It’s happened to major corporations, and even the U.S. Department of Defense--falling victim to data breaches that resulted from attackers exploiting employees or company vendors. Unfortunately, along with exposing millions of identities these attacks also reveal what is often the weakest link in enterprise data security – the human element.
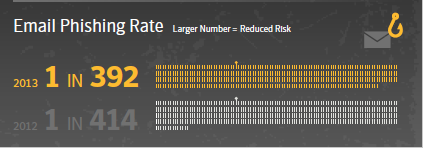
Over the past decade, an increasing number of users have been targeted with spear-phishing attacks and the social engineering has grown more sophisticated over time. The risks of data breaches that can result from these attacks are incredibly high – there were over 552 million identities exposed in data breaches during 2013. It’s obvious that protecting your organization and customer information is crucial, and protection in this case starts with knowing your enemy. It’s important that your organization and employees understand what these attacks look like and how to defend against them.
Incognito Emails
Today’s phishing attacks are no longer as simple and obvious as those you may remember. Hackers have developed sophisticated spear-phishing methods that rely heavily on refined and well-researched social engineering to improve their chances of success. Their emails are specifically tailored to spark the interest of the individual being targeted to increase the likelihood that they will open them.
Attackers may make emails appear to come from someone that the target knows, a source they would trust, or contain information that would be relevant to the target’s professional role. For instance, an attacker may send someone working in human resources a spear-phishing email that includes a resume attachment laden with malware, or send an employee an important notice that appears to be from his or her banking institution. In fact, according to Symantec’s latest Internet Security Threat Report (ISTR), 71 percent of last year’s phishing attacks were related to spoofed financial organizations, compared with 67 percent in 2012. The attackers can be very well disguised and as a result, they may be almost impossible to identify without the right controls in place to safeguard against it.

While spear-phishing attacks have traditionally only targeted email, we saw last year that a growing number of attackers are also using more aggressive offline tactics. In addition to sending emails attackers are using assertive follow up phone calls directly to the target to pressure him or her to open the email. In the “Francophoned” attack from April 2013, an attacker impersonated a high-ranking employee and requested that the target open the attachment immediately. In other cases, cybercriminals have pretended to be tech support to convince targets to open emails or run nefarious computer programs.
Attackers have even taken to leaving physical bait to take advantage of employees and gain access to organizations. In some cases, attackers have planted “lost” devices on or around the campuses of targeted organizations in the hopes that employees will retrieve them and open them on a company computer.
The important question this may leave you asking is: How do I protect my company and our data from being compromised? While there is no silver bullet solution, education is key. Most importantly, start by doing security awareness training the right way.
Don’t rely on just providing employee handbooks to educate your workforce. Effective training is actionable and should include actively testing your employees by throwing real-life circumstances at them. For example, send out phishing emails to mimic what a real-attack would look like and then use the test as a teaching moment for your employees. For Atlantic Media, this type of cyber-attack drill helped provide the data to support the need for greater vigilance among employees and proved to be the safest and most effective tactic to build the company’s collective security intelligence.