Recent Surge in Spam Emails Carries Repackaged Adwind RAT to Evade Detection
A recent surge in spam emails totaling over one million a month is the result of attackers trying to spread newly repackaged Adwind RAT variants.
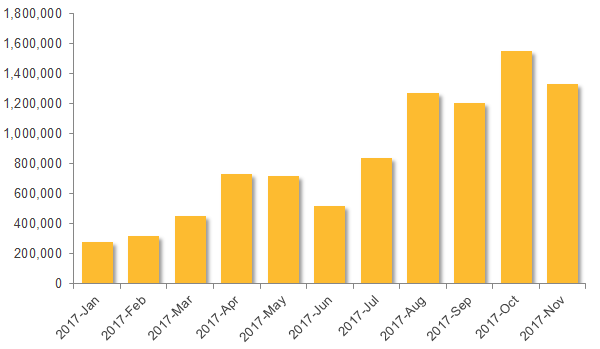
In August 2017, we began to see a surge of emails that were tied to the Adwind remote access Trojan (RAT). This increased activity led to a peak in October 2017, when we observed a large spike in the number of emails—totaling over 1.5 million—all attempting to deliver several variants of Adwind. In November, Symantec blocked over 1.3 million malicious emails related to this threat, this represents a small dip from October but the activity trend is still definitely upwards.
Adwind (Backdoor.Adwind) is a cross-platform, multifunctional RAT also known as AlienSpy, Frutas, Unrecom, Sockrat, JSocket, and jRAT. It was first discovered in 2013 and can be used for logging keystrokes, using the webcam, stealing information, downloading potentially malicious files, as well as a host of other nasty activities.
This high-volume campaign kicked off just in time for the holiday/shopping season, and the timing could be designed to give attackers more time to use any stolen credentials, as victims may let their guard down because they are more relaxed and engaged with other festive activities during this time.
Surge in malicious JAR files
The emails spreading Adwind come with JAR or ZIP file attachments. There was a surge in the number of malicious JAR files detected by Symantec, which peaked in October but actually began in August. The increase in malicious JAR detections corresponds with the recent Adwind campaign. The number of malicious JARs jumped from just over 840,000 in July to almost 1,272,000 in August. October saw 1.55 million, and November saw over 1.3 million detected.
The email surge that began in August is now well established, with the average volume now well above one million emails a month.
Adwind-spreading spam
The Adwind-spreading emails in this recent campaign are made to look like they originate from various service providers from industry sectors such as finance, telecoms, software, and logistics.
The emails come with subject lines containing keywords such as “Account statement”, “payment”, and “PURCHASE ORDER”.
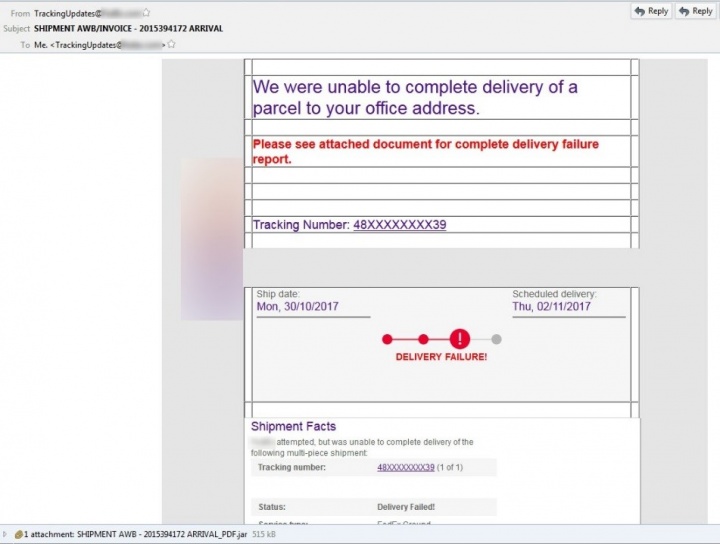
In some instances the email used (Figure.2) is made to look like it came from a well-known logistics firm. The email looks very convincing and could fool the recipient into thinking it is legitimate, however the email attachment tells a different story. The file is a fake shipping invoice made to look like a PDF file but is actually a JAR file containing the Adwind malware.
Other convincing emails appear to come from financial institutions, and some contain two attachments in case someone suspects that the JAR file may be malicious.
Current Adwind variant
The Adwind RAT has been around for quite some time but, in an effort to remain undetected, new variants contain very few identifiable strings and use a convoluted scheme involving layer upon layer of obfuscated function calls and classes wrapped inside numerous JAR files.
The wrapper file used in this campaign has multiple packages and classes with nested function calls within these multiple classes. The packages contain AES encrypted binary files with different extensions, such as .dll, .bin, and .so, to disguise themselves.
