What We’re Doing to Fight the Scourge of Cyber Stalking
Here’s how we’re battling “creepware” to protect victims of stalking and intimate partner violence
It’s a sad fact of life that technology can be used to stalk, harass and harm people’s partners, acquaintances and even strangers. MIT Technology Review cites the domestic-violence charity Refuge as saying that approximately 95 percent of the cases it sees involve technology-based abuse of some kind.
Mobile devices are often the platform on which abusers deploy software we call “creepware” – apps that can be used to abuse, stalk, harass and spy on others, frequently to enable intimate partner violence. But it’s been very hard to detect creepware apps, in part because they often have less objectionable use cases, or at least pretend to, as in the case of an app that abruptly changed its name from “Girlfriend Cell Tracker” to “Family Locator for Android.”
A major challenge in detecting creepware is that apps that enable stalking and harassment are often careful about how they describe themselves.
Because of the seriousness of the problem, at Symantec we set out to how to detect creepware and protect victims and would-be victims from it. In concert with researchers at Cornell and New York University, we created CreepRank, which ranks the probability that any given app is used as creepware. We have incorporated CreepRank into Norton Mobile Security, which stops the covert surveillance apps it detects from being installed on people’s phones and warns of their presence if they are already there.
A major challenge in detecting creepware is that apps that enable stalking and harassment are often careful about how they describe themselves. While the occasional app does call itself “Girlfriend Tracker” or “Boyfriend Tracker,” apps are increasingly likely to choose strictly technical or innocuous-sounding names, even when designed for illegal uses. In addition, an overly prescriptive approach to discovering creepware would have limited the scope of our findings.
Types of Surveillance
We designed CreepRank for anonymized data about billions of app installations on 50 million mobile devices over years of data. We quickly discovered that people who install one abusive app are likely install many others as well. Latching onto this observation, we designed CreepRank around the insight expressed in the old Spanish proverb, “Tell me who your friends are and I’ll tell you who you are.” Accordingly, we applied CreepRank to millions of apps installed on 50 million phones, ranking each app according to its propensity to be installed alongside known abusive apps. The higher the CreepRank, the more likely the app is to be used for abusive purposes. A manual examination of the apps with the highest CreepRanks revealed well over 1000 apps used for a variety of malicious purposes.
The most common form of creepware, we found, are surveillance apps used to spy on others and track their locations, phone use, texts and more. They are often used for stalking and can lead to intimate partner violence. Some of the apps can spy on another person's texts by uploading them to the cloud, and then reading them. Some track people’s precise locations or use geofencing to alert a stalker that the victim has left the house. Some can read people’s call logs or record people’s calls and forward them to the harasser. Others can remotely turn on the microphone on a victim’s phone, record whatever is happening, and forward that to the stalker.
The most common form of creepware, we found, are surveillance apps used to spy on others and track their locations, phone use, texts and more.
Many of these surveillance apps are extremely troubling and are used to stalk, harass and commit violence. People who use them are very controlling and very abusive. They use the apps not just to track their victims, but also to isolate, intimidate and control them.
In a horrifying case, a Florida man killed his wife and two children several days after he installed surveillance software on his wife’s phone and used it to see her texts and photos she had been sharing, according to the New York Times. The man has been sentenced to three consecutive life terms.
Norton Mobile Security detects these types of surveillance apps and won’t let them be installed on a phone and will remove them if they’re already installed. You can see a screenshot, below. (For now, it’s available for Android devices, but we are working on incorporating it into our iOS app as well.) We have also worked with app stores to get surveillance apps removed so they’re not readily available.
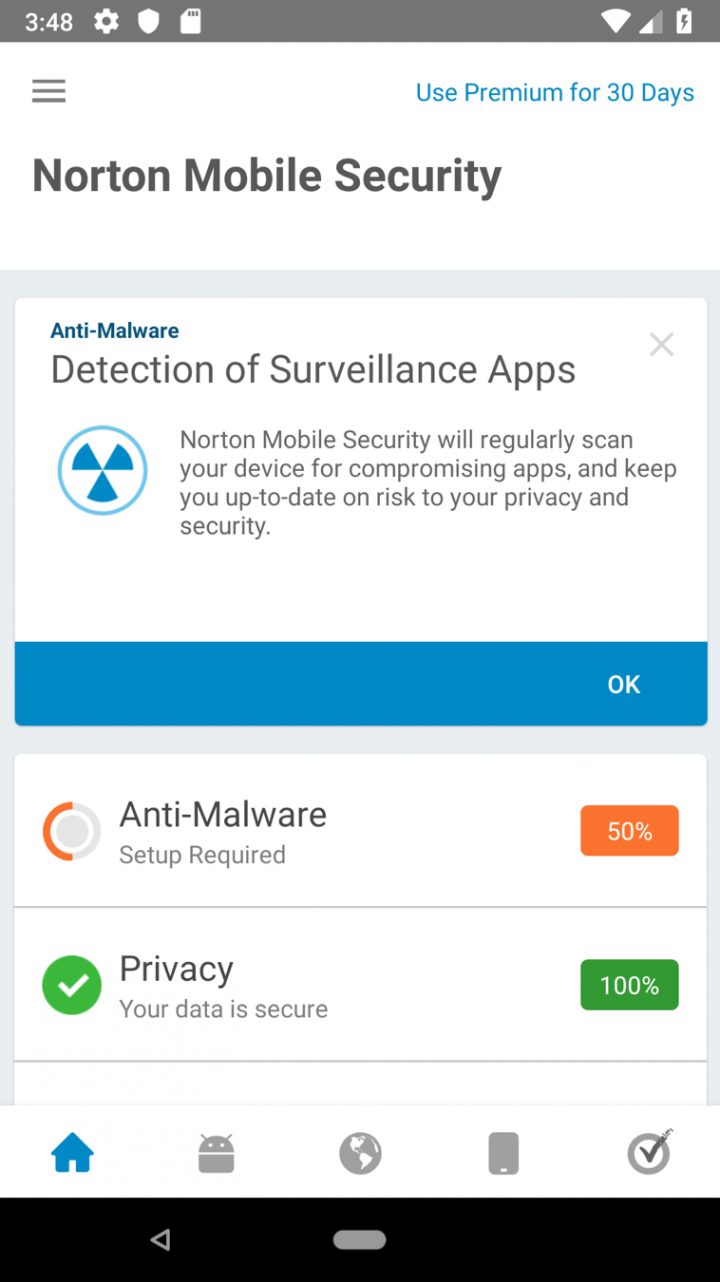
Using CreepRank we have also identified other types of stalking, harassment and abusive apps, including “bombing” apps that let abusers send hundreds or thousands of text messages simultaneously to a victim, spoofing apps that hide the true phone number and identity of the harasser, apps that can be used to create fake suggestive images and harm a victim’s reputation, and other types of interpersonal attack apps. We are incorporating their CreepRank into Norton Mobile Security so they can be removed from victim’s phones, and have worked with app stores to get hundreds of abusive apps removed from distribution.
We’re working hard to take creepware out of the hands of abusers, and to give victims and potential victims the tools to protect themselves and be free of harassment, violence and attacks. As we do more, I’ll keep you informed, so check back here regularly.

The Evolving Challenges of Mobile Security
Why last year’s mobile defense technology is no longer enough








We encourage you to share your thoughts on your favorite social platform.