Some of the key takeaways from May’s Latest Intelligence, and the threat landscape in general, include another increase in the number of web attacks blocked, a peculiar Google phishing scam, and of course, the WannaCry ransomware outbreak.
Web attacks
Last month the number of web attacks blocked increased 22 percent, from 1,038,000 per day to 1,266,000 per day in May. This is the highest amount of web attacks seen since November 2015.
In terms of exploit kit activity, the RIG toolkit comprised 28.4 percent of exploit kit activity, though this was down 1.1 percentage points from April. Halfway through the month, a number of legit, but apparently compromised websites known to redirect to the RIG exploit kit were apparently switching to the Terror exploit kit. In seeming contrast to this shift, the RoughTed malvertising operation appears to now be using the RIG exploit kit, in addition to the Magnitude exploit kit to spread its payloads. Magnitude is up for May, rising from 6.3 to 7 percent of exploit kit activity.
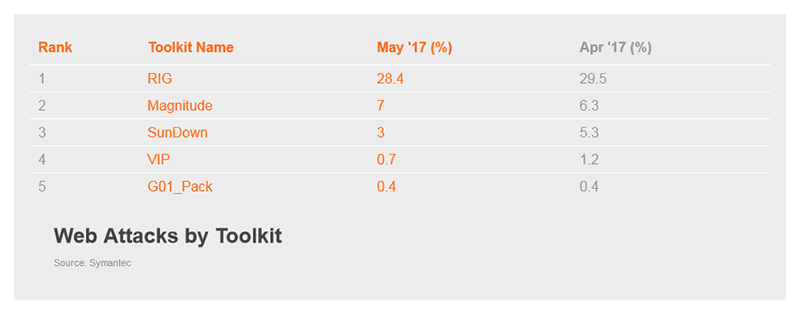
Figure 1. RIG held the top spot for exploit kit activity in May
Malware
There were 76.7 million new malware variants discovered in May. This is down slightly from April, but as a whole contributes to four months of elevated activity in this area of the threat landscape, following a lull during the December-to-January period.
The email malware rate increased in May, where one in every 422 emails contained a malicious payload. This marks the second month in a row with an increase in this malware rate, though it is still well below overall levels seen throughout 2016. The Necurs botnet is responsible for a good portion of this malicious activity, having returned in late March after a nearly three month absence. In particular, researchers noted a Necurs-led campaign distributing a new ransomware threat, dubbed Jaff, where email distribution traffic peaked at nearly 5 million emails an hour.
