoofing TaiG, a popular iOS jailbreaking website, and claiming to have a beta tool that can jailbreak iOS 9.2.1, a recent version of the operating system. Users are actually led to a donation page, and receive only misleading web links on their device.
A quick web search for iOS jailbreaks brings up some familiar names, such as TaiG, Pangu, and Cydia. Following the TaiG beta link, we came across a page that touts the TaiG brand, but uses a slightly different domain name and look (TaiG9, as opposed to TaiG):

Figure 1. Fake TaiG9 jailbreak homepage
The website claims that the Windows and Mac tools for the iOS 9.2.1 jailbreak will be released soon. In the meantime, it offers users a purported beta tool that can execute a jailbreak through a browser of an iOS device. If users try to open the link on a non-iOS device, the page says the device is not supported. By using the correct user-agent value in our request to impersonate an iOS device, we got a look at what this “beta” tool does.
Users are guided through several steps to complete the jailbreak process, but these steps are misleading. We were unable to detect any activity related to jailbreaking in the browser aside from the dialog displayed by the site.
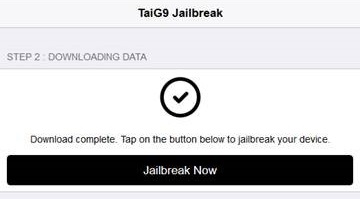
Figure 2. Misleading jailbreak process flow
Once the button is clicked in the final step, the user might expect an installation of the Cydia app, but the page actually serves an iOS configuration profile. Examining the profile, we see that it’s signed correctly with a COMODO CA, and therefore will be trusted by default on the device. The profile contains a web clip, which places a shortcut to a website on the user’s home screen, but may fool the user into thinking it’s an app.

Figure 3. Prompting an iOS profile download
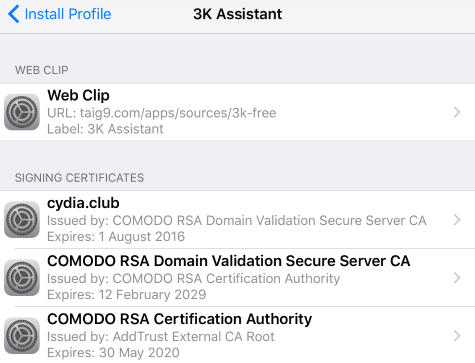
Figure 4. TaiG9 profile
Launching the shortcut takes the user to the URL configured in the profile, which is a TaiG9-hosted third-party app store. The website offers access to a “freemium” portion of the app store if a donation is made. Interestingly, the freemium portion of the site can be accessed without making the donation.
If a user attempts to install the Cydia app from this store, another iOS configuration profile is displayed, which creates a shortcut on the home screen, this time linking to a fake Cydia webpage. This page is apparently designed to make users believe they have successfully jailbroken their phone and installed the real Cydia app.
In the end, users are led to believe that they’ve jailbroken their phone, and have access to the Cydia community of apps—but, in reality, were tricked into installing two configuration profiles and subjected to a fraudulent solicitation for donations. Our telemetry shows over 100,000 Symantec users were lured to these pages.
Mitigation
Be wary because this fake jailbreak solution is dominating the top results on Google search, using well-known jailbreaking names to fool users, and receiving referrals on Reddit threads. Symantec does not recommend jailbreaking your device.