Welcome to the Part 1 out of 3 discussing the terms, technologies and concepts related to Symantec Endpoint Protection and Symantec Security Software. In the series you will find description and explanation of several SEP related technologies, tools and concepts alongside of the relevant links to Symantec KB articles. The terminology articles are based upon the available official documentations and publications from Symantec KBs and Implementation Guides for SEP. Any comments or ideas what should be included in the series are welcome. I hope this series will be informative to you.
The Series consists of following articles:
Symantec Endpoint Protection Terminology Guide - Concepts, Technologies, Terms - Part 1 (A-G)
Symantec Endpoint Protection Terminology Guide - Concepts, Technologies, Terms - Part 2 (H-R)
Symantec Endpoint Protection Terminology Guide - Concepts, Technologies, Terms - Part 3 (S-Z)
This is the fist part of the series concerning the following terms:
Administrator-defined Scans - type of antivirus/antimalware scans set up on the SEPM manager and provided to SEP client over the assigned policy. Administator-defined scans can be either scheduled scans or on-demand scans. Administrators define scheduled scans to run on client computers at configurable intervals. Administrators can predefine a specific set of scan settings for running on-demand scans on clients from the management console. On-demand scans are manual scans run on a client at the administrator's request.
Scheduling an administrator-defined scan
http://www.symantec.com/docs/HOWTO16379
Customizing administrator-defined scans for clients that run on Windows computers
http://www.symantec.com/docs/HOWTO54927
Anti-MAC Spoofing - a setting in Virus and Malware Protection of Symantec Endpoint Protection. When enabled, Symantec Endpoint Protection allows incoming and outgoing address resolution protocol (ARP) traffic if an ARP request was made to that specific host. All other unexpected ARP traffic is blocked and an entry is generated to the Security log.
Detecting potential attacks and spoofing attempts
http://www.symantec.com/docs/HOWTO55408
Antivirus and Antispyware Protection - protects computers from viruses and security risks, and in many cases can repair their side effects. The protection includes real-time scanning of files and email as well as scheduled scans and on-demand scans. Virus and spyware scans detect viruses and the security risks that can put a computer, as well as a network, at risk. Security risks include spyware, adware, and other malicious files. Antivirus and Antispyware Protection can reduce the amount of false positives and improve scan perfromance when used together with several other SEP technologies like: SONAR, File System Auto-Protect, Insight Lookup, Download Insight.

Symantec Endpoint Protection Manager - Antivirus and Antispyware - Policies explained
http://www.symantec.com/docs/TECH104430
Application and Device Control (ADC) - is an advanced security feature included in Symantec Endpoint Protection and offers two types of control, or protection, over client computers: application control and device control. Application Control provides administrators with the ability to monitor and/or control the behavior of applications - some of the possible scenarios:
■ Prevent malware from taking over applications
■ Restrict the applications that can run
■ Prevent users from changing configuration files
■ Protect specific registry keys
■ Protect particular folders, such as \WINDOWS\system
Device control manages the hardware devices that access client computers. It can be used in following ways:
■ Block or allow different types of devices that attach to client computers, such as USB, infrared, and FireWire devices
■ Block or allow serial ports and parallel ports
Another part of Application and Device Control is System Lockdown - a feature used to ensure that the system stays in a known and trusted state. Some of the ADC policies were designed to protect against the activities associated with certain particular threats and are recommended for use in outbreak situations.
Best Practices for Deploying Symantec Endpoint Protection's Application and Device Control Policies
http://www.symantec.com/docs/TECH145973
Symantec Endpoint Protection Manager - Application and Device Control (ADC) - Policies explained
http://www.symantec.com/docs/TECH104431
How to configure Application Control in Symantec Endpoint Protection 11.0 : Configuring Application Control Policies
http://www.symantec.com/docs/TECH102525
How to use Application and Device Control to limit the spread of a threat.
http://www.symantec.com/docs/TECH93451
How to use Symantec Endpoint Protection to block or log legitimate but unauthorized software usage
http://www.symantec.com/docs/TECH97618
Application learning - allows Symantec Endpoint Protection (SEP) clients to report information and statistics about the executables that are run on them. The information is provided to the SEPM and collected in the SEPM database. The purpose of this information is to build a list of known applications in an environment to create Application-based firewall rules, Host Integrity (HI) rules and can be used as a reference for Centralized Application Exceptions.
