DoubleHidden Malware Found Hiding on Google Play
Android malware uses multiple tricks to remain hidden on devices.
We have uncovered a new Android Trojan that uses several techniques to hide itself on devices, and remain in the Google Play Store. The malicious app collects device information and displays advertisements. However the functionality and behavior of this app could be easily extended to a wide range of other malicious purposes.
The malware (Android.Doublehidden) is localized in the Persian language. Its name translates to ‘Photograph by Fiery’ and it has a package name of com.aseee.apptec.treeapp.
The pattern of availability of this malicious app on Google Play suggests the author is attempting to remain under the radar. During October and November 2017, the app has been updated five times, alternating between a working legitimate photo editing app, and this self-hiding malicious non-app. As far as we can tell, the app developer ‘i.r.r developer’ publishes several other apps which are legitimate.
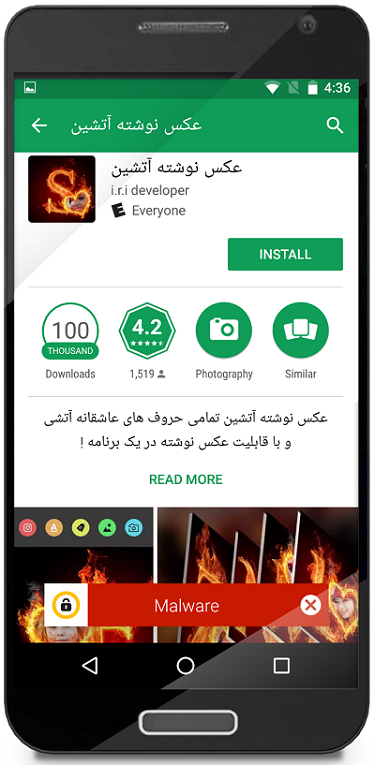
The app presents itself as a photo editing app, but immediately dupes the user and hides itself on installation. On launch, the app asks the user for Device Administrator permissions—a well-used approach for malware to gain a strong foothold on the device. In the subsequent user interface (UI) screen, the app displays a message which roughly translates as: “Unfortunately, this app does not work on your phone. After exiting, the application will be deleted.”
Although the app closes, the malicious functionality is already in place.
The app hides itself on the device using the following techniques:
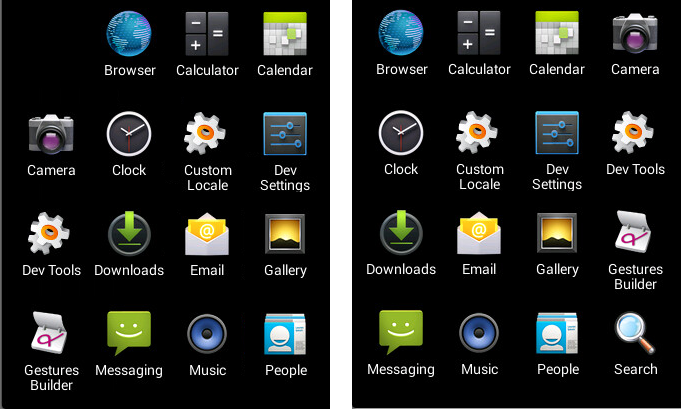
- The launcher icon is set to a transparent image with no app name. After installation, the app icon appears as a blank space on the home screen. In the settings, the app will appear as a blank entry wherever it is displayed.
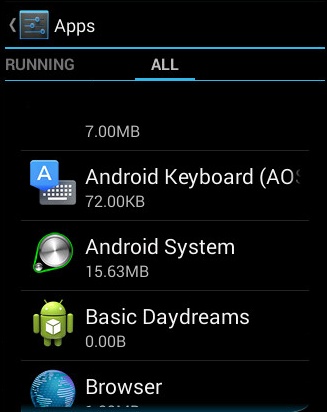
The app calls setComponentEnableSetting(). Once the app launches, it disappears from the app launcher (its icon no longer appears on the home screen).
The app leverages its position on the victim’s device to collect data and advertising revenue. The app collects user information to send to the malware authors. Google Cloud Messaging is used to push configuration information, including when to collect data and where to send it.
The malware may collect the following information:
- Device information, such as International Mobile Equipment Identity (IMEI) number, Mac address, device model, device brand, device screen
- Installed applications and timing of install/uninstall
- Activity/UI time for the malware
- Network connectivity (throughput while roaming/Wi-Fi-connected/carrier-connected)
- Device location
- All accounts listed in the Account Service
- Which application is running in the foreground
If the user gave the malicious application the Device Administrator permission, it will be more difficult to remove.
The malware also requests and displays advertisements on the device including suggestions for additional applications by using the OneSignal notification network.
If the user gave the malicious application the Device Administrator permission, it will be more difficult to remove, as the user will have to disable ‘Device Administrator’ for the app in the app settings (and remember, this entry is a blank row) to actually uninstall it.
Protection
Symantec and Norton products detect this malware as:
Mitigation
Stay protected from mobile malware by taking these precautions:
- Keep your software up to date
- Do not download apps from unfamiliar sites
- Only install apps from trusted sources
- Pay close attention to the permissions requested by apps
- Install a suitable mobile security app, such as Norton, to protect your device and data
- Make frequent backups of important data









We encourage you to share your thoughts on your favorite social platform.