Symantec Security Response has recently discovered the Sage 2.0 ransomware (Ransom.Cry) being delivered by the Trojan.Pandex spambot, which we have previously seen sending JS downloaders with spambots, banking Trojans, and ransomware as payloads. We have also recently observed Sage 2.0 sharing similar routines with the Cerber ransomware (Ransom.Cerber), although no link between the two malware families could be fully established.
Sage 2.0 evolved from Crylocker (Ransom.Cry), which emerged in September 2016, and continues to be used today. Sage was previously delivered through the Rig exploit kit (EK), but is now mostly delivered through spam. We have also seen Sage 2.0 being downloaded by the Trik botnet, which uses the Trojan.Wortrik malware to compromise computers.
Similarities with Cerber
The threat arrives on compromised computers as a .ZIP file attached to sexually explicit spam emails, as shown in Figure 1.
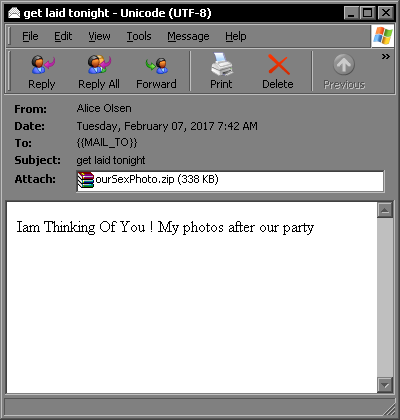
Figure 1. Sample of a sexually explicit spam email containing the malicious attachment
When executed, Sage 2.0 uses the Adobe PDF icon to pose as a .PDF file. It also uses a different packer from the previous releases.
Sage 2.0 also has some new routines that remind us of Cerber, such as offering multiple-language support in its ransom note.
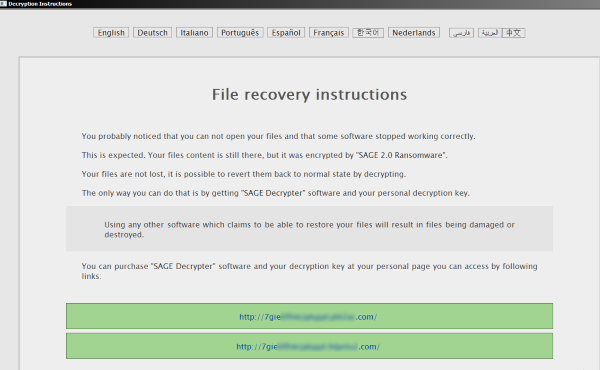
Figure 2. Sage 2.0’s most recent ransom note is an .HTA file with multiple-language support
Like Cerber, Sage 2.0’s ransom note is now an .HTA file that offers multiple language support, whereas it used to be an .HTML file. To be fancier, it also added new default icons for .HTA and .SAGE files in the registry. The .HTA file is displayed with a key icon and contains the ransom note, while the .SAGE file displays a lock icon and holds the locked files.
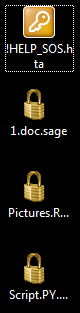
Figure 3. Sage has added new default icons for .HTA and .SAGE files
Also like Cerber, the new Sage 2.0 variant drops a .VBS script that uses the SAPI SpVoice interface to inform the affected user of the ransomware infection. This new version also ends database-related processes, something we’ve seen Cerber do to better infect files that may have been locked by running database processes.
Moreover, Sage 2.0 uses a process list that is the selfsame list we found in an old Cerber configuration, specifically from Cerber version 4.

Figure 4. Snippet from the Cerber 4 configuration showing the same process list used by Sage 2.0
The previous iteration of Sage 2.0 had clear indications that it was still under development. It would check for the %Temp%\lol.txt file and abort its encryption routine if the file was found. It would also blacklist the MY_QWemsadkjasd folder, which could be a location used in development, from its directory. These checks have been removed in the latest Sage 2.0 variants.
This newest version also has an updated shadow deletion routine to bring it more in line with current ransomware. The old code only executed vssadmin to delete shadow copies, but now Sage 2.0 also disables safe boot options and error recovery.
Conclusion
There is no concrete evidence as to whether the attackers behind Cerber are the same ones behind Sage 2.0. The two threats do not share the same packer, although Sage 2.0 mirrors some of Cerber’s routines. This could be an indication that Sage 2.0 is gearing up for more infections and mimicking Cerber because of its previous success.
[click_to_tweet:1]
Mitigation
Symantec recommends users follow these best practices to stay protected from ransomware threats:
- Delete any suspicious-looking emails you receive, especially if they contain links or attachments.
- Always keep your security software up to date to protect yourself against any new variants of malware.
- Keep your operating system and other software updated. Software updates will frequently include patches for newly-discovered security vulnerabilities that could be exploited by attackers.
- Regularly back up any files stored on your computer. If your computer does become infected with ransomware, your files can be restored once the malware has been removed.
Protection
Symantec and Norton products protect against these attacks with the following detections:
Antivirus
Intrusion prevention system