Phishing for a Proactive Security Culture
How to drive a measurable reduction in security risk using phishing simulations
One of the most critical layers of defense in cyber security is a proactive security culture where the expectation is that all users are playing their part to protect themselves and the organization from harm.
Users need to be aware of their susceptibility to threats, but also confident in their ability to protect themselves and their colleagues. As discussed in previous posts, we believe the best way to learn is by getting hands-on practice, using simulated exercises such as phishing assessments.
Symantec’s Global Security Office engaged in an intensive 12-month phishing campaign between August 2018 and July 2019, which among other goals aimed to boost engagement of Symantec staff in our security uplift program.
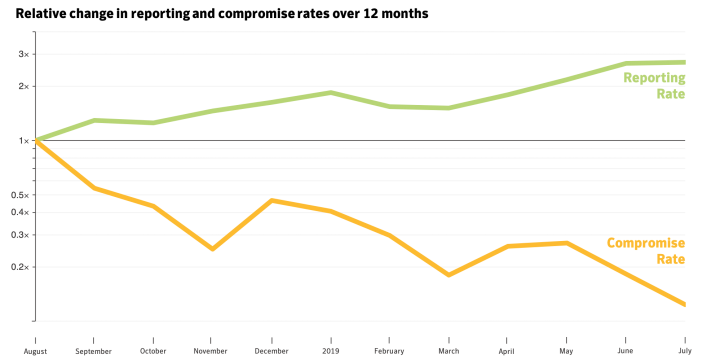
We’ve enjoyed some strong results: Symantec staff are now 2-3 times more likely to report suspicious activity to the security operations center today than they were 12 months ago.
The graph below reveals the relative positive reporting and compromise rates for Symantec staff over the 12-month campaign.
Framing the Challenge
Convincing thousands of users to persistently report suspicious activity to the right channels requires a campaign of sustained training and comms. Our organization is relatively fragmented and globally-distributed – encompassing enterprise and consumer-facing teams and supporting functions. Many products were inherited from start-ups that each brought elements of their own working culture to Symantec.
We anticipated that engineers that manage a highly-tuned email filtering service and develop email isolation tools would likely question the need for phishing simulations, as these tools are designed to prevent users from having to interact with these threats altogether. We had to convince them to suspend their disbelief and assume attackers had found a way to circumvent our technical controls. Chief among our arguments was that users had to be ready to play a role if it ever were required of them, whether in or out of their work context.
With that in mind, we needed the campaign to drive organic conversations about the social and behavioral aspects of phishing. Our assessments had to strike a delicate balance between consistency and cunning. There would be a minimum of three ‘tells’ in every lure that all staff could be trained to identify, but equally we had to reflect the crafty techniques attackers use to make phishing so successful.
The Hall of “Phame”
And so was born Symantec’s Hall of Phame, a 12-month phishing campaign designed to imitate the most compelling and impactful real-world phishing campaigns in history. These infamous examples would demonstrate to staff that anybody can fall victim to the right lure.
We scoured our threat intelligence data, law enforcement indictments and ran image searches to identify appropriate lures used by cyber crime gangs (such as Carbanak, Dridex and Mealybug) and nation-state actors (such as Appleworm, Dragonfly and Sandworm) that we could emulate in the assessments.
Chasing Learning Outcomes
Any user compromised in these assessments would be presented with a training page in Symantec’s Phishing Readiness Platform. The training page would feature a short story narrative about the real-world campaign we had emulated. We discussed what techniques and tradecraft the real attackers used, what human instincts they preyed upon and the impact of the attacks. We wanted learners to draw a line between the lure they fell victim to and known attacks that interrupted power grids, stole vast sums of money, pilfered intellectual property, destroyed networks or interfered with elections. We also developed animated GIFs pointing out what ‘tells’ the compromised user could have picked up on, followed by a just-in-time quiz to reinforce what they’d learned.
Articles on each assessment were also published on the company intranet. Each article presented an opportunity to reinforce training about the correct ways to handle and report suspicious messages to Symantec’s security operations center. They also directed readers to a leaderboard that ranked the positive reporting rates by business unit in order to drive competitive interest in identifying and reporting suspicious activity.
