
Symantec Security Response recently discovered a peculiar back door program that targeted a Korean organization. The malware, detected by Symantec as Backdoor.Baccamun, is dropped by an RTF document written in Korean that is disguised as an internal invitation to the organization’s employees for a free car inspection. The document file exploits the Microsoft Windows Common Controls ActiveX Control Remote Code Execution Vulnerability (CVE-2012-0158) and drops the Backdoor.Baccamun upon successful exploit of the vulnerability.
The back door is quite compact (19 kilobytes) and is smaller than average back door programs. It can perform the following actions:
- List running processes
- Terminate processes
- Download files
- Execute arbitrary commands
While the malware does not have any out of the ordinary functions, it does have an interesting marker that the attacker left in the code.
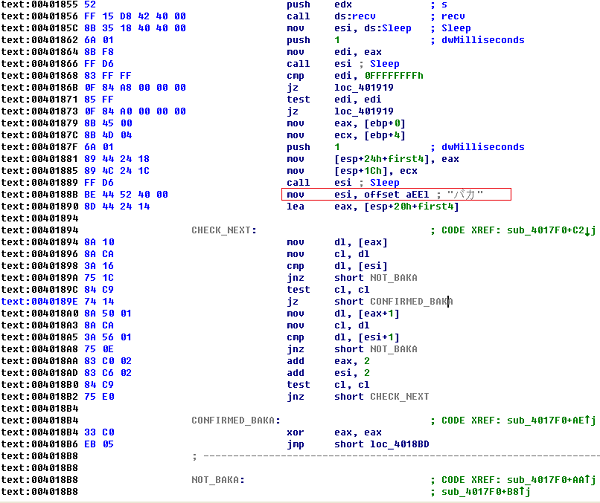
Figure 1. Attacker’s mark in Backdoor.Baccamun code
The malware checks the first 4 bytes of the received packets at virtual address 40188Bh. However, the string at that address is a bit peculiar.
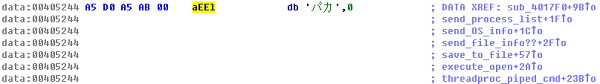
Figure 2. String compared at virtual address 40188Bh
In hex, the string is 0xA5, 0xD0, 0xA5, 0xAB. If the bytes were OR-ed by 0x80, the original bytes were 0x25, 0x50, 0x25, 0x2B, making the string “%P%+” in ASCII. A5, D0, A5, and AB do not make a meaningful word in European character codes for Windows. In Japanese character codes, it is not defined. In Korean character codes, A5D0 is a Greek Pi, but A5AB is not defined. In BIG5 character codes used in Taiwan and Hong Kong, it makes two Chinese characters, but is still not meaningful. However, in GB character codes used in China it makes a Katakana word in Japanese.
The string is baka (バカ), which means fool or idiot in Japanese. In GB character codes, some Japanese phrases can be expressed because all Hiragana and Katakana characters are defined. It is not difficult for a Japanese attacker to type the marker string on a Japanese OS, but a Japanese OS does not produce A5, D0, A5, or AB for the word because the code mapping is different. If this is attempted on a Chinese OS, the attacker is required to install a Japanese Input Method Editor (IME) and manually type baka. With OS versions in other languages, the attacker must input the hex code or use a back door controller program to send the marker string automatically.
Security Response also found another file (Trojan.Dropper) sent to the same Korean organization that drops the same back door program. Unlike the sample we have described above, the Trojan.Dropper sample is a simple executable file that has the name of a Japanese company as part of its file name.
Who perpetrated these attacks?
With a Word document in decent Korean, a marker string that can be translated to a Japanese word, and a Japanese word represented in Chinese GB character codes, it can be difficult to make a guess at who the attacker is. In some cases, the domain a back door connects to can give additional clues to an attacker’s identity, but in this case, it connected to a Dynamic DNS. However, it is likely that the attacker or attacker group is operating somewhere in East Asia and possesses multilingual skills.
Protection
Symantec protects users against this threat with the following detections:
Symantec advises users to be cautious when dealing with suspicious emails and to avoid clicking on suspicious links or opening suspicious attachments. Users should also ensure their security software is kept up to date. Other software should regularly be updated as well to prevent attackers from exploiting known vulnerabilities.