BEC Scams Remain a Billion-Dollar Enterprise, Targeting 6K Businesses Monthly
Symantec examines the latest trends and themes in BEC scams in the last 12 months.
Business email compromise (BEC) scams are not going away anytime soon. For such a relatively low-tech type of financial fraud, it has proved to be a high-yield and lucrative enterprise for scammers.
BEC scams—also known as email account compromise (EAC), CEO fraud, or whaling—have been around since at least 2013. Between October 2013 and May 2018, more than $12 billion in domestic and international losses were attributed by the FBI to BEC scams.
According to the FBI's latest Internet Crime Report (ICR), losses from BEC scams amounted to almost $1.3 billion in 2018. This is double the losses in 2017, which stood at $676 million.
| Year | Victim count/complaints | Victim losses |
|---|---|---|
| 2014 | 1,495 | $60,294,162 |
| 2015 | 7,837 | $246,226,016 |
| 2016 | 12,005 | $360,513,961 |
| 2017 | 15,690 | $676,151,185 |
| 2018 | 20,373 | $1,297,803,489 |
In 2018, the FBI's Internet Crime Complaint Center (IC3) also received 20,373 BEC-related complaints, which is up from 15,690 complaints in 2017. Aggregate losses from internet-enabled theft, fraud, and exploitation reached $2.7 billion in 2018, and losses from BEC scams accounted for almost one-half of this figure. The FBI also said in a July 2018 public service announcement that, based on the financial data, banks located in China and Hong Kong were the primary destinations of fraudulent funds, while financial institutions in the UK, Mexico, and Turkey were also prominent destinations.
The good news is that the IC3's Recovery Asset Team (RAT), which was formed in February 2018, has successfully recovered more than $192 million lost to BEC scams, representing a recovery rate of 75 percent. The RAT reportedly dealt with 1,061 incidents that caused losses of more than $257 million.
Given this dramatic rise in actual BEC-related losses as well as complaints, we wanted to examine BEC scams more closely. Is the number of BEC emails sent daily growing? How many businesses are targeted by BEC scams each month? Which regions are most targeted by these scams?
BEC statistics at a glance
Daily activity
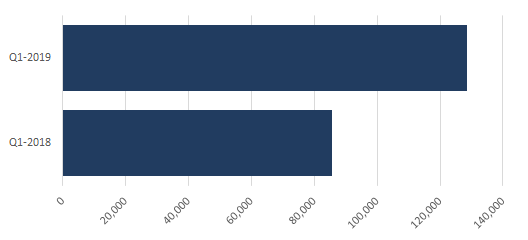
According to Symantec telemetry, the average daily volume of BEC emails was significantly higher in the first quarter of this year than in the same period last year. From January to March 2018, the average daily BEC email volume was 85,816, while from January to March 2019, the average daily volume was 128,700—a 50 percent increase.
Average number of businesses targeted per month
We found that an average of 6,029 organizations were targeted by BEC emails per month during the last 12 months, from July 2018 through June 2019. BEC scams could have potentially affected this many businesses monthly were these attacks not blocked.
This indicates that BEC scammers have slightly reduced their targets, as an average of 6,089 businesses were targeted per month in the previous 12 months.
Average number of emails received per targeted business
We also found that businesses received an average of five BEC scam emails each month during the past 12 months. This means each business had a 17 percent chance of getting at least one BEC email per month. In the previous 12 months, an organization would have received an average of four BEC emails per month.
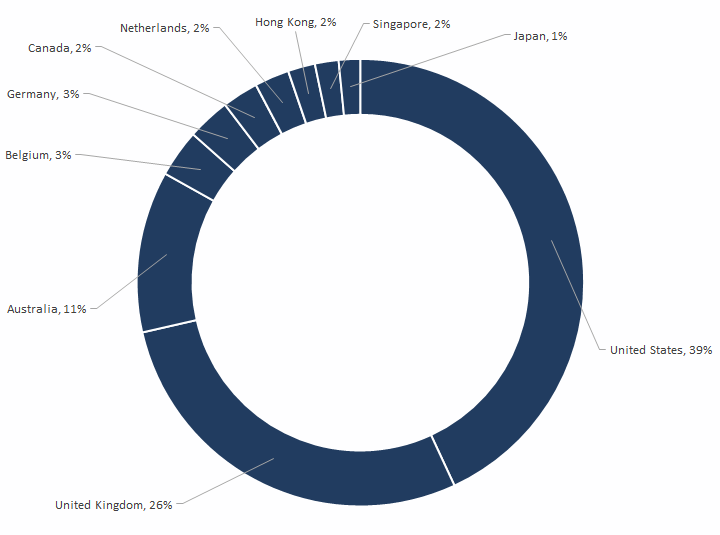
Top 10 victim regions
In which regions are these targeted businesses located? The top 10 regions targeted by BEC scammers in the last 12 months are led by the U.S. (39 percent), followed by the UK (26 percent), Australia (11 percent), Belgium (3 percent), Germany (3 percent), Canada (2 percent), the Netherlands (2 percent), Hong Kong (2 percent), Singapore (2 percent), and Japan (1 percent).