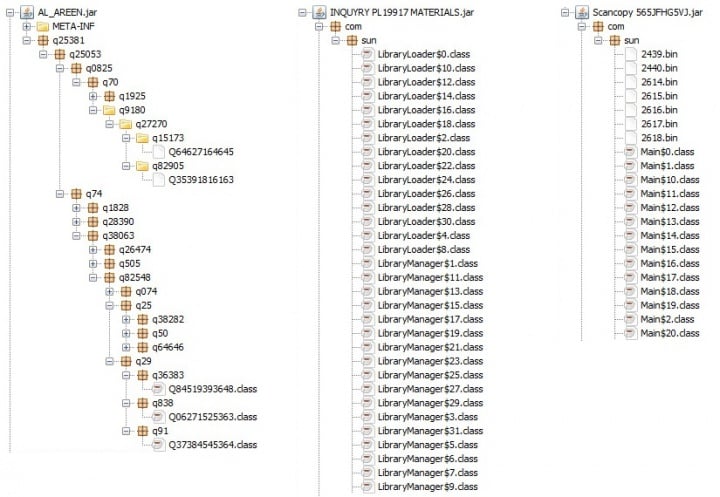
All three variants shown in Figure.3 are different in terms of obfuscation but the functionality remains the same.
Peering into the JAR
Once executed, the JAR files drop a payload JAR file with a random name and extension. The payload JAR is dropped in a randomly named directory and executed. The threat then runs VBS scripts in order to fingerprint the compromised computer. It also uses the Windows Management Instrumentation (WMI) interface to get details of any installed firewall or security products.
The threat then sets registry entries to disable System Restore and set Image File Execution Options for many security products and reversing tools to svchost.exe so that the tools cannot start. It also starts ending processes related to monitoring tools. The threat also connects to its command and control (C&C) server (we observed Adwind connecting with 174[.]127[.]99[.]211 but similar IP address ranges have also been used).
The payload JAR is similar to previous versions of Adwind and can be decompiled and reverse engineered using Bytecode Viewer or Java Decompiler and freely available Adwind decryptors.
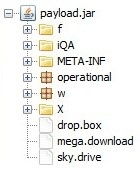
The important files here are those that provide further information on the threat’s configuration:
- drop.box - RSA private key
- mega.download - Encrypted configuration file
- sky.drive - AES key to decrypt data in mega.download
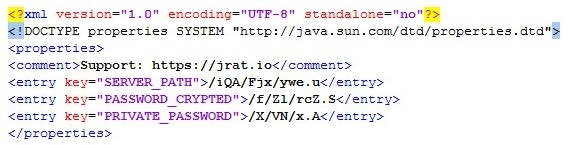
The configuration file points to yet more files specified by the SERVER_PATH, PASSWORD_CRYPTED, and PRIVATE_PASSWORD keys. These keys represents the following attributes:
- SERVER_PATH - Encrypted content
- PRIVATE_PASSWORD - RSA key repository
- PASSWORD_CRYPTED - AES key
We can use these additional files to isolate the core Adwind RAT tool and decompile it to check the core functionalities. Figure.6 is what we eventually find in the core of Adwind.
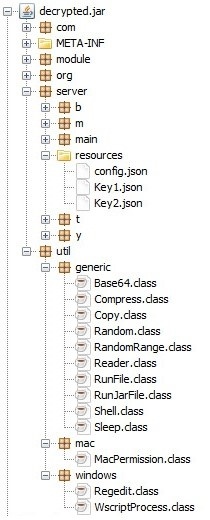
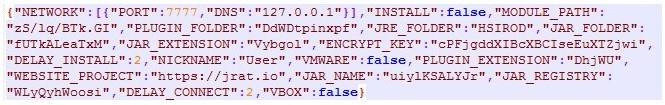
Looking even deeper into the JAR file, we can see operating system specific implementations (Adwind can work on macOS, Windows, and Linux), and utility classes containing code to execute other files, open shells, and carry out other activities. The resources directory of decrypted.jar contains a set of files that are used to decrypt the contents of config.json. This file contains configuration details (Figure.7) with information on network, path, user, and VMware, among other things.
Adwind does what Adwind does best
After all the layers of obfuscation are peeled back, what we are left with is Adwind. And Adwind is really a cross-platform malware that can monitor user activity, take screenshots, log keystrokes, record video and audio, and much more. This latest spam campaign spreading yet another variant of the RAT shows that the criminals behind it are constantly changing their tactics to evade detection. However, we are keeping a close eye on Adwind and are adjusting our protection when necessary to keep our customers safe.
A few simple steps to help you stay safe
In the meantime, follow these simple steps to help keep you safe from cyber attacks:
- Be wary of unsolicited emails, particularly those with a call to action to follow links and open attachments in the email. If in doubt, just delete the email.
- Use a comprehensive security solution such as Symantec Endpoint Protection or Norton Security to help keep you safe from cyber threats.
- Keep your software and operating system up to date with the latest updates to avoid falling victim to any exploit-based attacks.
Protection
Symantec has the following protection in place to protect against the malware mentioned in this blog:
Antivirus
Symantec.Cloud has advanced heuristics to detect the type of email used to spread Adwind.







We encourage you to share your thoughts on your favorite social platform.