A Manifesto for Great Security
If you want the right security outcomes, your policy documentation must be equal parts love letter, tax return, graduation thesis, and owner’s manual
A well-written policy is the foundation for an organization’s security posture.
As the Global Security Office, Symantec’s internal cyber security team, we’ve spent considerable energy refining our approach to information security policy and creating the frameworks and guardrails that guide our staff towards good security behaviors.
In this blog we’d like to share how we’re using security policy documentation to help drive an organization-wide culture of security.
A policy needs to be clear, concise, and comprehensive; its goal is to provide the workforce a straightforward outline of what to do and how to do it.
For starters, our security policy provides the direction and intent for information security within Symantec. It’s the primary artefact that communicates our expectations for secure behaviors and practices within the organization. It also describes the standard we hold ourselves to and the expectations we have of the broader organization. A policy needs to be clear, concise, and comprehensive; its goal is to provide the workforce a straightforward outline of what to do and how to do it.
We place a very high bar on the quality of our documentation. It’s not good enough simply to drive the right security outcomes. Our policy is our resume for security, and it must be nothing short of exceptional. It is equal parts love letter, tax return, graduation thesis, and owner’s manual. It must be easy to understand, it must withstand the highest audit scrutiny, and at all times it should inspire excellence.
Write Less, Say More
The central challenge for any policy writer is to articulate complicated topics in a straightforward way. You have to dive deep into the subject matter, distill its core purpose and intent, and summarize it as simply as possible. Our goal is to have policies that are clear, well-defined and easy to consume.
One of the most common downfalls of security policies is over-engineered language that dances around desired outcomes. Your readers will become lost if you try to account for every nuance and use case; go too far and your meaning will be lost entirely. Sure, such language allows you to argue a good case with auditors, but that doesn’t do much good if you can’t get the workforce to understand what you mean.
For example:
- Not awesome:
- All users throughout the company shall enforce user-level, system-level, privileged, service, and generic password lengths as used in any networks, systems, centralized servers, or cloud services of no less than but wherever possible greater than ten (10) characters as defined by established best practices and in compliance with relevant laws and regulations.
- Better:
- Passwords of at least ten (10) characters in length must be enforced for all users and systems throughout the company in accordance with best practices, laws, and regulations.
- Straight to the point:
- Passwords are at least ten characters long.
Writing styles and requirements vary greatly depending on your organization and industry, but care should always be taken to focus policy language as tightly as possible.
Building on a Foundation
Concise policy language helps to reduce document length, but a truly comprehensive information security policy can easily be 50 pages or more and not especially easy to read. So how then are you supposed to fit everything into a single document? Good news! You don’t have to.
Symantec’s information security policy framework is underpinned by a single, concise, high-level policy that outlines the company’s security direction and intent. This foundational policy document serves as the basis for a suite of security standards, each narrowly focused on a topic area, that describe the criteria for complying with the policy. This hierarchy of documentation helps us focus the messages we seek to convey.
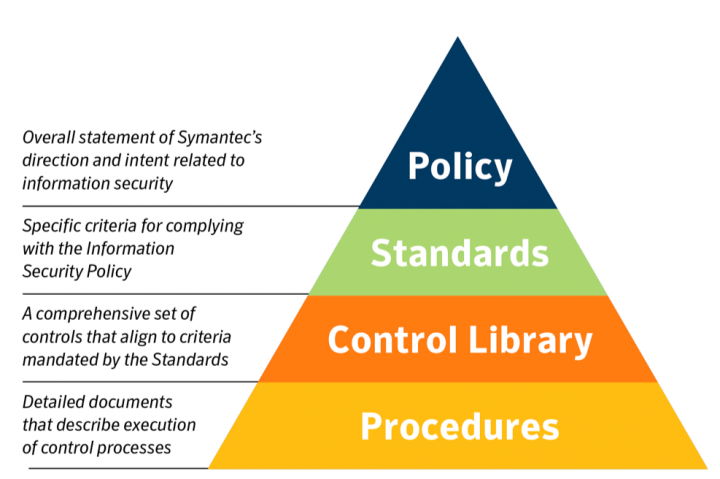
To bring this to life, let’s look at data protection as an example. Our information security policy describes the need to classify and handle data according to its sensitivity. If an employee walks away from reading this document with a basic understanding that some information is more sensitive than others, and needs to be treated differently as a result, we’ve made a good start.
Our data classification standard then gives this employee more granular detail on how to live by this policy. It describes in more detail the types of data classifications at Symantec, and clearly lists handling standards for each – for instance, when and how to encrypt data based on its sensitivity.
From Policy to Habit
But for all our efforts towards simplicity and accessibility, we know people don’t always retain information contained in documents like policies and terms of use. As committed security professionals, we must continuously work at helping staff internalize our policies.
At Symantec we created “Security Non-Negotiables”, a set of behaviors and expectations everybody is expected to live by in their daily work. Each Non-Negotiable links to a specific section of our policy, such as data protection or access.
The Non-Negotiables provide a great vehicle for keeping our policies front of mind for staff. They have strong and visible executive sponsorship – our C-level execs are often seen and heard referring to them – and are a focus of ongoing organization-wide communications.
Policy also features centrally in our staff awareness programs.
It’s not enough to educate staff about the content of each document in the policy framework (although we do that too). We’ve also developed modules that educate staff on the use of policy itself – for instance, where staff can find our policies and procedures and how to determine which documents are relevant to their roles and tasks. A highly creative approach to these modules – using gamification and story-telling – helps drives staff engagement.
Tooling is the final piece in how we embed policy into daily habits and operations. We work closely with our internal technology teams to create practical tools that make policy compliance a simple, seamless and habitual process.
Our own Symantec solutions play a key role, such as plug-ins for Microsoft Office based on Information Centric Tagging, which enables documents to be automatically classified according to their sensitivity. Our other solutions, such as Symantec DLP, monitor and alert based on these classifications.
Key Takeaways
We’d love to hear any great ideas you have on the fine art of writing security policy. In the meantime, here are our key takeaways:
-
Deliver excellence. High quality documents inspire confidence, drive behaviors, and reduce audit observations
-
Be clear. Don’t add verbiage where it is not needed. Continually ask yourself, “How can I deliver the same message with fewer words?”
- Make it relatable. Show the workforce how your policy relates to them. Use real-world examples they can learn from.

10 Ground Rules for Red Teams
An effective Red Team offers huge value to your defensive strategy, but you have to be prepared to face up to some hard truths








We encourage you to share your thoughts on your favorite social platform.