How to set up learned applications in the Symantec Endpoint Protection Manager
http://www.symantec.com/docs/TECH102994
Best Practices Guide to Application Learning in Symantec Endpoint Protection Manager
http://www.symantec.com/docs/TECH134367
BASH (Behavioural Analysis and System Heuristics)- is an underlying technology for a number of SEP 12.1 features, and is not limited to Proactive Threat Protection or SONAR. The SEP components heavily based on the BASH technology are Tamper Protection, Suspicious Behaviour Detection/System Change Detection, SONAR, Reputation Submissions.
Bloodhound - is a component of a heuristic protection. Bloodhound isolates and locates the logical regions of a file to detect a high percentage of unknown viruses. Bloodhound then analyzes the program logic for virus-like behavior.
What is the difference between the Bloodhound and Proactive Threat Protection (TruScan) technologies?
http://www.symantec.com/docs/TECH92436
How to enable, disable, or configure Bloodhound(TM) heuristic virus detection in Symantec Endpoint Protection.
http://www.symantec.com/docs/TECH92424
Browser Intrusion Prevention - is a new advanced protection feature included with the SEP 12.1 client. This technology works in conjunction with, but is separate from the Client Intrusion Detection System (CIDS) used by the client firewall-based IPS engine in SEP. BIPS uses IPS signatures to detect the attacks that are directed at browser vulnerabilities. Browser intrusion prevention monitors attacks on Internet Explorer and Firefox. Browser intrusion prevention is not supported on any other browsers. This type of intrusion prevention uses attack signatures as well as heuristics to identify attacks on browsers.
Expected behavior of Browser Intrusion Prevention
http://www.symantec.com/docs/TECH172174
How intrusion prevention works
http://www.symantec.com/docs/HOWTO81344
Supported Browser versions for Browser Intrusion Prevention
http://www.symantec.com/docs/TECH174537
Central Quarantine – is a central static repository of detected threats where SEP clients can forward the infected items from their own local Quarantine. The Central Quarantine consists of two components: the Quarantine Server and the Microsoft Management Console (MMC) snap-in. It provides a single source to co-locate all quarantined items on the network. Quarantined items can be all viewed from the Console and they are automatically submitted to Symantec Security Response. The Central Quarantine stays completely optional as in normal circumstances SEP and SEPM by itself can handle quarantined items on their own. Central Quarantine Server and Client Console require separate installations - the installers can be found on the Part2_Tools.exe image attached to the SEP installation media.
Symantec™ Central Quarantine Implementation Guide
http://www.symantec.com/docs/DOC3258
Installing and configuring the Central Quarantine
http://www.symantec.com/docs/TECH105496
Setting up Symantec Endpoint Protection clients to forward infected files to a Central Quarantine Server.
http://www.symantec.com/docs/TECH104755
Installing the Quarantine Server
http://www.symantec.com/docs/HOWTO26760
Centralized Exceptions - are part of the Centralized exception policy and allow for exclusion of certain items from future detection from different SEP Scan components like AV, Truscan, Sonar or even Tamper Protection. It is possible to exclude items like: Known security risks, Extensions, Files, Folders.

Symantec Endpoint Protection Manager - Centralized Exceptions - Policies explained
http://www.symantec.com/docs/TECH104432
Creating Centralized Exceptions Policies in the Symantec Endpoint Protection Manager 11
http://www.symantec.com/docs/TECH104326
Checksum Utility - utility used to create a file fingerprint list. The list contains the path and the file name and corresponding checksum for each executable file or DLL that resides in a specified path on the computer. The utility is installed with Symantec Endpoint Protection on the client computer and offers an alternative to some other available third-party tools.
Creating a file fingerprint list with checksum.exe
http://www.symantec.com/docs/HOWTO81199
Cleanwipe - a tool used to prepare or clean any supported Windows computer before Symantec Endpoint Protection installation. CleanWipe should be used as a last resort after all other means to prepare or clean a computer for Symantec Endpoint Protection installation have failed. May be used as well to clean and remove corrupted SEP installations. Software currently supported by Cleanwipe Tool: SEP/SEPM, SNAC, SAV, Symantec Client Security, SPC, Windows Liveupdate. Tool maybe obtained only directly from Symantec Support.

