The Missing Piece of the APT Security Puzzle – Symantec Endpoint Threat Defense
Active Directory is the most targeted asset in the organization. Here’s what you can do about it
For attackers, Active Directory is the most targeted asset in the organization.
It takes only one compromised domain connected endpoint to take control of an organization’s vital assets. Active Directory (AD) is a database exposed, by design, to any domain connected user, meaning all identities and resources on a corporate network are visibly exposed, making AD the number one target for attackers. With just a few queries to Active Directory from a compromised endpoint, an attacker can obtain all information needed to steal domain admin credentials and move laterally to high value assets.
OK, I’m Listening. But is it Really that Common?
Targeting Active Directory is more common than you might think.
While nine out of ten companies around the world use Microsoft Active Directory to control and maintain internal resources, companies nowadays are focused on defending endpoints, applications, servers, mobile devices, and networks. That leaves Microsoft Active Directory as the least protected asset in the company. And as documented by MITRE, attackers exploit this extensively:
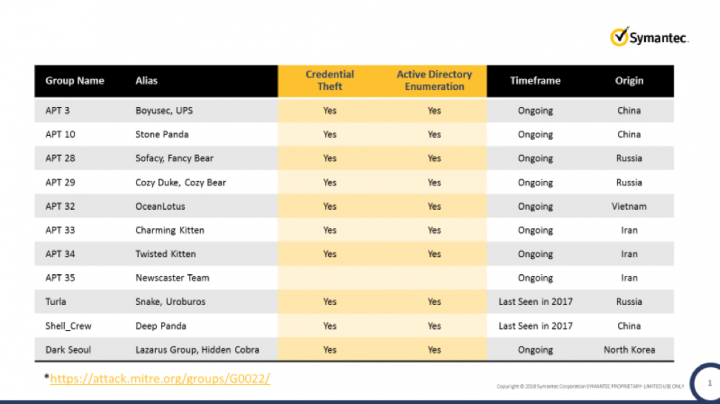
Anatomy of an APT Attack Using Active Directory
So, how do attackers exploit Active Directory to conduct APTs? Attackers start on an endpoint. Once they gain a foothold on a domain-connected endpoint, they perform reconnaissance of the Active Directory database to gain visibility into all domain-connected resources, including servers, endpoints, applications, and users.
Their next step is to steal domain privileged credentials and move laterally. With stolen credentials, attackers are granted full and stealth access to all servers, applications, and computers in the organization – with the end goal of stealing or encrypting data. For an attacker, 7 minutes is all it takes, post-endpoint compromise, for them to achieve domain dominance, essentially granting them the keys to the kingdom.
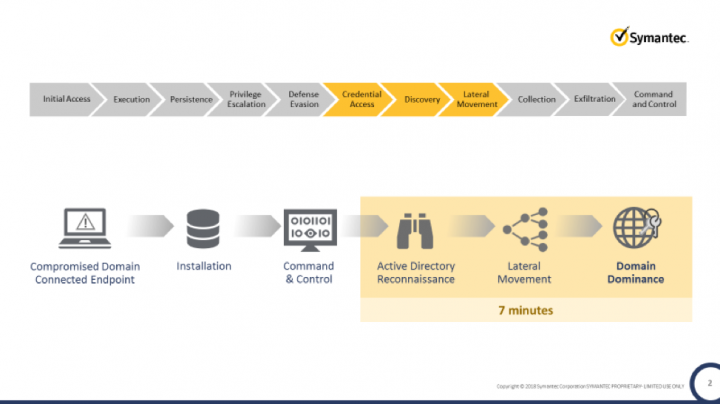
The Failure to Protect Active Directory
The industry has offered user behavioral analytics, network monitoring, and privileged access management tools as compensating control for attackers compromising domain user and admin accounts. However, these tools and methods focus on detection too late in the attack cycle. Attackers’ use of trusted applications and built-in tools to learn about the environment, steal credentials and move laterally, as opposed to use of malicious binaries, makes detection and mitigation on-time, nearly impossible. Therefore, it’s important to look for security solutions that protect Active Directory by containing attackers as early as possible in the attack cycle before they can gain a foothold on the domain and establish irreversible persistence.
Time for a New Approach, New Solution
Symantec’s solution approach entails containing attackers as early as possible – at the endpoint - before they have any opportunity to persist on the domain. The moment an endpoint gets compromised Endpoint Threat Defense for Active Directory starts working to thwart domain admin credential theft and lateral movement.
Using AI-driven intrusion detection this solution autonomously learns the organization’s Active Directory structure in its entirety and uses this data to create an authentic and unlimited obfuscation. All Active Directory queries from the endpoint are evaluated and obfuscated in runtime based on context.
With obfuscation, a perspective of the domain-connected assets compromised is projected to the attacker; the attacker gives themselves away, while interacting with assets or attempting use of domain admin credentials on the solution’s perception. Because Threat Defense for Active Directory relies on automated obfuscation of Active Directory assets to massively increase the number of assets presented to the attacker from the endpoint, the odds of an attacker selecting a legitimate asset is 1%, which means this solution provides a 99% rate of success stopping an attacker on their first move.
To learn more about Endpoint Threat Defense for Active Directory, click here









We encourage you to share your thoughts on your favorite social platform.