We wanted learners to draw a line between the lure they fell victim to and known attacks that interrupted power grids, stole vast sums of money, pilfered intellectual property, destroyed networks or interfered with elections.
For the entire 12 months of the campaign, these were by far the most read articles on Symantec’s intranet each month, with all but one doubling the average traffic of the five highest stories that month.
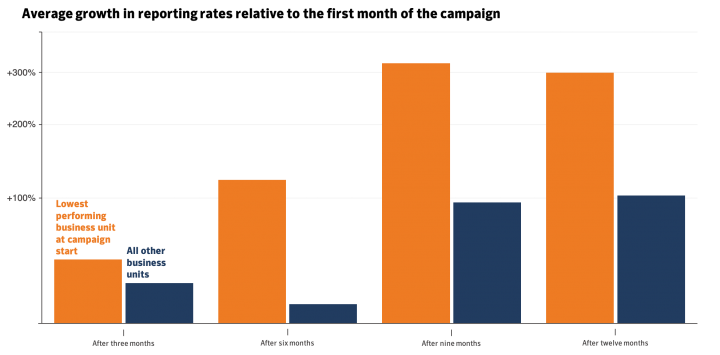
The gamification of the program drove great results. Some of the more technically astute teams were strong performers from the outset and remained there for most of the campaign. What mattered more to us was whether the worst performers improved over time.
The graph below shows the growth in positive reporting rates of the business unit which had the lowest reporting rate at the beginning of the campaign. The SVP that leads this business unit took decisive action and used weekly newsletters to encourage team performance, whilst members of their staff took it upon themselves to organize and deliver classroom-based workshops for their peers. After several months of steady improvement, this business unit was consistently in the top 3 (of 10) on positive reporting by the latter stages of the campaign.
Making Reporting Easy
While positive reporting rates grew steadily throughout the 12-month campaign, we achieved the most rapid growth after providing users with tools that simplify the process of reporting suspicious messages.
We call it the ‘Phishing Tacklebox’. The Tacklebox ensures help is only a click of a mouse or tap of a screen away for any user unsure about the legitimacy of an email.
The Phishing Tacklebox is a custom add-in integrated into users’ Outlook clients across all corporate devices (desktops and mobiles). One feature (‘Inspect Headers’) allows users to parse an email header to better determine how trustworthy the message is. The tool highlights important information that can be pulled from the header – whether it originated from an external network, the server it was first sent from and the outputs of various email security authentication checks. All of this information was linked off to further reading resources where a user could learn more. At all times we stressed that users should not rely solely on a single indicator to determine the trustworthiness of a message, but we felt it important to provide options for those eager to learn more about email security.
The Tacklebox ensures help is only a click of a mouse or tap of a screen away for any user unsure about the legitimacy of an email.
The second feature (‘Report Email’) is – as you’d expect - for those users unsure about the trustworthiness of the email who wish to report it to the security team. We adapted the typical workflow of ‘one-click reporting’ solutions to ease the burden of SOC analysts responding to these reports. Reporters would see a confirmation prompt upon clicking the icon (to avoid an influx of accidental reports into the SOC), as well as toggles for whether they needed a response from the SOC or wanted the email removed from their inbox after the report was sent. Users could also set sticky preferences for future reporting.
We’ve been very impressed with user uptake of the Tacklebox. Power users love having raw and parsed email header information available in one click. And in the last two Hall of Phame simulations, the share of positive reporting using the Tacklebox rose from 37% of reports to 51%. This demonstrates that with sustained hands-on training, comms, and tools developed with user convenience in mind, users gain greater confidence in playing an active role in the security program.
Next Steps
With this 12-month campaign behind us, we have a great baseline of data about which users and groups are most susceptible to social engineering alongside the attacker tradecraft they are more or less susceptible to.
Now that our users are highly engaged, the focus of our phishing training can shift to current attacker tradecraft (vs historical), and we can pay greater attention to a broader program of remedial training for at-risk users.
We’ll go into detail about our remedial program in the next blog post.

5 Must-Have Elements to Include in Your Security Awareness Program
When your aim is to change the culture of an organization, awareness isn’t enough








We encourage you to share your thoughts on your favorite social platform.