Latest Intelligence for December 2017
We assess our year-end spam rate predictions, email bug could result in increased phishing attempts, and the number of Android apps used for cryptocurrency mining grows.
Some of the key takeaways from December’s Latest Intelligence, and the threat landscape in general, include year-end spam rates in line with our predictions, an email-spoofing bug, and an increase in Necurs activity.
Spam
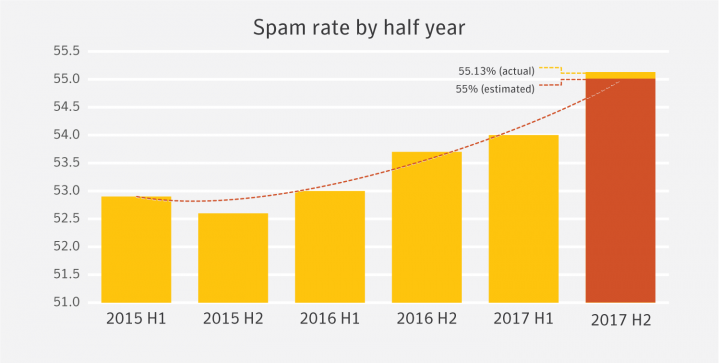
In December the global spam rate declined slightly to 55.3 percent, down 0.2 percentage points from 55.5 percent in November. In the Email Threats whitepaper, published earlier in the year, we took a look at spam rates in half-year increments. While doing so we made a prediction that the spam rate would continue to increase in the second half of 2017, estimating that it would come in at around 55 percent. Now that the year has closed out, we can see that this prediction turned out to be very close. At 55.13 percent, the actual global spam rate for 2017 H2 came in just a little higher than we anticipated.
The mining sector, which covers metal and coal mining, as well as oil and gas extraction, had the highest spam rate for December. Mining frequently appears at or near the top of the sector list for spam rates, having come out on top in 8 out of the last 12 months. For the year, the mining sector saw a spam rate of 58.8 percent.
Phishing
The phishing rate for December increased slightly to 1 in 2,109 emails. This marks two months of increases, after dropping to its lowest levels in six months last October. If current trends continue, we could soon see similar rates as those in June and July of last year, when phishing reached a 12-month high.
A recently uncovered email-crafting bug could allow attackers to easily spoof sender addresses and carry out code-injection attacks, possibly leading to an increase in phishing attempts. Dubbed “Mailsploit,” the newly discovered bug allows the encoding of non-ASCII characters inside of email headers, which are later decoded by the mail client as a spoofed email addresses. The method of execution varies depending on the client, but the security researcher who discovered it claims that the bug was found in over 30 applications. Whether this bug leads to an increase in the phishing rate remains to be seen.
Malware
The global email malware rate increased over December, bringing it up to 1 in 431 emails. While this is still below the rates seen from July through October, the overall month-on-month trend for the year has increased.
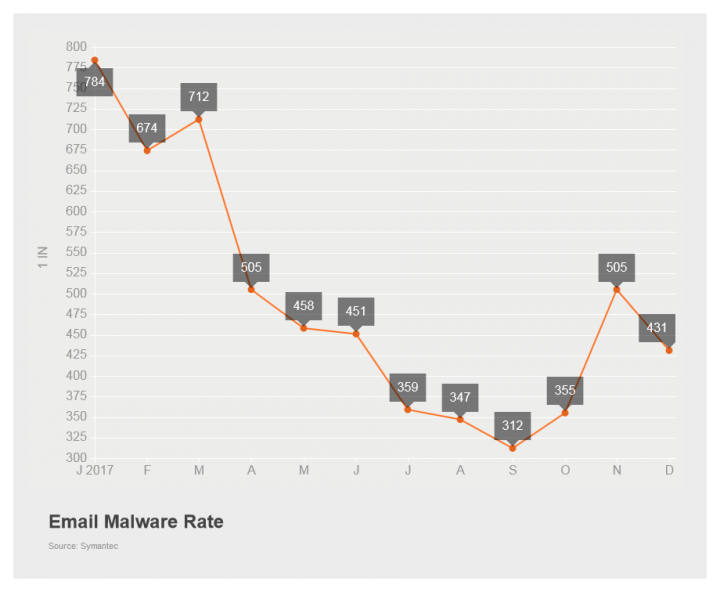
Much of this malware activity, or the lack thereof, can be attributed to the Necurs botnet. This botnet all but disappeared around Christmas 2016, only reemerging in late March 2017. As a consequence, the email malware rate tanked in January, dropping from a December 2016 rate of 1 in 123 emails all the way down to 1 in 784 emails in January. As the year progressed the rate crept back up, though never quite reaching the highs seen in 2016. However, as October arrived, and on into November, the rate began to decline again.
While it appeared as though we could have been in store for another December hiatus on the part of the actors behind Necurs, this turned out not to be the case. In fact, the holiday period in late December saw elevated activity, which likely led to the increase in the email malware rate. We'll find out in the coming months whether this represents the start of another active period, or simply a year-end push by the Necurs actors before going on another hiatus.
Mobile
There was one new Android malware family discovered in December. Android.Anubisspy is a Trojan that could be used to monitor a phone user's activity, such as taking screenshots, recording phone calls, and stealing content such as text messages, browser history, or the contents of databases present. The threat can also install apps and execute commands on rooted devices.
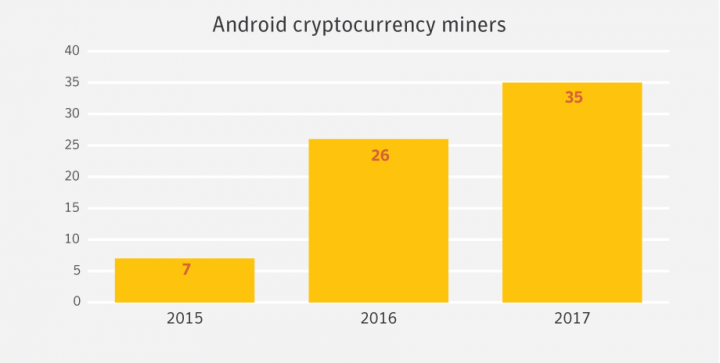
Mobile devices have increasingly become the target of cryptocurrency miners, according to new research conducted by Symantec. The ubiquity and always-connected nature of mobile devices has led to an increase in the frequency such devices are targeted for cryptocurrency mining. In fact, the number of Android apps used for mining has increased 34 percent in 2017.
This is just a snapshot of the news for the month. Check out the Latest Intelligence for the big picture of the threat landscape with more charts, tables, and analysis.







We encourage you to share your thoughts on your favorite social platform.