At the beginning of April, a vulnerability in the OpenSSL cryptography library, also known as the Heartbleed bug, made headlines around the world. If you haven’t heard of the Heartbleed Bug, Symantec has published a security advisory and a blog detailing how the Heartbleed bug works.
As with any major news, it is only a matter of time before cybercriminals take advantage of the public’s interest in the story. Symantec recently uncovered a spam campaign using Heartbleed as a way to scare users into installing malware onto their computers. The email warns users that while they may have done what they can by changing their passwords on the websites they use, their computer may still be “infected” with the Heartbleed bug. The spam requests that the user run the Heartbleed bug removal tool that is attached to the email in order to “clean” their computer from the infection.
This type of social engineering targets users who may not have enough technical knowledge to know that the Heartbleed bug is not malware and that there is no possibility of it infecting computers. The email uses social and scare tactics to lure users into opening the attached file.
One warning sign that should raise suspicion is that the subject line, “Looking for Investment Opportunities from Syria,” is totally unrelated to the body of the email.
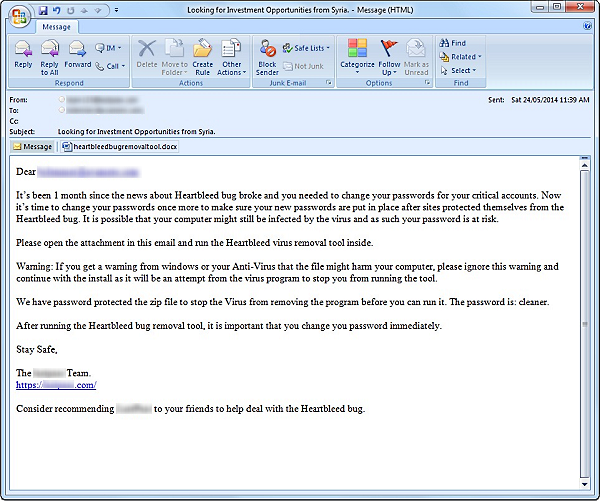
Figure 1. Heartbleed bug removal tool spam email
The email tries to gain credibility by pretending to come from a well-known password management company. The email provides details on how to run the removal tool and what to do if antivirus software blocks it. The attached file is a docx file which may seem safer than an executable file to users. However, once the docx file is opened the user is presented with an encrypted zip file. Once the user extracts the zip file, they will find the malicious heartbleedbugremovaltool.exe file inside.
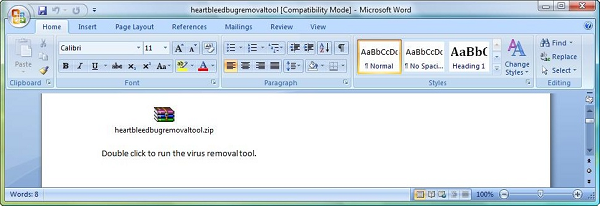
Figure 2. Encrypted zip file
Once heartbleedbugremovaltool.exe is executed, it downloads a keylogger in the background while a popup message appears on the screen with a progress bar. Once the progress bar completes, a message states that the Heartbleed bug was not found and that the computer is clean.
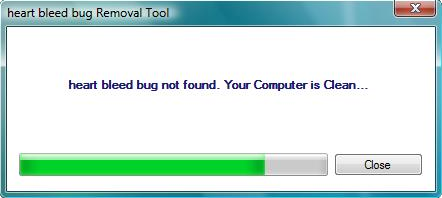
Figure 3. Popup message
After the fake removal tool gives a clean bill of health users may feel relieved that their computers are not infected; however, this couldn’t be further from the truth as they now have a keylogger recording keystrokes and taking screen shots and sending confidential information to a free hosted email provider.
As detailed in the official Symantec Heartbleed Advisory, Symantec warns users to be cautious of any email that requests new or updated personal information, and emails asking users to run files to remove the Heartbleed bug. Users should also avoid clicking on links in suspicious messages.
Symantec detects this malware as Trojan.Dropper and detects the downloaded malicious file as Infostealer.
Symantec.cloud Skeptic heuristics engine is blocking this campaign and detecting it as Trojan.Gen.