You Better Watch Out: Online and Offline Threats Endanger Payment Card Data
Cyber attackers are using old tricks and new to steal customers’ payment card details from retailers this shopping season.
As we enter the busiest shopping period of the year, both offline and online retailers and consumers are facing risks to the security of their payment card data.
Formjacking has surged in 2018—with Symantec blocking almost 700,000 formjacking attempts from mid-September to mid-November alone. This surge in formjacking is one of the big stories of 2018—with attackers like Magecart using supply chain attacks and other tactics to inject malicious scripts into websites to steal payment card information.
There have also been attacks on point-of-sale (PoS) systems in bricks-and-mortar stores this year, though none so far that compare to the mega breaches of earlier this decade, which saw tens of millions of credit cards compromised in a single breach.
Point of sale, point of weakness
According to recent research from Symantec’s Deepsight Managed Adversary and Threat Intelligence (MATI) team (published in the MATI report How Cyber Criminals Monetize Unauthorized PoS System Access And Stolen Card Data - 01 Nov 2018), on dark net marketplaces threat actors are advertising access to PoS systems at prices ranging from $12 for administrative access to one PoS machine, to $60,000 for access to a large corporate network containing thousands of PoS servers and terminals. Meanwhile, depending on its quality, payment card data on the dark web retails for between $1 and $175 per card.

The techniques used by PoS scammers remain straightforward and have not evolved greatly in the last number of years, with scammers still using “RAM-scraping” malware to steal payment card details.
This RAM-scraping malware works because of how data generally travels around retailers’ systems.
- Retailers generally use network-level encryption within their internal networks to protect data as it travels from one system to another.
- However, payment card numbers are not always encrypted in the systems themselves and can still be found within the memory of the PoS system and other computer systems responsible for processing or passing on the data.
- This weakness allows attackers to use RAM-scraping malware to extract this data from memory while the data is being processed inside the terminal rather than when the data is travelling through the network.
PoS cyber crime groups
Two high-profile actors in the PoS malware space are FIN7 and FIN6. FIN7 is a well-known group that is reported to have stolen more than $1 billion from companies around the world. FIN7 uses sophisticated spear-phishing emails to convince targets to download an attachment that then infects their company network with malware. The malware used by FIN7 is most commonly a tailored version of the Carbanak malware, which has been used in multiple attacks on banks. Companies compromised by FIN7 include well-known brands like Chipotle, Chilli’s, and Arby’s, with the group thought to have compromised thousands of business locations and to have stolen millions of credit card numbers.
FIN6 was first spotted in 2016 when it used the Grabnew backdoor and the FrameworkPOS malware to steal the details of more than 10 million credit cards. The group was also active in 2018, and was seen exploiting living off the land tools such as Windows Management Instrumentation Command (WMIC) and the Metasploit framework to execute PowerShell commands.
Both groups are believed to have made many millions of dollars selling the card details they steal on dark web marketplaces—with the Joker’s Stash marketplace appearing to be where most of these transactions take place.
However, a few factors have emerged in recent times that may impact the environment around PoS attacks, and the activity of these groups:
- Three members of FIN7 arrested: In August this year, the U.S. Department of Justice issued indictments against three Ukrainian nationals it alleged were members of FIN7: Dmytro Fedorov, Fedir Hladyr, and Andrii Kopakov. The three men reportedly had high-profile roles in FIN7: Hladyr as its systems administrator, and Fedorov and Kopakov as supervisors to groups of hackers. While FIN7 activity has continued to operate since these arrests, they could have an impact on the group’s activity going forward.
- Increased adoption of chip and chip-and-PIN: The increased adoption of chip in the U.S., and chip-and-PIN technologies globally, by payment card issuers has reduced the availability of “usable” payment card information in the criminal marketplace. If a threat actor compromises a PoS system that processes 50 percent cards that use chip-and-PIN then only 50 percent of the cards are usable, or saleable, for them. As chip-and-PIN technology becomes more commonplace around the world and reduces the number of PoS systems capable of producing card data that actors can monetize, Symantec’s MATI experts believe the price of unauthorized PoS access will decline, while usable stolen payment card information will increase in value due to its scarcity.
PoS attacks in 2018
One new actor we have seen engaged in malicious activity on PoS machines in 2018 is a group we have dubbed Fleahopper. Fleahopper has been active since at least July 2017. It is a financially motivated group that appears to be monetizing its victims by stealing information from infected machines running PoS software.
In the latter half of 2018, Fleahopper has been observed using the Necurs botnet to infect victims. It does this in two ways: through Necurs bots and through spam email, likely originating from the Necurs botnet. Symantec has observed Fleahopper delivering malware directly through Necurs bots, where the bots drop malware from Fleahopper onto machines already infected by Necurs. Machines that are not infected with Necurs may still be infected by Fleahopper through spam that comes from the Necurs botnet.
