ISTR 24: Symantec’s Annual Threat Report Reveals More Ambitious and Destructive Attacks
ISTR Volume 24 is here, providing insights into global threat activity, cyber criminal trends, attacker motivations, and other happenings in the threat landscape in 2018.
Like flies to honey, miscreants are drawn to the latest cyber crime that promises quick bucks with minimal effort. Ransomware and cryptojacking have had their day in the sun with the get-rich-quick criminals, and now it’s formjacking’s turn. In this year’s Internet Security Threat Report (ISTR) Volume 24, we share the latest insights into global threat activity, cyber criminal trends, and attacker motivations.
This year's report notably reveals formjacking—where infected web servers skim off consumers' payment information—has emerged as the breakthrough threat of 2018. This threat showed explosive growth—and potentially big profits—at the end of the year, ensuring that it's likely to draw plenty of flies in 2019 and beyond. Often using third-party apps to infiltrate websites, formjacking also further illustrates the dangers of supply chain attacks, a growing weakness we first warned of in last year's report. Requiring only a few simple lines of code loaded onto a website, formjacking represents a significant threat to online retailers, or anyone who collects personally identifiable information from their customers via their website.
This year's report notably reveals formjacking—where infected web servers skim off consumers’ payment information—has emerged as the breakthrough threat of 2018.
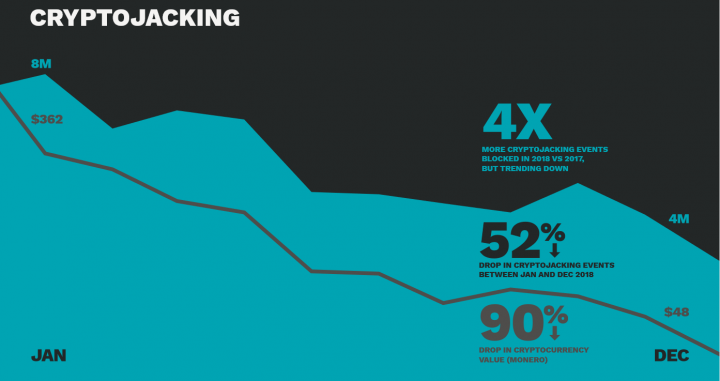
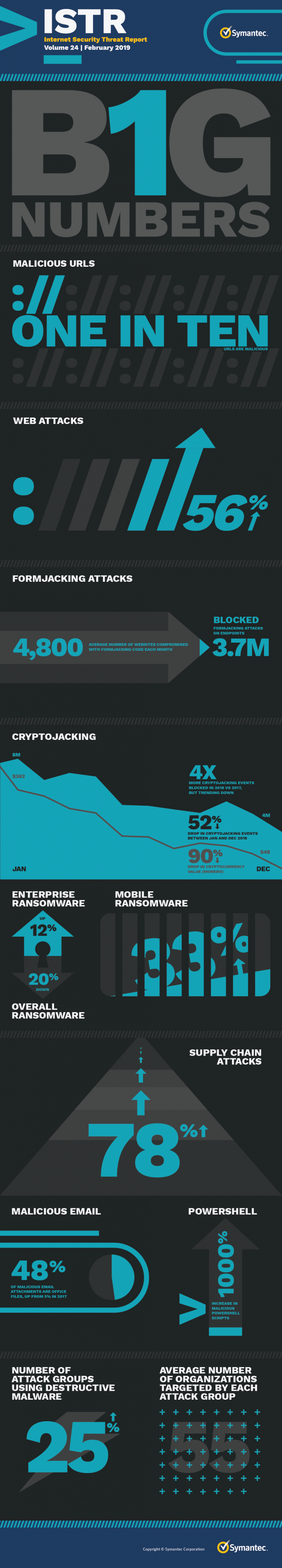
While no longer easy money, ransomware and cryptojacking have not gone away. The ISTR shows that with the decline in the value of cryptocurrencies, getting rich quickly through cryptojacking isn't as easy as before, and some attackers have moved on to more lucrative activities. But attacks are easy to instigate and manage, meaning those criminals playing the long game can still make money. Overall, Symantec blocked four times as many cryptojacking attacks last year than in 2017, and it continues to persist as an active threat so far this year.
Ransomware still offers the opportunity to make large sums of money. The SamSam gang is estimated to have made $6 million from their ransomware attacks. In fact, ransomware actors are increasingly narrowing in on enterprises, a high-value target. Ransomware infections grew in enterprise environments by 12 percent, while consumer infections declined. Consumers likely benefited due to their growing use of mobile devices, as criminals favor Office email attachments and PowerShell scripts—which don't work as well on mobile devices—to carry out ransomware attacks.
Yet the threat landscape is not just about crime and the quest for cash. Nation-states quickly adopted the internet for espionage and have used it for destructive purposes. Late last year, Shamoon notably reemerged after a two-year absence, deploying wiping malware to delete files on computers of targeted organizations in the Middle East. Nearly one in ten targeted attack groups now use malware to destroy and disrupt business operations, a 25 percent increase from the previous year. They also continue to refine their attack techniques, favoring spear phishing over zero days and using living off the land techniques to maintain a low profile and hide their attacks in a sea of legitimate IT processes.
Nearly one in ten targeted attack groups now use malware to destroy and disrupt business operations, a 25 percent increase from the previous year.
In fact, Symantec's Targeted Attack Analytics (TAA) technology discovered an attack group called Gallmaker in 2018 that needed no malware at all to infiltrate its targets. As attackers continue to use our own tools against us, detection must evolve from identifying malware to determining intent. Solutions based on machine learning and advanced artificial intelligence, like TAA, are increasingly critical for detecting attacks.
It seems that no one would willingly carry on their person a device that would allow someone to spy on their every thought, conversation, and movement. But the headlines of today indicate that we do. That device is our smartphone, and it's not just spymasters seeking out information about us. Even legitimate applications are spying on us. To help understand the risks involved, Symantec analyzed the top 100 Android and iOS applications in 2018 and found nearly half of Android apps and one-quarter of iOS apps requested location tracking. Apps asked for phone numbers, email addresses, access to cameras, microphones, photos, and any personal data stored on the device. That these applications want information about us—far beyond the needs of the application itself—is clear. What to do about it is not as clear, but it starts with understanding the extent of the problem.
No blog can sufficiently cover the threat landscape, but the ISTR can. For much more on the threat landscape, to dive into the numbers behind the latest trends, or register for one of Symantec's ISTR webinars, visit go.symantec.com/istr.








We encourage you to share your thoughts on your favorite social platform.