Hidden App Malware Found on Google Play
The 38 applications hide their presence on devices while they perform their malicious activity.
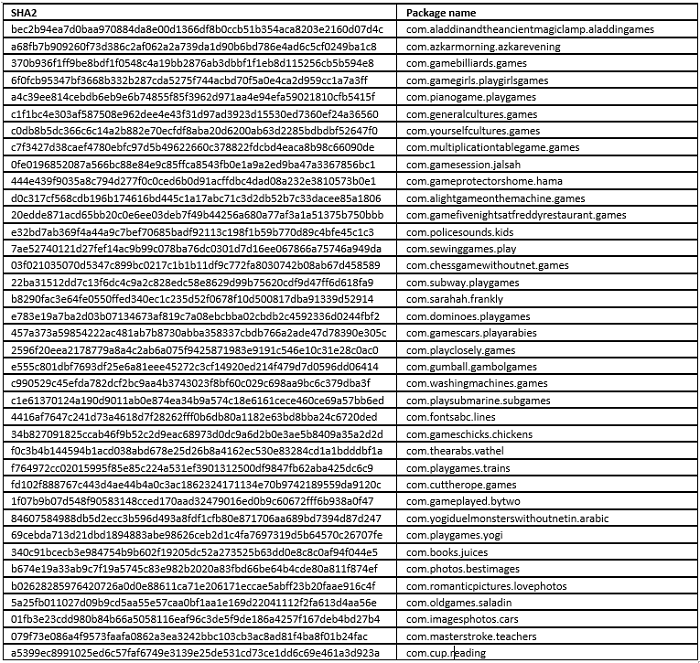
We recently discovered 38 malicious applications in the Google Play Store disguised as games and education apps. These malicious apps hide their existence on victims’ devices by removing their icons from home screen. They redirect victims to install another app on the Google Play Store that displays advertisements, and has minimal additional functionality. Furthermore, these malicious apps load several blog URLs in the background without the user’s knowledge.
The malicious apps (detected as Android.Reputation.1) were published to the Play Store in December 2017 by a developer called learningdevelopment, who listed the email address [email protected].

The apps claim to be games or education apps according to their display names on Google Play. To describe the behavior of these 38 malicious apps, we’ll take a look at one of them in more detail. Let’s look at com.aladdinandtheancientmagiclamp.aladdingames as an example.
When the app is installed on a device, it has a fake app name of “Helper”.

Once the app launches, it immediately invokes the setComponentEnabledSettings API to have its icon removed from home screen, while it is still running actively in the background.
Despite the inability to provide the functions it claims to have, the malicious app forcefully redirects victims to install another app on the Play Store once it has been launched. The promoted app is named “Change my voice”, has the package name com.ModifySound.VoiceChanger, and it is developed by TopTech. Although the app does have simple functionality to modify voice recordings, it also displays a large number of advertisements.
The URLs lead to various blogs and it is likely the app is being used to increase web traffic to these sites.
While staying undercover, the malicious app has a background service that constantly checks the device’s network connectivity status. Once network connectivity is available, the app checks if the compromised device has installed any of the previously mentioned 37 malicious apps. If none of them are present, the app will load several URLs in the background. The URLs lead to various blogs and it is likely the app is being used to increase web traffic to these sites.
So far, the majority of users downloading these apps seem to be located in the U.S., U.K., South Africa, India, Japan, Egypt, Germany, Netherlands, and Sweden. The presence of the apps on the Google Play Store and the seemingly legitimate app names and descriptions allowed the apps to be downloaded onto at least 10,000 devices. Symantec has notified Google about these apps and they have been removed from the Play Store.
Protection
Symantec and Norton products detect these malicious apps as:
Mitigation
Stay protected from mobile malware by taking these precautions:
- Keep your software up to date
- Do not download apps from unfamiliar sites
- Only install apps from trusted sources
- Pay close attention to the permissions requested by apps
- Install a suitable mobile security app, such as Norton or SEP Mobile, to protect your device and data
- Make frequent backups of important data









We encourage you to share your thoughts on your favorite social platform.