There has been a sudden drop off in activity relating to a number of major malware families in recent weeks. Dridex (W32.Cridex), Locky (Trojan.Cryptolocker.AF), the Angler exploit kit and Necurs (Backdoor.Necurs), are among the threats who appear affected by this development. Following reports of scaling back in activity by a range of cybercrime gangs, Symantec telemetry has confirmed that some of these groups have virtually ceased operating, while others appear to have greatly scaled back activity.
Locky has been one of the most prevalent ransomware threats in recent months, but Symantec has seen very few new Locky cases, either from spam campaigns or exploit kits since the beginning of June. While the threat has not disappeared, there has been a significant dip in activity, indicating that that there has been some disruption in the actors’ operations or a conscious decision to scale back.
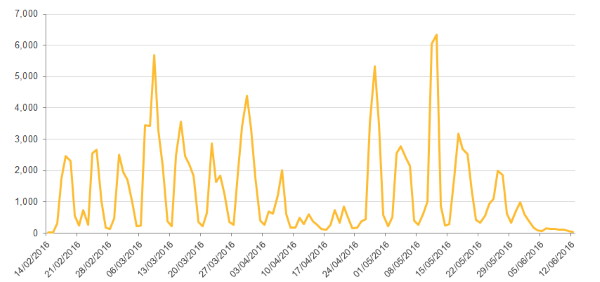
Figure 1. Blocked Locky infections by week, showing drop in activity over past two weeks
Financial fraud Trojan Dridex, which is known to use the same spam affiliate has Locky, has also shown a notable drop in activity but has not disappeared entirely. The Dridex botnet is segregated into a number of subsidiary botnets, known as subnets. These subnets are identified by three digit numbers, e.g. 120, 220 etc. Some subnets, such as 120, are continuing to operate. In addition to this, Symantec has observed a number of Word macro downloaders (W97M.Downloader) continuing to deliver Dridex through spam campaigns.
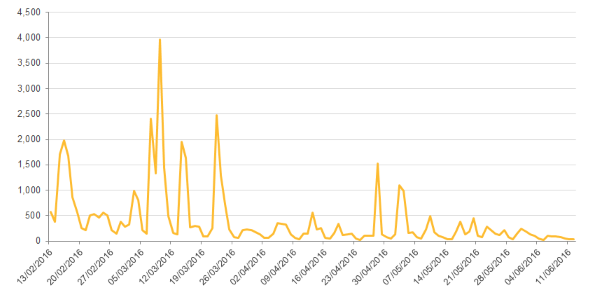
Figure 2. Blocked Dridex infections by week, showing low activity in recent weeks
The Necurs botnet has also been reported to have suffered an outage in recent days although it has since resumed activity. Necurs has been heavily associated with major spam campaigns and disruption in its activities could provide one possible explanation for the drop on Locky and Dridex activity.
Another threat group to drop off the radar is the Angler exploit kit. Symantec telemetry has not reported any payloads being delivered by Angler since the beginning of June nor has it reported any compromised websites that points to the exploit kit. This is not the first time Symantec has seen Angler become inactive and it remains uncertain whether the well-known exploit kit has disappeared permanently.
Angler’s disappearance has also prompted a falloff in activity in CryptXXX ransomware (Trojan.Cryptolocker.AN). Angler was one of the main delivery channels for CryptXXX.
Angler is not the only exploit kit to recently depart the scene. The well-known Nuclear exploit kit became inactive from the beginning of May. Since this occurred one month earlier, it is unclear if there is any connection with more recent developments.

Figure 3. Payloads being delivered by Nuclear exploit kit. Activity ceases in first week in May.
Connection with arrests
Mystery surrounds the sudden drop off in activity among so many threat groups, but it comes in the immediate aftermath of the arrest of 50 people in Russia accused of involvement in the Lurk banking fraud group.
Given that most of the affected threats have not disappeared entirely, it appears unlikely that they are directly connected to the Lurk group. One possible explanation is that the law enforcement takedown against Lurk could have resulted in the shutdown or seizure of infrastructure used by other attacker groups, who have since been working to resume their operations.
Symantec Security Response is continuing to monitor the situation and will provide further updates if new information comes to light.