New Cleanwipe version is introduced for SEP 12.1 RU2
https://www-secure.symantec.com/connect/articles/new-cleanwipe-version-introuduced-sep-121-ru2
Client / Computer Mode - two different modes defining how the policies should be applied to the clients in groups. If the client software runs in user mode, the client computer gets the policies from the group of which the user is a member. If the client software runs in computer mode, the client computer gets the policies from the group of which the computer is a member.
About user mode and computer mode
http://www.symantec.com/docs/HOWTO27008
Client Deployment Wizard - GUI based SEPM wizard that helps quickly locate unprotected computers on which youneed to install the client software. The wizard also provides an email deployment link so that users can download the client software by using the Web. Other option of deployment consist of Push deployment of the installation package over the network or export of the installation package as .exe or .msi executable.
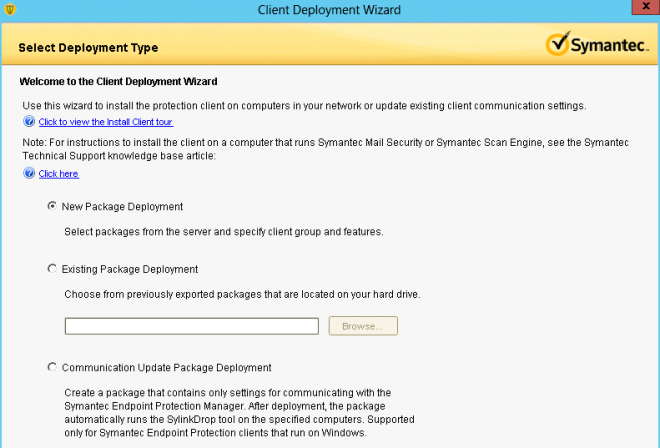
How to install clients using "Client Deployment Wizard" in the Symantec Endpoint Protection Manager 12.1
http://www.symantec.com/docs/TECH164308
Communication Update Package Deployment - a new feature implemented in SEPM 12.1 RU2 that allows for remote deployment of communication settings (sylink.xml) to the SEP Clients directly from SEPM. It is an automated machanism replacing the older methods of sylink replacement such as Sylinkdrop or Sylink Replacer tools. This feature may be used for a large number of computers, for the computers that cannot be physically accessed easily, or the computers that require administrative access.
Restoring client-server communications with Communication Update Package Deployment
http://www.symantec.com/docs/HOWTO81109
SEP 12.1 RU2 and Reset Client Communication
https://www-secure.symantec.com/connect/articles/sep-121-ru2-and-reset-client-communication
Content Distribution Monitor - utillity used to monitor the health and status as well as general content deployment of Group Update Providers in the environment. This is a lightweight, stand-alone tool designed to be run directly on the Symantec Endpoint Protection Manager (SEPM) server, and should return a graphical display of the content distribution status.
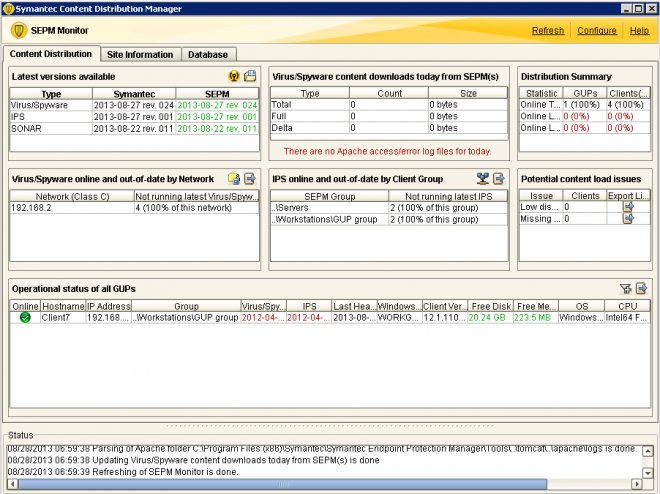
SEP Content Distribution Monitor / GUP monitoring tool.
http://www.symantec.com/docs/TECH156558
SEP Content Distribution Monitor (for GUP health-checking)
https://www-secure.symantec.com/connect/downloads/sep-content-distribution-monitor
SEP Content Distribution Monitor - Introduction
https://www-secure.symantec.com/connect/videos/sep-content-distribution-monitor-introduction
Dbvalidator - a tool used to find a broken database object and broken links in the database.
