Contributor: Mark Anthony Balanza
Twitch has become one of the most popular online video services today. The platform, which allows people to live-stream their gaming sessions to an audience over the internet, experienced particular success in 2014. That year, there were 100 million unique visitors, 1.5 million broadcasters, and more than 16 billion minutes of videos watched each month on Twitch.
The popularity of Twitch allows some broadcasters to earn money while streaming their videos, provided that they have a large enough audience. While many broadcasters have managed to legitimately earn their viewers, others have attempted to artificially inflate their viewership figures by renting a botnet. Some of these botnets were created by infecting victims’ computers with malware and forcing them to keep Twitch streams open in the background.
How do broadcasters make money using Twitch?
Broadcasters can earn revenue through their Twitch streams in a number of different ways:
- Viewers can subscribe to broadcasters’ channels on a monthly basis in order to access new perks.
- Broadcasters can receive donations from viewers.
- Broadcasters can display ads either before, during, or after their streams.
Before broadcasters can take part in these revenue programs, they first need to gain a large audience that views their content regularly−an average concurrent viewership of more than 500 viewers.
The Twitch botnet marketplace
An online market has emerged to take advantage of this program, allowing people to take a shortcut and generate a large audience of bots for their Twitch channels. This scam isn’t exclusively tied to Twitch. Botnets are being used on other video platforms with similar revenue-generating programs, such as YouTube.
During our research, we found several Twitch botnet services that were for sale both on underground forums and on the open web. These services allow people to rent bots over a period of time to boost their Twitch channel viewership stats. The offerings are marketed as being easy for customers to set up. We also found that many services offered a single application that could generate a huge number of fake Twitch channel viewers.
For one botnet service, the seller claims that each “victim” on the botnet can view five streams on broadcasters’ Twitch channels. The affected computer is seemingly forced to open the Twitch channel streams, though the streams are hidden and muted so that the computer’s owner is unaware that anything is amiss.

Figure 1. Twitch botnet service claims each “victim” can view five streams on Twitch
Another service that we found lets broadcasters rent different botnet packages, depending on their budget. Along with offering viewers, the service also offers “chatters,” which are bots that post messages in the chat section on broadcasters’ Twitch streams. Prices range from US$29.99 for 100 viewers and 40 chatters to $159 for 1,000 viewers and 400 chatters.
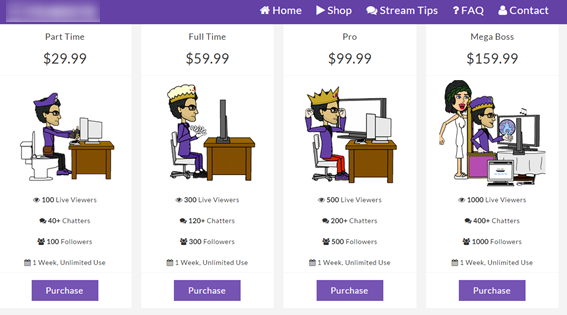
Figure 2. Twitch botnet service offers different rental packages
Another service offers monthly subscriptions for Twitch bot services, starting from $24.95. Along with offering viewers and chatters, this service has a customer support service to help broadcasters set up these bots to view their channel. This shows yet again how botnet rental services are maintaining a more “professional” appearance to attract customers.

Figure 3. Twitch botnet service offers customer support
Botnet malware
While some botnets may include computers where the user has agreed to take part in the scam, others include compromised computers that have been forced to become Twitch stream-viewing bots. We have observed one Twitch botnet threat in the wild, detected as Trojan.Inflabot. The malware appears to disguise itself as a fake Chrome or Adobe software update and has mainly infected computers in Russia, the US, UK, and Ukraine.

Figure 4. Top ten countries affected by Trojan.Inflabot
Once Trojan.Inflabot compromises a computer, it connects to the malware author’s community page on the Russian social network site vk.com. This page includes a URL to the server that gives the malware details on which Twitch stream to visit, along with the referrer URL. This allows the malware to force the compromised computer to view a broadcaster’s Twitch channel.
Trojan.Inflabot appears to come from cybercriminals in Russia who are using the threat to operate a Twitch botnet-for-rent service. The malware is not as sophisticated as other Twitch botnet threats lurking in underground forums, as it creates just one view per compromised computer. The following shows a Twitch broadcaster who may have used/rented Trojan.Inflabot to increase their audience.

Figure 5. Twitch broadcaster who may have rented a botnet powered by Trojan.Inflabot
What does the future hold?
While many broadcasters stream their gameplay online as a hobby, some have managed to turn it into a well-paid full time job. Over the past few years, this business model has grown sharply, so it’s unsurprising that scammers are piggybacking on the industry in a parallel underground economy.
Artificial audience inflation isn’t the only way that this emerging sector could be targeted. Our previous research has shown how attackers hired distributed denial-of-service attacks to take competing gamers offline. This could also be used to target game stream broadcasters to disrupt their channels.
Other existing malware could be tailored to target this business and top broadcasters. For example, attackers could target well-known broadcasters with banking or information-stealing threats. They could also use popular Twitch channels’ chat services to spread malware to the broadcasters’ fans.
Symantec and Norton protection
To stay protected against botnet malware, Symantec advises users to keep their computers, security software, and other programs up-to-date by applying the latest patches and updates.
Symantec and Norton products have the following detections in place to protect customers from this threat:
Antivirus
IPS