Symantec has discovered a new ransomware variant that pretends to originate from Microsoft and uses social engineering techniques to trick the victim into calling a toll-free number to “reactivate” Windows. In this case reactivating Windows means unlocking their computer. This is an offshoot of the notorious tech support and ransom browser lock scam and tech support ransomware scam we’ve covered in the past, this time, however, it is using a recognizable name.
We have seen the threat (freedownloadmanager.exe), which Symantec detects as Trojan.Ransomlock.AT, being distributed primarily in the United States. We have seen it used in limited attacks. It uses a prompt that mimics the look and feel of Microsoft’s trade dress (Figure 1), and states:
“Your Windows Licence has Expired , Please get a new one by calling on 1-888-303-5121 from Store Representative”

Figure 1. Screenshot of the lock screen displayed by the threat
Other than the localized spelling for the word “licence” (UK/Canada) versus “license” (US), and various odd uses of capitalization, punctuation, and grammar, this new variant offers the victim a compelling reason to call the toll-free number for assistance.
The threat has links to TeamViewer and Logmein in the lock screen as well. This isn't a structural weakness in either piece of software, but these links may be intended to offer the victim some sense of support and professionalism, as it can be assumed that the agent on the other side (the attacker or someone hired by them) will guide the victim through the process of unlocking the computer.
We called the toll-free number for more details and for a cost, but due to time constraints (we were on hold for more than 90 minutes), we were forced to hang up. The on-hold music and message were also convincing, and played random music with an automated voice repeating every so often: “We appreciate your business. All agents are currently busy assisting other callers, and please continue to hold for the next available agent.” After the 30-minute mark, it stated: “We apologize for the extended delay and appreciate your business. Please press any key to schedule a call back.”
Fortunately, further analysis revealed that the malware author left the unlock code in plain sight without using any obfuscation techniques (Figure 2). The malware itself is simplistic and does not contain any connections to a command and control server.
Victims of this threat can unlock their computer using the code: 8716098676542789
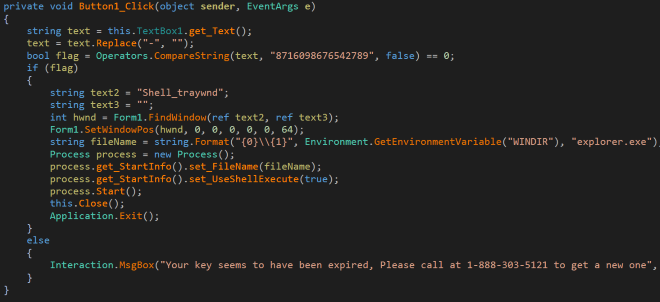
Figure 2: Unlock code 8716098676542789 can be found within the source
Additional revenue generation model through manipulated search results?
Victims with good instincts or intuition will probably perform a search on the toll-free number to see what the web has to offer. Someone has clearly taken advantage of this attack to offer questionable forms of help. A cursory search on the web for 1-888-303-5121 reveals dozens of sites (Figure 3), which appear to have been created by affiliates, and which try to appear as legitimate malware removal help sites. These sites use various scare tactics to try and coerce unsuspecting victims into following additional removal steps.
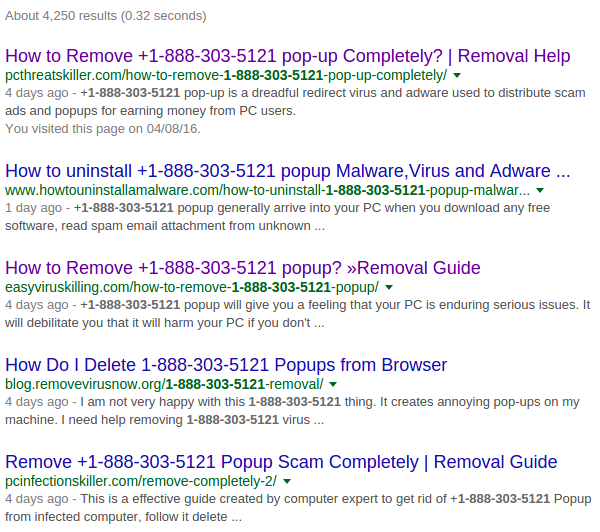
Figure 3. Manipulated search engine results
The removal suggestions contain generic and unhelpful banter to remove the program (Figure 4).

Figure 4. Fake website recommends removal steps for the threat
This threat represents an evolution of the tech support scams we’ve seen in the past. What makes this different from traditional ransomware is that it appears the attackers have carefully thought out how to maximize revenue generation by using a combination of branded ransomware alongside manipulated search results.
Tips on protecting yourself from ransomware
- Regularly back up any files stored on your computer. If your computer does become infected with ransomware, your files can be restored from the backup once the malware has been removed.
- Always keep your security software up to date to protect yourself against any new malware variants.
- Keep your operating system and other software updated. Software updates will frequently include patches for newly discovered security vulnerabilities that could be exploited by attackers.
- Delete any suspicious-looking emails you receive, especially if they contain links or attachments.
- Be extremely wary of any Microsoft Office email attachment that advises you to enable macros to view its content. Unless you are absolutely sure that this is a genuine email from a trusted source, do not enable macros and instead immediately delete the email.
Protection
Symantec and Norton products detect this latest ransomware variant as:
Further reading
If you would like to find out more about the threat posed by ransomware, you can read our whitepaper: The evolution of ransomware