How to use the Database Validation tool (DBValidator.bat) for Symantec Endpoint Protection Manager
http://www.symantec.com/docs/HOWTO39461
How to use the Validation Tool for the Symantec Endpoint Protection Manager Database.
http://www.symantec.com/docs/TECH104892
DevViewer - tool used to view the devices on a client computer and obtain the class IDs or device IDs of them. This ID is needed when creating or editing Application and Device Control Policies. DevViewer can be found on CD2 of the SEP Installation media under ...Tools\NoSupport\DevViewer.

DevViewer - a tool for finding hardware device ID for Device Blocking in Symantec Endpoint Protection
http://www.symantec.com/docs/TECH103401
Disaster Recovery - set of procedure steps used when in case of hardware failure or database corruption. Depending on the SEPM version and the database type used the steps may differ. Mostly the steps will include the backup of the database and configuration files. Later stage includes restore process of SEPM, the database, server ceritificates and client communication.
Symantec Endpoint Protection 12.1: Best Practices for Disaster Recovery with the Symantec Endpoint Protection Manager
http://www.symantec.com/docs/TECH160736
Symantec Endpoint Protection 11.x: Best Practices for Disaster Recovery with the Symantec Endpoint Protection Manager
http://www.symantec.com/docs/TECH102333
Doscan - a tool that enables to run a quick or a scheduled SEP client scans from command prompt, batch scripts or the windows task scheduler. DoScan is not a separate scanner – it does use the same scan engine build-in in SEP – for it to run Autoprotect on the SEP client needs to be enabled. DoScan.exe is located directly in the SEP installation folder and does not require a separate download.

DoScan.exe – SEP Antivirus scans from Command Prompt – Introduction
https://www-secure.symantec.com/connect/articles/doscanexe-sep-antivirus-scans-command-prompt-introduction
How to run a scan from a command line using Symantec Endpoint Protection using DoScan.exe
http://www.symantec.com/docs/TECH104287
Download Insight - is a new advanced protection feature included with the SEP 12.1 clients. DI is a part of Auto-Protect protection. This feature allows the SEP client to leverage Symantec's Cloud-based reputation database when files are downloaded or executed directly from popular Web browsers, text messaging clients, and other portals. Supported portals include Internet Explorer, Firefox, Microsoft Outlook, Outlook Express, Windows Live Messenger, and Yahoo Messenger. Download Insight determines that a downloaded file might be a risk based on evidence about the file's reputation. Download Insight is supported only for the clients that run on Windows computers.

Expected behavior of Download Insight
http://www.symantec.com/docs/TECH171776
Managing Download Insight detections
http://www.symantec.com/docs/HOWTO55252
Customizing Download Insight settings
http://www.symantec.com/docs/HOWTO55253
Early Launch Anti-Malware Driver - works with the Microsoft ELAM driver to provide protection for the computers in the network when they start up and before third-party drivers initialize. The settings are supported on Microsoft Windows 8. Malicious software can load as a driver or rootkits might attack before the operating system completely loads and Symantec Endpoint Protection starts. Rootkits can sometimes hide themselves from virus and spyware scans. Early launch anti-malware detects these rootkits and bad drivers at startup.
Managing early launch anti-malware (ELAM) detections
http://www.symantec.com/docs/HOWTO81107
Adjusting the Symantec Endpoint Protection early launch anti-malware (ELAM) options
http://www.symantec.com/docs/HOWTO81106
Embedded Database - the database stores security policies and events. The database is installed on the computer that hosts Symantec Endpoint Protection Manager. Embedded database is a Sybase SQL DB and is an alternative to use a of remote MS SQL DB - that is also supported with SEPM. The embedded database does not require configuration and is the easiest to install. The embedded database supports up to 5,000 clients.