Top 10 BEC email subjects by country
One interesting metric we looked at was the most popular Subject lines used in BEC emails in the last 12 months and in which victim regions these were used. BEC scams targeted at the UK and the U.S. were mostly labeled "Important," while most BEC scams that hit Australia, Spain, France, and Germany had payment-related themes.
| Country | Subject line | Count |
|---|---|---|
| UK | IMPORTANT | 20,234 |
| U.S. | IMPORTANT | 11,930 |
| Australia | PAYMENT | 4,292 |
| Japan | YOUR RECEIPT FROM APPLE | 3,513 |
| Belgium | RE: U HEEFT RECHT OP EEN LAGERE ENERGIEREKENING IN 2018 ! (YOU ARE ENTITLED TO A LOWER ENERGY BILL IN 2018 !) | 3,308 |
| Singapore | CONFIDENTIAL | 2,520 |
| Spain | NOTIFICATION OF PAYMENT RECEIVED | 1,765 |
| Canada | URGENT | 1,758 |
| France | PAYMENT DUE 8 DEC. | 924 |
| Germany | PAYMENT | 921 |
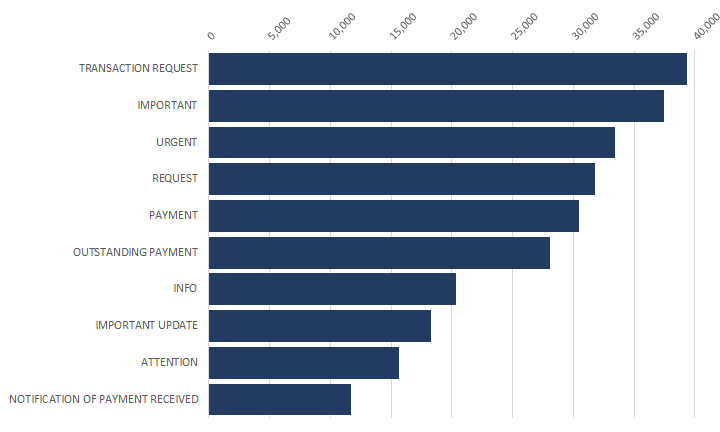
Top 10 BEC keywords
We also looked at the 10 most popular keywords used in BEC emails in the last 12 months. "Transaction request" topped the list with 39,368 instances observed, followed by "Important" (37,477) and "Urgent" (33,391). There were three iterations of "Payment" that rounded up the top 10, including "Outstanding payment" and "Notification of payment received."
Almost all of the keywords are meant to call the attention of the recipient or induce a sense of urgency with finance-related themes.
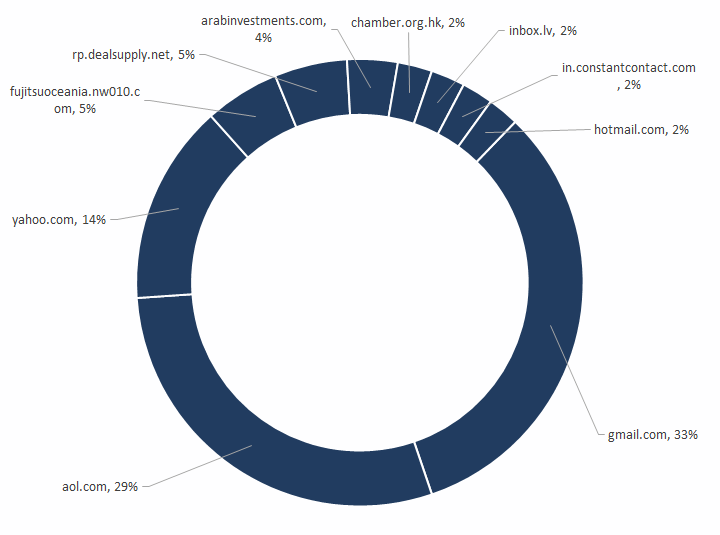
Top 10 BEC sender domains
Email scammers have been known to use so-called cousin domains—for example "[email protected]" instead of "symantec.com". BEC scammers appear to have gone easy on these cousin domains in the last 12 months, and have gone back to using free web accounts and web mailers, such as gmail.com, yahoo.com, aol.com, and inbox.lv. Using and/or spoofing such legitimate domains also lends legitimacy to the scam.
Four popular email services—including Gmail, AOL, Yahoo! Mail, and Hotmail—are among the 10 top most abused domains from which BEC emails are sent, with Gmail and AOL bearing the brunt. What's most surprising here is that AOL, which experienced a sharp decline in subscribers back in 2007, apparently remains a top choice for BEC scammers.
BEC email themes
Let's take a closer look at the BEC emails themselves. We have noted recent changes in BEC message composition, with scammers building on previous ideas, getting more creative, and using newer themes, such as:
- Requests to buy gift cards, both physical and electronic
- Requests to update salary or direct deposit account details
- Requests for personal/work cellular/landline number to provide further instructions
This observation aligns with that of the FBI's, as the IC3 report found that in 2018, there was an increase in the number of BEC complaints requesting victims purchase gift cards. According to the report, the victims received a spoofed email, call, or text from a person in authority requesting that the victim purchase multiple gift cards for either personal or business reasons.
