How to Take Protection Against Phishers Up a Notch
Cyber criminals are getting cleverer, deploying phishing variants to confuse defenders. But now there’s a way to detect and blunt their forays earlier than ever
Give cyber criminals credit for persistence. When defenders close off one line of attack, attackers learn through experience to find other ways to disguise their tracks and steal into your network undetected. Nowhere more so than when it comes to phishing where the rates have hovered in the 1 in 2,000-3,000 email range for the last 10 months according to our latest intelligence briefing
Scammers send out a variety of fake e-mails in a bid to deceive unsuspecting victims into sharing their personal or corporate information. And it’s having an effect with phishing attacks causing billions of dollars in damages each year.
Unfortunately, the advantage often lies with attackers and most attack victims visit phishing websites within the first few hours of their launch where they are tricked into clicking on malware-laden links.
The challenge to defenders is made that much harder because approximately a million new malware variants get created every day. The bad guys also deploy a variety of techniques to try and bypass inspections to carry out phishing attacks. Last quarter, for instance, we saw an attack where a URL went to a PDF. Inside the PDF was another link and it was that link that was trying to steal the credentials of someone in the organization.
So, when it comes to defending against phishing threats, the battle ultimately turns on how long it takes an organization to recognize variants and block the attack. Speed and accuracy are decisive in the race to prevent cyber criminals from inflicting major damage.
Over the years, security companies have tried a combination of different technologies to combat the challenge posed by phishing websites. Other vendors have approached the phishing challenge by using reactive blacklists as way to understand which links are bad. At that point, they push down those blacklists onto an email security solution. Fine and well. But it’s a reactive approach that lets attackers set the agenda.
We’ve also been busy trying to figure out possible solutions and I’m happy to share our progress. Symantec has found a new way to recognize phishing attacks faster and more effectively than ever before.
Advanced Phishing Variant Detection to the Rescue
Since the early 2000s, we’ve used a Symantec technology called URL Link Following to scan hyperlinks to determine whether they are being used for spam, phish or malicious purposes. At the time of a scan, it extracts the URL from a message and lets us follow the link to its destination to determine whether there’s a danger.
The problem we encounter with some phishing attacks nowadays is that we have to have all the indicators present to determine whether the link is malware, phishing or spam. This isn’t a trivial job. From an email perspective, it’s vital to balance detecting phishing sites while not blocking someone’s legitimate email. For instance, often the link will look very similar to a legitimate email or URL.
So, we review a variety of different indicators. For instance, we will examine the end destination page and look at static streams on the page itself. If the page asks the user input their personal details, that’s a clear indication the website is phishy.
But this becomes something of an arms race as cyber criminals continue to come up with new ways to try and get around our measures and stop us from being able to detect their handicraft. Sometimes all it takes is for them to make only slight variations and that’s enough to prevent us from discovering the problem.
That’s where Advanced Phishing Variant Detection comes in.
Advanced Phishing Variant Detection uses established computer science techniques to allows us to compare websites to those that we’ve already identified as phishing. That also proves highly effective helping us detect slight variations in an actual downloaded page.
We can follow a questionable link. When it leads back to a phishing site, we can download that phishing site. There may only be slight variations from one phishing site to the next. Cyber criminals might try to throw us off the scent by adding obfuscated content in the page or use different phrases in the page to cover their tracks.
But using all the indicators that we’ve identified and comparing to sites that we’ve not indicated as phishing helps us to make a more accurate determination. The value here is that we’re always evaluating at the time of scan and making the judgment call about whether a website is phishing in real time.
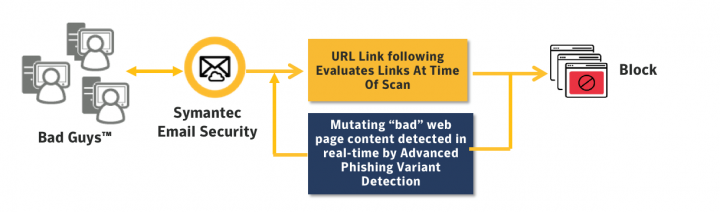
We’ve now integrated Symantec’s Advanced phishing variant detection technology into our cloud and email security products to take protection up a notch. But this isn’t the final coda. It’s been quite successful since we completed the first phase of a product integration in the 4th quarter of last year. We’ve already seeing URL detection improve by up to 2%. At first blush, that might not sound like a lot but it's resulted in 250,000 additional messages getting blocked over a 30-day period. Over the course of coming months, we’re expecting to do even better and develop more indicators that help us zero in on the malicious stuff sent over the transom.
It’s clearly too soon to celebrate victory in the battle against phishing. But keep faith in the future because we’re striding closer all the time.







We encourage you to share your thoughts on your favorite social platform.