Maintaining the database
http://www.symantec.com/docs/HOWTO55337
Symantec Endpoint Protection Manager 12.1.2 Database Schema
http://www.symantec.com/docs/DOC6039
Encryption password - The password that encrypts communication between the Symantec Endpoint Protection Manager, clients, and optional Enforcer hardware devices. The password can be from 1-32 alphanumeric characters and is required. Encryption password cannot be changed or recovered after creation of the database. It is required for disaster recovery purposes. During the default SEPM installation, the entered administrator password will be the same as the encryption password. If you change the administrator's password, the encryption password does not change.
The Encryption Password and Symantec Endpoint Protection 11 (SEP11)
http://www.symantec.com/docs/TECH93119
Enforcer - a software component that enforces policy compliance in three ways: Gateway Enforcer, DHCP Enforcer, or LAN Enforcer. Enforcers authenticate clients to ensure they are running the Symantec Agent and comply with Host Integrity rules. A Gateway Enforcer is used for enforcement at access points for external computers connecting remotely through a VPN, Wireless LAN, or Remote Access Server (RAS). A LAN Enforcer is used for enforcement for internal clients that connect to the LAN through a switch that supports 802.1x authentication. A DHCP Enforcer is used for enforcement of internal clients that gain access to the LAN by receiving a dynamic IP address through a Dynamic Host Configuration Protocol (DHCP) server.
Symantec Network Access Control 11.0 LAN Enforcement Overview
http://www.symantec.com/docs/TECH102536
Symantec Network Access Control 11.0 Gateway Enforcement Overview
http://www.symantec.com/docs/TECH102537
Configuring a connection between an Enforcer appliance and a Symantec Endpoint Protection Manager
http://www.symantec.com/docs/HOWTO81652
Explicit Group Update Provider - a type of Group Update Provider (GUP) include since SEP 12.1 RU2 version. It allows configuration of an explicit list of Group Update Providers that clients can use to connect to Group Update Providers that are on subnets other than the client's subnet. Especially recommended for roaming clients.
About the types of Group Update Providers
http://www.symantec.com/docs/HOWTO80957
Understanding "Explicit Group Update Providers (GUPs) for Roaming Clients" in Symantec Endpoint Protection (SEP) 12.1.2
http://www.symantec.com/docs/TECH198640
SEP 12.1 RU2 And Explicit Group Update Providers
https://www-secure.symantec.com/connect/articles/sep-121ru2-and-explicit-group-update-provider
What is the processing order of an Explicit GUP list within version 12.1.2 of Symantec Endpoint Protection?
http://www.symantec.com/docs/TECH196741
Fast Pathing - feature implemented in SEP 12.1 RU4 - allows an organization to set a relatively long heartbeat interval to minimize traffic without losing up to date information about the security of clients. With "Fast Pathing" enabled, the client checks if there are new detections or new network security events every minute. If one of these critical events is found, the SEP client uploads all threat-detection and network security related information for those events to SEPM overriding thus the normal heartbeat settings. The setting for Fast Pathing is located in the group's "Communications Settings" ->
"Let clients upload critical events immediately"
Information about the "Fast Pathing" feature in SEP 12.1 RU4
File Fingerprint List - consists of a list of checksums, one for each application on a client computer. It includes the complete file paths of those applications. You can create a file fingerprint list from a software image that includes all the applications that you want to allow users to run. You can manage file fingerprint lists in Symantec Endpoint Protection Manager and use them in your system lockdown configuration. To create a file fingerprint list, you can use the Checksum.exe utility. The utility is installed along with Symantec Endpoint Protection on the client computer.
Creating a file fingerprint list with checksum.exe
http://www.symantec.com/docs/HOWTO81199
Managing file fingerprint lists
http://www.symantec.com/docs/HOWTO55133
File System Auto-Protect - File System Auto-Protect is a type of ongoing or background scan that provides real-time protection for files on your computer. Whenever files are being accessed, copied, saved, moved, opened, or closed, Auto-Protect scans them to ensure that a threat or security risk is not present. According to the settings in the policy Auto-Protect offers several options for mitigating the detected threats such as: Clean risk, Quaranatine risk, Delete risk, or Leave alone.
