
Contributor: Shaun Aimoto
By leveraging Symantec’s Mobile App Insight automation, our researchers have found an interesting new threat that highlights the double-edged nature of some security software capabilities found in legitimate products.
The spyware we discovered poses as a “Google Service” app and uses an embedded copy of a legitimate security tool to compromise other security protection tools that could be used to defend against it. Symantec detects this threat as Android.Spywaller.
Malware behavior
The malware’s initial behavior is similar to many mobile threats. When launched, the app exits the user interface (UI) and hides its icon in an attempt to cover its tracks. It then releases an encrypted payload containing the malware service logic and loads it into memory. Once installed, the threat displays a “Google Service” icon on the device; however, there is no actual offering from Google with this name.

Figure 1. Malware displays a fake “Google Service” launch icon
The malware then tries to root the device and sits in the background collecting sensitive information. The collected information is sent to the malware’s backend server.
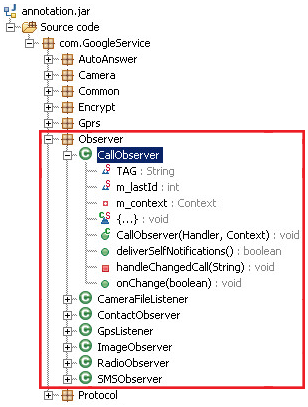
Figure 2. Reversed code showing registered observers used to spy on sensitive user data
Things get interesting
After examining the reversed payload, a clue emerged in the form of a method named disable360Network(). A closer look at this method revealed some interesting behavior: the malware checks to see if the Qihoo 360 mobile security app, which is popular in China, is installed on the compromised device. If the security app is installed, the malware will acquire the app’s unique identifier (UID).
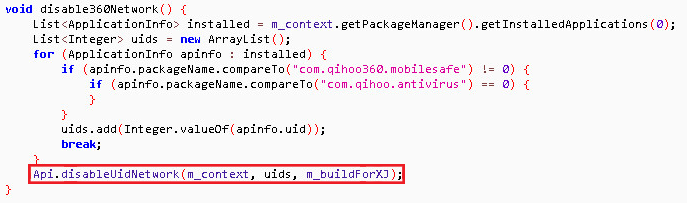
Figure 3. Malware obtains the UID for the Qihoo 360 security app on the device
The malware then drops and runs a firewall binary called DroidWall (a customized version of iptables for Android), and creates firewall rules that will block the targeted security application (in this case Qihoo 360) by referencing its UID. These days, many security scanners rely on the cloud to deliver protection, so blocking their communication would significantly compromise that ability.
DroidWall was first developed by Rodrigo Rosauro as an open source app aiming to help users protect their devices. The app was sold to AVAST in 2011 and its source code can still be easily obtained from Google Code and Github. In cybersecurity, the boundary between defense and offense can sometimes become very thin. An internet search for DroidWall will return many posts like this one discussing how DroidWall is able to help protect devices. However, this malware example reveals the other side of the story: in the wrong hands, some security tools can be used to actually compromise user security.
Targeting Chinese users
The deception and detection-prevention used by this malware targets a distinctly Chinese usage pattern. By posing as Google services, the malware entices users in China (where the official Google services, such as Google Play are not available) to download the malware. The Chinese market is also known to have a higher proportion of rooted devices which puts them at a higher risk of malware infection in general.
The spyware attempts to exfiltrate a wide array of sensitive data. In addition to system-based personally identifying information (PII) such as call logs, SMS messages, GPS readings, system browser data, emails, radio, images, and contacts, it also collects data belonging to specific third-party communication apps like BlackBerry Messenger, Oovoo, Coco, QQ, SinaWeibo, Skype, Talkbox, TencentWeibo, Voxer, Wechat, WhatsApp, and Zello. The extensive list of data gathered by this malware ranks it among the most comprehensive spyware we’ve come across.
While the infection numbers are relatively low, this threat is still noteworthy as it illustrates another instance of malware authors using legitimate tools for malicious purposes.
Mitigation
We recommend the following measures to help users to protect their devices against this threat:
Protection
Symantec and Norton products detect this threat as Android.Spywaller.