Tech Support Scam Integrates Call Optimization Service
Scammers are using service to dynamically insert phone numbers into scam pages.
Symantec has observed tech support scammers using a popular call optimization service, allowing them to dynamically insert phone numbers into their scam web pages and potentially giving them additional features to make their scams more successful.
Tech Support scammers continue to adapt their methods to ensure long-term success. We previously outlined how tech support scams have evolved by leveraging “living off the land” tactics to avoid detection. They have also used various other methods to evade detection, from simple JavaScript obfuscation to more advanced encryption algorithms such as the Advanced Encryption Standard (AES).
In this blog, however, we look at how scammers are now making use of legitimate call optimization services in order to make their scams more efficient.
Call optimization services
Call optimization services are commonly used by businesses whose customers interact with them over the phone. These services can provide the following features:
- Tracking the source of inbound calls
- Creation and management of phone numbers
- Call load balancing
- Call forwarding
- Call analytics
- Call routing
- Call recording
These services help businesses gain useful insights about their customers which can be used to help improve and optimize marketing campaigns. However, now it seems tech support scammers are also using call optimization services to optimize their own “campaigns,” as we recently discovered.
The scam
As with many tech support scams, it is initiated when an unsuspecting user visits a malicious website or is redirected to one by various means such as a malvertisement or compromised website.
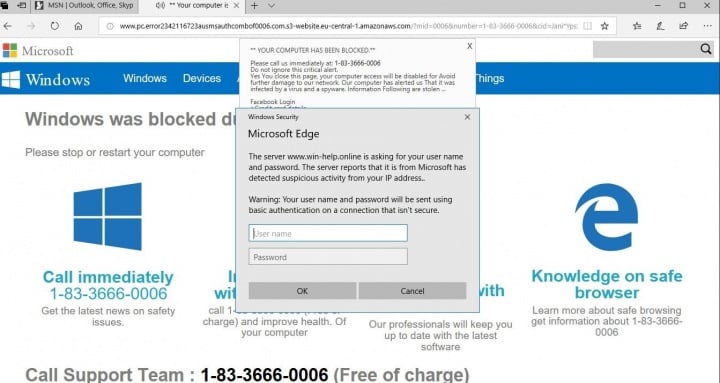
The scam web page informs the victim that the computer has been blocked due to a malware infection and tries to lure the user into calling a “toll free” number for assistance. An audio file, stating that the computer is infected, is also played in the background when the user arrives on the scam web page.
Joining the dots
A first look through the source code for the scam web page reveals the piece of code responsible for playing the audio.
After that, we come across some interesting pieces of JavaScript.
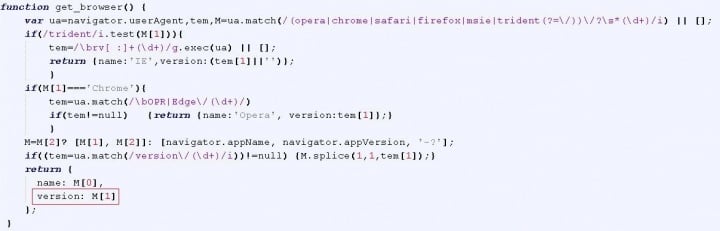
The script seen in Figure 2 retrieves information about the browser used by the victim. Tech support scams performing browser fingerprinting is nothing new but most scams only focus on the browser name. This particular scam goes a step further and retrieves the browser version as well. Based on the browser name and version number, the victim is redirected to a different scam page, as can be seen in the code shown in Figure 3.
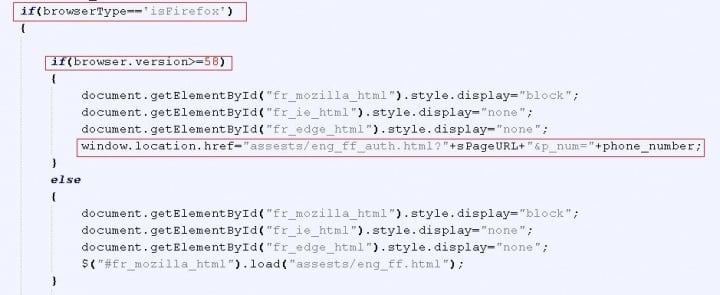
In Figure 4 we can see a script which is part of a popular call optimization service’s advanced JavaScript integration.