Spam emails that deliver malware from Fleahopper have been observed with malicious Microsoft .pub files attached. These .pub files download an installer for the malware used by Fleahopper, Trojan.FlawedAmmyy.
The Trojan.FlawedAmmyy RAT is a modified version of the publicly available remote access tool Ammyy Admin (Remacc.Ammyy). Although Trojan.FlawedAmmyy is not believed to be exclusive to Fleahopper, the group has been observed using Trojan.FlawedAmmyy to deliver its tools.
Once they've compromised an organization, Fleahopper has been observed dropping a number of files onto machines running POS software. Fleahopper installs a modified legitimate Remote Desktop Protocol (RDP) file onto infected machines running POS software. This gives Fleahopper remote desktop access to the infected machine that is separate from access through malware. Symantec has observed Fleahopper using this access.
Symantec has observed Fleahopper activity on machines in grocery stores, furniture stores, restaurants and a store selling men’s clothing. The group’s activity appears to be spread around the globe, with some activity seen targeting businesses based in the U.S. and the U.K.
Some of the other PoS malware that has been seen used by various groups in the wild in 2018 includes: RtPOS, Prilex, LusyPOS, LockPOS, GratefulPOS, and FindPOS.
Publicly reported attacks
There have been several publicly reported attacks on PoS systems in 2018:
- RMH Franchise Holdings, an Applebee’s franchisee
- Canadian restaurant chain Tim Horton’s
- U.S. restaurant chain Chili’s
- Saks Fifth Avenue, Saks Off 5th, and Lord & Taylor (these stores have the same parent organization: Hudson's Bay Company)
The compromise of Hudson’s Bay Company’s stores and Chili’s has been linked to FIN7. While these were significant compromises—the details of at least 5 million cards were compromised when the Hudson’s Bay Company stores were targeted—there have been no reports so far of PoS attacks this year affecting tens of millions of consumers.
This relative drop in activity in the PoS space compared to previous years could be down to the reasons mentioned above—the increased adoption of chip-and-PIN globally and upset in the FIN7 group. However, it may also indicate that attackers are looking at other ways to make money and get their hands on payment card details—for example, by turning to formjacking.
Formjacking
We first published research on formjacking at the end of September 2018, after a spate of high-profile attacks by the Magecart attack group. Among Magecart’s targets were Ticketmaster UK, British Airways, Feedify, and Newegg. One of its more recent targets was British electronics kit retailer Kitronik.
Formjacking is a term we use to describe the use of malicious JavaScript code to steal credit card details and other information from payment forms on the checkout web pages of e-commerce sites. It is not a new technique, but in the latter half of 2018, it has garnered a lot of attention due to some large campaigns, many of which have been carried out by Magecart. Recently released research has claimed that Magecart is not just one group—but rather approximately seven groups that are all engaged in similar activity.
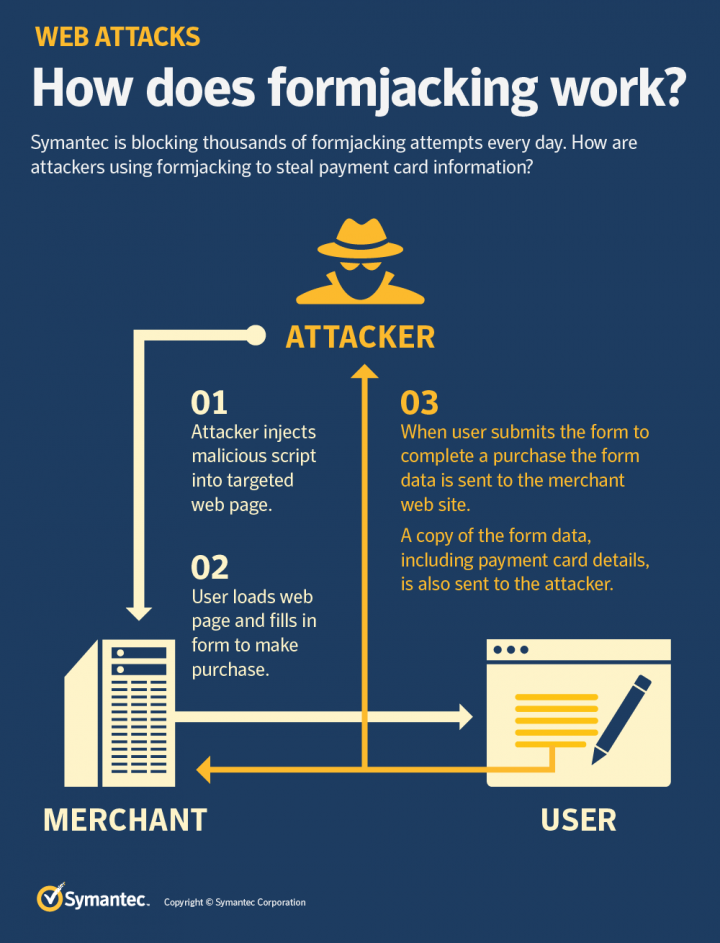
When a customer of an e-commerce site clicks “submit” or its equivalent after entering their details into a website’s payment form, malicious JavaScript code that has been injected there by the cyber criminals collects all entered information, such as payment card details and the user’s name and address. This information is then sent to the attacker’s servers. Attackers can then use this information to perform payment card fraud or sell these details to other criminals on the dark web.