What is Auto-Protect ?
http://www.symantec.com/docs/TECH94990
Firewall - a feature is part of Network Threat Protection in SEP. Firewall allows or blocks network traffic based on the various criteria that the administrator sets. If the administrator permits it, end users can also configure firewall policies. Firewall is responsible for executing following tasks:
■ Prevents any unauthorized users from accessing the computers and networks in your organization that connect to the Internet
■ Monitors the communication between your computers and other computers on the Internet
■ Creates a shield that allows or blocks attempts to access the information on your computers
■ Warns you of connection attempts from other computers
■ Warns you of connection attempts by the applications on your computer that connect to other computers
The Symantec Endpoint Protection firewall uses firewall policies and rules to allow or block network traffic. The Symantec Endpoint Protection includes a default Firewall policy with default firewall rules and firewall settings for the office environment. Firewall rules control how the client protects the client computer from malicious
inbound traffic and malicious outbound traffic. The firewall automatically checks all the inbound and the outbound packets against these rules. The firewall then allows or blocks the packets based on the information that is specified in rules.
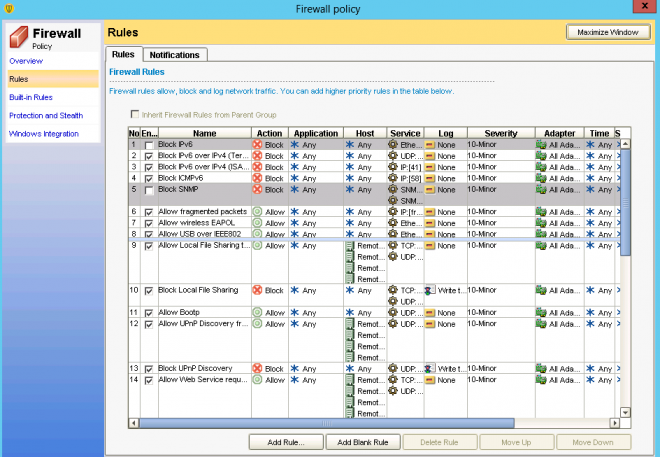
About the Symantec Endpoint Protection firewall
http://www.symantec.com/docs/HOWTO55247
Symantec Endpoint Protection Manager - Firewall - Policies explained
http://www.symantec.com/docs/TECH104433
Managing firewall protection
http://www.symantec.com/docs/HOWTO55053
How a firewall works
http://www.symantec.com/docs/HOWTO55054
How the firewall uses stateful inspection
http://www.symantec.com/docs/HOWTO55098
About firewall rules
http://www.symantec.com/docs/HOWTO55261
About inherited firewall rules
http://www.symantec.com/docs/HOWTO55483
Group Update Provider (GUP) - a client computer designated to locally distribute content updates to clients - usually within a specified subnet only - although it can provide updates as well across subnets when correctly configured. A Group Update Provider downloads content updates from the SEPM Server only and distributes them to clients. A Group Update Provider helps conserving bandwidth by localizing content distribution - there are as well available settings for throttling the available bandwith for content download from SEPM to a GUP. GUP can only distribute content updates - definitions and does not support distribution of Product updates such as new version of the SEP installer. According to settings the is possibility to specifify either a single GUP or multiple GUPs for a specific group of clients. Newer SEP versions offer as well a new implementation of GUP - Explicit Group Update Provider.

Best Practices and Troubleshooting for Group Update Providers
https://www-secure.symantec.com/connect/blogs/best-practices-and-troubleshooting-group-update-providers
Group Update Provider: Sizing and Scaling Guidelines
http://www.symantec.com/docs/TECH95353
Best Practices with Symantec Endpoint Protection (SEP) Group Update Providers (GUP)
http://www.symantec.com/docs/TECH93813
Configuring the Group Update Provider (GUP) in Symantec Endpoint Protection 11.0 RU5 and later
http://www.symantec.com/docs/TECH96419
About the types of Group Update Providers
http://www.symantec.com/docs/HOWTO80957