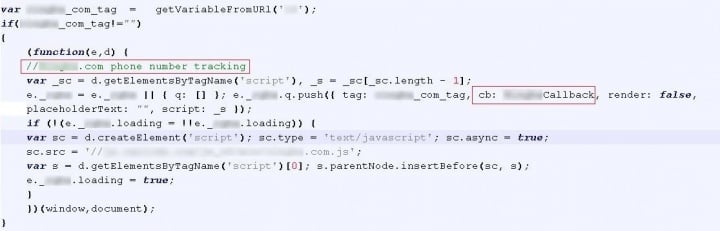
When a specific tag from the call optimization service is present in the scam URL, the script retrieves the scammer’s phone number from the service’s servers. When the servers return the scammer’s phone number, the tag triggers the “Callback” function. This function is responsible for retrieving and displaying the appropriate phone number for victims to call.
If the tag from the call optimization service in not in the scam URL, the phone number is retrieved by loading an XML file and then parsing it to retrieve the number, which is then displayed on the scam page (see Figure 5).
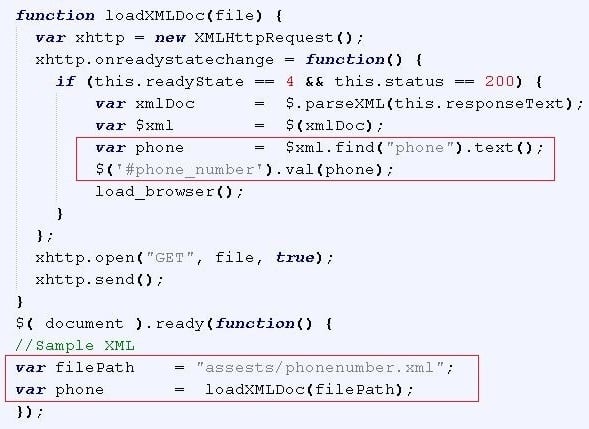
However, by using the call optimization service’s tag in the URL the scammers can dynamically insert phone numbers into their scam pages. This can be useful, for example, if victims are based in multiple countries, as the victim can be shown a phone number that calls someone that speaks their language.
Other possible uses
Using call optimization services to make sure the correct phone number is displayed to each victim is just one feature we know of that tech support scammers are using. It’s possible that scammers are also taking advantage of many more of the features offered by these useful services, such as call load balancing during busy times, rerouting calls to other “tech support” agents so no customers/victims are lost; tracking the source of inbound calls, allowing the scammers to tailor their service; accessing detailed analytics about calls, which could help scammers understand what they need to do to improve their success rate. These are just a few of the many features scammers could incorporate.
Call centers, ecommerce vendors, affiliate networks, and all manner or small to large organizations have recognized the advantages of using call optimization services to improve their business, and now the criminals behind tech support scams have begun doing the same.
Prevalence and protection
Symantec proactively protects customers against tech support scams. Our intrusion prevention system (IPS) protects customers from tech support scams by blocking the malicious network activity associated with such scams using a wide variety of detections.
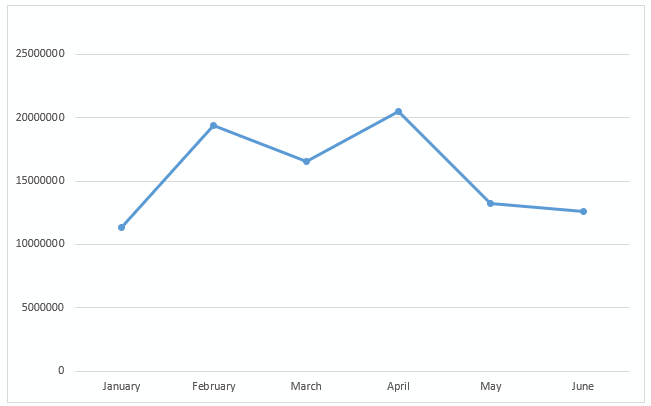
From January 1, 2018 through June, Symantec’s IPS blocked more than 93 million tech support scams.
Mitigation
- Norton Security, Symantec Endpoint Protection, and many other Symantec security products have comprehensive network-based protection features such as firewall and IPS built in. To protect yourself from these types of scams, ensure that these features are enabled.
- Also, make sure to only visit legitimate websites when you need support for any product.
- Last but not least, make sure your security product is updated regularly.
- More information on tech support scams can be found here.







We encourage you to share your thoughts on your favorite social platform.