Ongoing Android Malware Campaign Targets Palestinians - Part 1
APT-C-23 continues its assault with a new Android malware variant
It has been more than a year since the group “APT-C-23” started to spread its Android Malware in the Middle East (mainly against its Palestinian political rivals), and it seems the Malware authors are not apprehensive about continuing to spread newer versions of its Malware.
The latest sample we analyzed is of an application named “Zee Player”, that was added to Google Play a few weeks ago. The app is described as a media player that can “hide your pictures and video” (well maybe that explains why it hides its own icon...).

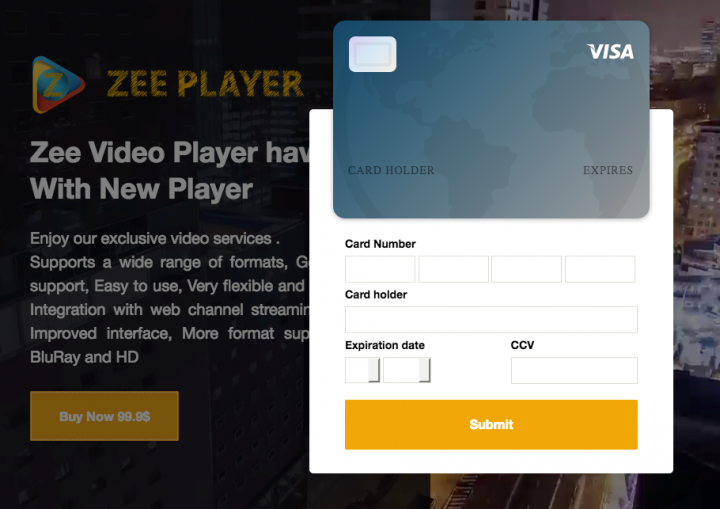
We’ve noticed the Google Play page has a link to a developer website. This site is a scam that tries to exfiltrate your credit card details for “exclusive video services”, before you even actually install the app.
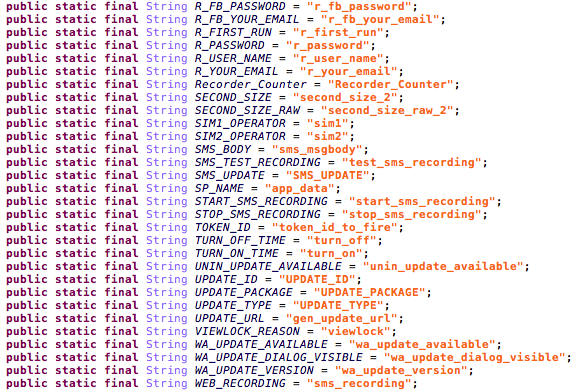
Looking under the hood of the application, it seems it is a new sample of GnatSpy, that can grab information from the device and trick the victim to install more Malware. A quick view of the SharedPreferences manager can already reveal the app’s true intentions.
"Zee Player" is only the latest sample from APT-C-23's recent Android malware campaign. We have been monitoring the group's activity in the past year and it seems we were not the only ones. In today's Pastebin publication we found some details about the recent samples, as well as a reference to an open source tool that is able to scan Android devices and remove the said Malware.
We have inspected the tool’s source (commit 19a0e55) and from our review it indeed does what it claims to. However, the way it removes the Malware is too simplistic, as it removes the Malware solely based on the package name of the APK.
As more information becomes available about APT-C-23, we expect to present a more thorough report, including technical details of the group's modus operandi, attached with a big list of IoC’s (Indicators of Compromise) that we've analyzed.
Mitigations
Stay protected from mobile malware by taking these precautions:
- Do not download apps from unfamiliar sites
- Only install apps from trusted sources
- Pay close attention to the permissions requested by apps
- Install a suitable mobile security app, such as SEP Mobile or Norton, to protect your device and data
- Keep your operating system up to date
- Make frequent backups of important data
Zee-Player IOC’s:
SHA256: cbf9a0737e27fafafaff5c73825bb96907a976b230bf18843badd7b10d475eb2
Package name: co.zeeplayer
Domains: zee-player[.]com, zee-player[.]website, kristy-milligan[.]website







We encourage you to share your thoughts on your favorite social platform.