Specifically, Symantec's Security Response team observed that the 10 most popular themes carried by BEC emails in the last 12 months include:
- Apple iTunes gift cards (physical) to employees: The scammer requests the potential victim to buy Apple iTunes physical gift cards from a store. The scammer states that these cards will be distributed among employees of the same organization.
- Apple iTunes e-gift cards to employees: The scammer requests the potential victim to buy Apple iTunes e-gift cards for employees.
- Amazon gift cards: The scammer requests the potential victim to buy Amazon gift cards.
- Generic gift cards for clients/partners: The scammer requests the potential victim to buy physical gift cards to be distributed to partners.
- Personal/work cellphone number request for further payment instructions: The scammer asks the potential victim to provide their personal/work cellular number so that the scammer can text payment instructions via messages.
- Same-day wire payment: The scammer asks the potential victim about the same-day wire payment process.
- Probing for international transfer limit: The scammer probes the potential victim for the daily limit on international transfers.
- Set up payment for vendor/supplier: The scammer instructs the potential victim to set up a payment for vendor/supplier.
- Salary issue (direct deposit/salary account assistance): The scammer tells the potential victim that there has been an issue with a direct deposit or a salary account, and that they need to update their account details.
- Urgent payment needed while in a meeting/conference: The scammer demands an urgent payment while they are unable to receive calls as they are supposedly in a meeting/conference.
The future of BEC
BEC scams are said to have begun with the hacking or spoofing of CEOs' or CFOs' email accounts, with scammers sending fraudulent emails typically to a company’s finance department an' tricking employees into making wire transfer payments. A combination of email spoofing, computer intrusion, and social engineering is required to pull off this type of scam.
These scams have been constantly evolving, with scammers getting craftier and growing more sophisticated each year. This year alone, we have seen Facebook and Google getting defrauded of $100 million; Chinese fraudsters stealing $18.6 million from the Indian arm of an Italian engineering company; and BEC gangs expanding geographic targets and identifying new victims, such as universities, the Salvation Army, and Boy Scouts of America. Even a small church in Ohio was not spared.
What lies ahead for BEC scams? As artificial intelligence (AI) and machine learning (ML) become more developed, we may very well see BEC scammers adopting these technologies in the near future to make their attacks even more convincing. Both ML and AI could be used to power audiovisual "deepfakes" that target or impersonate C-Suite executives. Already we have seen deepfakes that use only audio, as it is easier to leverage than both audio and visual elements.
A BEC scammer using ML/AI could target an organization's senior financial executive or employee who has direct access to the CEO and who could authorize money transfers. When the employee tries to verify the request, the scammer might use audio featuring the CEO—such as earning calls, YouTube footage, TED talks, and other previous recordings—to fool the employee into believing it is indeed the CEO's voice on the other end ordering the transfer. The employee could then execute the request fully believing it was legitimate. While this is a scary prospect, future BEC scam scenarios may just play out this way.
Mitigation
Symantec recommends the following best practices to protect your organization from BEC scams:
- Submit BEC samples to help improve protection against these scams, as sharing information allows organizations to quickly detect and stop these attacks.
- Question any emails requesting actions that seem unusual or aren't following normal procedures.
- Don't reply to any emails that seem suspicious. Obtain the sender's address from the corporate address book and ask them about the message.
- Use two-factor authentication (2FA) for initiating wire transfers.
- Conduct end-user awareness training to raise overall awareness of BEC scams among employees.
- Keep employees educated on the latest threats so they remain vigilant against dangers in their inboxes, which is still the primary means of communication in corporate settings.
- Deploy BEC controls that include automated email sender authentication and impersonation controls that monitor susceptible employees' emails.
- Isolate the threats quickly to prevent them from infecting individual machines or the network.
- Analyze potential threats using analytics technologies that can pick up on the subtle differences between clean and infected emails and identify indicators of compromise.
- Use digital signatures that prove the authenticity of an email sender. Have your executives, such as the CEO, use digital certificates to sign messages and ensure that recipients question emails appearing to come from their CEO when they are not digitally signed.
Protection
Symantec customers are already protected from BEC scams with the following solutions in place:
- Symantec Email Security.cloud Data Protection provides granular control to identify suspicious messages based on various indicators and helps to flag messages that are coming from outside the organization.
- Symantec Data Loss Prevention helps combat the data theft BEC scenario by seamlessly integrating with our Email Security solutions to detect emails containing sensitive information such as personally identifiable information (PII) that should not leave the organization.
- Business Email Scam Analyzer, a component of the Email Security.cloud Anti-Spam service, is an additional spam detection method that provides increased visibility into attacks that are related to BEC.
Special thanks to Vijay Thaware for his inputs on this blog.







We encourage you to share your thoughts on your favorite social platform.