Speaking of ransomware, WannaCry made its presence known on the threat landscape beginning May 12, quickly becoming one of the worst malware outbreaks in recent memory. Symantec quickly published a blog covering everything known about WannaCry, updating it with new information as the threat spread.
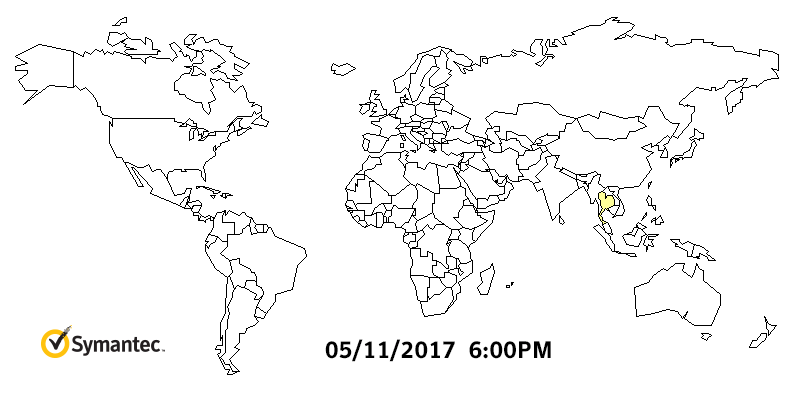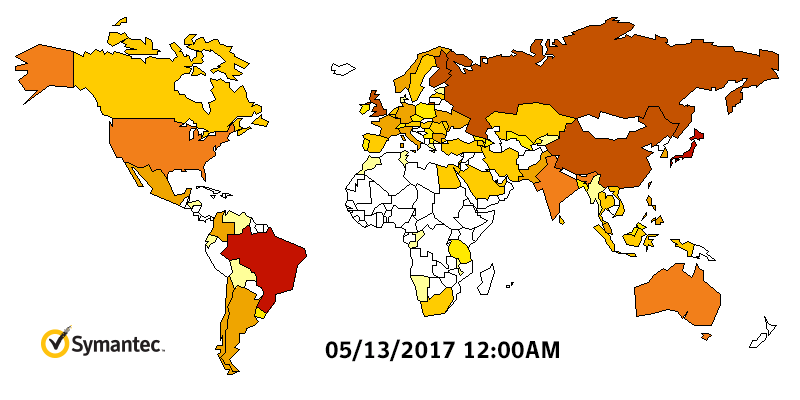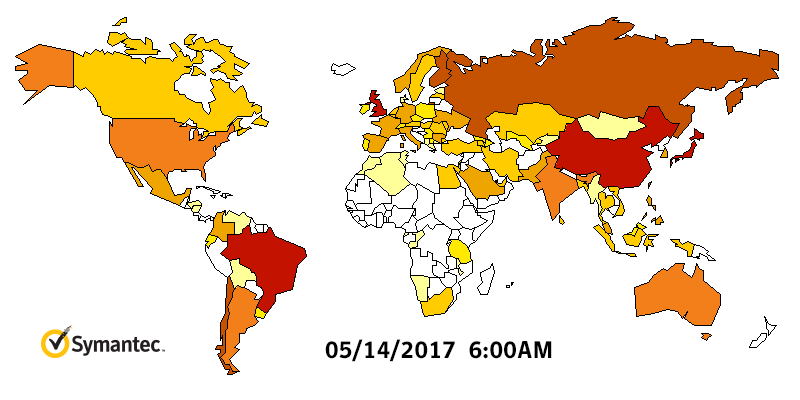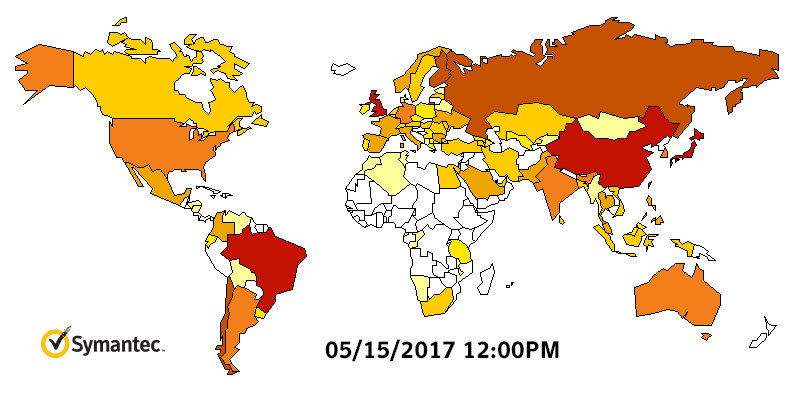
Figure 2. Heatmap showing Symantec detections for WannaCry, May 11 to May 15
Finally, Symantec researches published information about a highly skilled cyber criminal. This particular attacker has been observed developing and deploying malware so advanced that our researchers originally thought it could be the work of a nation state. However, the attacker appears to be using it for far less ambitious ends. Further information on the attacks can be found on the Security Response blog and the Threat Intel Medium publication.
Spam
There were slight declines in the spam rate overall, down 0.1 percentage points in May to 54.1 percent. The Construction and Mining sectors were of note for having above average spam rates, at 59.9 percent and 57.9 percent, respectively.
There was an incident that came to light during May where users of an online dating site began receiving highly tailored spam. Some recipients realized that some of the personal information in the spam could only have come from online profiles they had created with the Guardian Soulmates dating service. The company behind the site eventually admitted that the attackers had managed to obtain user email addresses and user IDs by utilizing a flaw in a third-party tool used by the site. The attackers then managed to gather other personal details by using the information obtained to locate the users' public-facing profile pages, and then sending them spam.