In a two-month period, from mid-September to mid-November, Symantec blocked almost 700,000 formjacking attempts—with a clear upward trend visible as we approach the holiday shopping season.
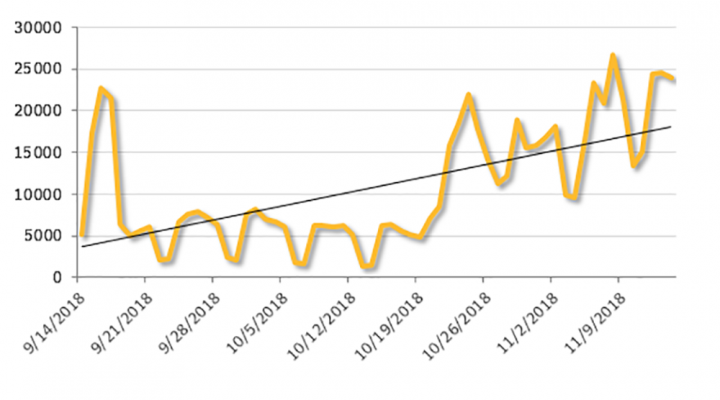
Much as we reported in September, these formjacking attempts target a wide range of e-commerce websites, including a fashion retailer in Southeast Asia, and another in Australia, a U.S. website selling jewelry, and another U.S. store specializing in outdoor gear and equipment. Suppliers of equipment for dentists, and online stores selling gardening equipment, were also among those targeted. These formjacking attempts continue to target a wide range of stores—ranging from small to large retailers in various countries around the world.
We detailed in our previous research how, in some cases, Magecart was using supply chain attacks to gain access to its targeted websites and carry out these formjacking attacks. The Magecart attackers injected malicious JavaScript code into Ticketmaster’s website after they compromised a chatbot from tech firm Inbenta that was used for customer support on Ticketmaster websites, for example. Magecart was then able to alter the JavaScript code on Ticketmaster’s websites to capture payment card data from customers and send it to their servers.
Dutch security researcher Willem de Groot has discovered since then that Magecart is also exploiting unpatched vulnerabilities in 21 Magento extensions used by online stores to gain access to websites. Magento is an open-source e-commerce platform. Magecart is using a series of URL paths to probe Magento stores in the wild for the vulnerable extensions, and injecting its malicious code into vulnerable websites.
As we approach the holiday shopping season, it is likely that we will see a ramping up of activity from actors out to steal consumers’ payment card details—both online and in retail stores worldwide.
Best Practices for Retailers
Formjacking
Victims may not realize they are victims of formjacking as generally their websites continue to operate as normal, and attackers like Magecart are sophisticated and stealthy and take steps to avoid detection.
Website owners should be aware of the dangers of software supply chain attacks, as these have been used as the infection vector in some of these formjacking attacks. Software supply chain attacks can be difficult to guard against, but there are some steps that website owners can take:
- Test new updates, even seemingly legitimate ones, in small test environments or sandboxes first, to detect any suspicious behavior.
- Behavior monitoring of all activity on a system can also help identify any unwanted patterns and allow you to block a suspicious application before any damage can be done.
Producers of software packages should ensure that they are able to detect unwanted changes in the software update process and on their website.
Website owners can also use content security policies with Subresource Integrity tags (SRI) to lock down any integrated third-party script.
Point of Sale
- Install and maintain a firewall to facilitate network segmentation.
- Change default system passwords and other security parameters.
- Encrypt transmission of cardholder data across open, public networks.
- Use and regularly update security software.
- Use strong authentication including two-factor authentication for remote systems.
- Test security systems, perform penetration testing, and implement a vulnerability management program.
- Maintain security policies and implement regular training for all personnel.
- Implement chip-and-PIN technology in your business.
- Implement system integrity and monitoring software to leverage features such as system lockdown, application control, or whitelisting.
Best Practices for Consumers
- Monitor your credit card bills so you will spot any suspicious transactions. You could even consider hiring the services of a credit monitoring company.
- Only shop from well-known, secure websites and stores that are more likely to have good security measures in place. However, even well-known stores fall victim to cyber criminals, so while this may reduce your risk of exposure it doesn’t eliminate it.
Threat Intelligence
Customers of the Deepsight Managed Adversary and Threat Intelligence routinely get intelligence about threats posed by cyber criminals, including details of PoS threats. These intelligence reports provide IOCs and detail adversary TTPs so that customers can better defend their environment from emerging threats.
Further Reading








We encourage you to share your thoughts on your favorite social platform.