[click_to_tweet:1]
Phishing
The phishing rate has reached a high for 2017, finally returning to rates similar to those seen during 2016. After three months of relatively low phishing rates, this is the highest seen since November 2016. The Services and Public Administration sectors saw the highest rates for the month.
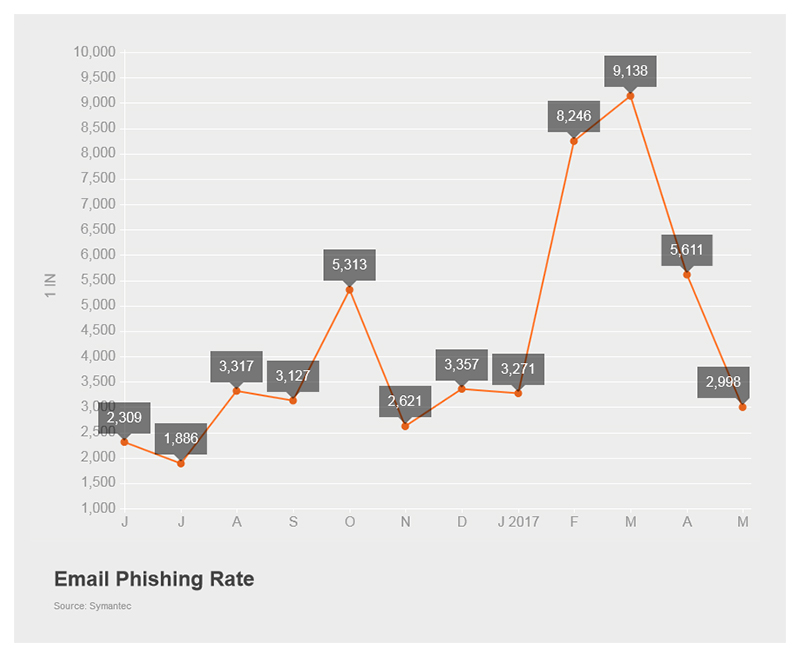
Figure 3. The phishing rate for May was the highest seen since November 2016
In a rather peculiar incident in May, a phishing scam was discovered that can provide an attacker access to a user’s Gmail account and Google Contacts. The attack works by providing a legitimate Google sign-in screen, leading to a “continue to Google Docs” link. However, this link points to a non-Google associated, third-party app simply named “Google Docs.” While a clever attack on the surface, what followed was even more bizarre. The following day a Twitter account named @EugenePupov appeared, claiming that this wasn’t a phishing scam but simply a Coventry University project gone awry. However, Coventry University stated that no one by that name was enrolled at, or had ever attended, their institution. All told, Google stated that 0.1 percent of their users were impacted by this scam; some estimates put this at close to 1 million accounts.
In other phishing news, a highly tailored attack aimed at two music management businesses resulted in the theft of unreleased songs by Lady Gaga. In what appears to be a social engineering scam, attackers impersonated an executive from Interscope Records, convincing two executives at the management companies to send copies of the songs used for postproduction and mixing to them. While the songs have yet to be leaked publicly, the incident highlights how a weak link in a supply chain can lead to a breach.
Mobile and social media
No new Android malware was seen and the variants per family rate stayed at 62.
Two mobile-related banking heist stories made the news in May. First, attackers exploited weaknesses in the SS7 protocol used by mobile operators for interoperability between networks. By doing so the attackers were able to bypass two-factor authentication and steal money from German bank accounts. The potential for SS7 abuse has long been known to mobile operators, and this is not the first time it has been used in an attack.
In more positive news, 16 suspected cyber criminals were arrested for alleged involvement in a banking malware campaign. The group is accused of targeting customers of a number of Russian banks and making off with $883,000 as a result. The arrests appear to have disrupted expansion plans by the group, which reportedly planned to target further banks in the UK, France, Germany, the U.S., and other countries.
This is just a snapshot of the news for the month. Check out the Latest Intelligence for the big picture of the threat landscape with more charts, tables, and analysis.