More Hidden App Malware Found on Google Play with over 2.1 Million Downloads
Malicious apps hide themselves after installation and aggressively display full-screen advertisements.
In recent times we’ve seen multiple malicious apps found in the Google Play Store by various cyber security firms, including Symantec, yet this problem doesn’t seem to be dissipating. We have uncovered another wave of malicious apps in the Play Store which have been downloaded more than 2.1 million times. We reported these apps to Google on September 2, 2019, and they were removed from the store.
A total of 25 Android Package Kits (APKs), mostly masquerading as a photo utility app and a fashion app, were published under 22 different developer accounts, with the initial sample uploaded in April 2019. These 25 malicious hidden apps share a similar code structure and app content, leading us to believe that the developers may be part of the same organizational group or, at the very least, are using the same source code base.
Remote configuration file
When first installed, the app’s icon is still visible on the device, enabling the user to open and interact with the app normally. However, unbeknownst to the user, a request is made in the background via a third-party service to download a remote configuration file.
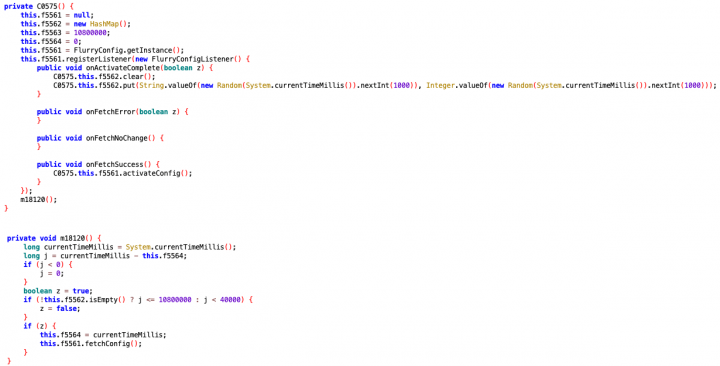
We intercepted the configuration file and spotted several different configurations including one that can toggle the app’s icon-hiding behavior, as well as other advertisement-related settings. For other APKs, the icon-hiding and advertisement-displaying behavior was disabled.

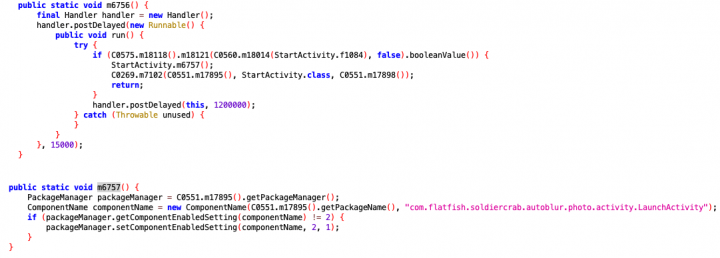
Once the configuration file is downloaded, the malware extracts the settings and applies them. From the malware code, we can see that keywords, such as “app_hideIcon” in the case of the icon-hiding feature, are encoded and encrypted. Various encryption keys and initialization vectors (IV) were used across all 25 APKs we found on Google Play (see Figures 4 and 5), which we believe is an effort on the malware authors’ part to avoid rule-based detection by antivirus scanners.
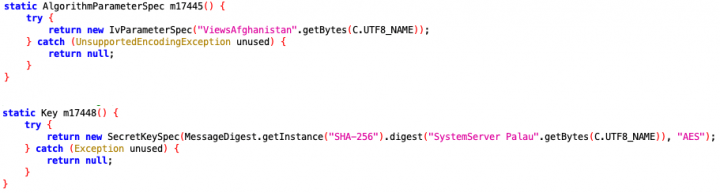
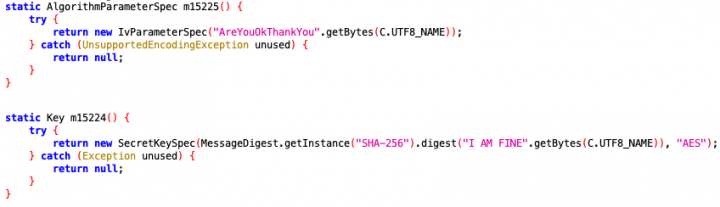
When a string—let’s use the icon-hiding string app_hideIcon as an example again—is decoded and decrypted, it is checked against the key in the configuration file. Then, if it matches, the corresponding value in the configuration file is used to determine if the app icon should be hidden. The setting setComponentEnabledSetting() is called to hide the app’s icon if the value of app_hideIcon is set to true.
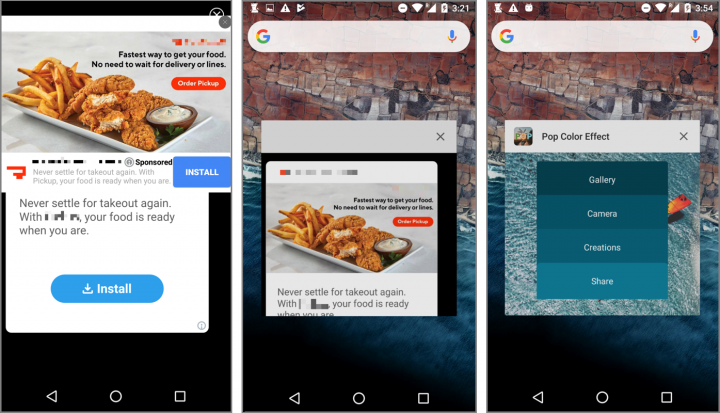
Once the app’s icon is hidden, the malware begins displaying advertisements, which are shown even when the app is closed. Full-screen advertisements are displayed at random intervals with no app title registered in the advertisement window, so users have no way of knowing which app is responsible for the behavior.
Monetary gain from advertising revenue is likely the motivating factor behind these apps. Thanks to the apps’ ability to conceal their presence on the home screen, users can easily forget they downloaded them. As such, the malware authors can freely and aggressively display advertisements to users, with minimal evidence leading back to them.
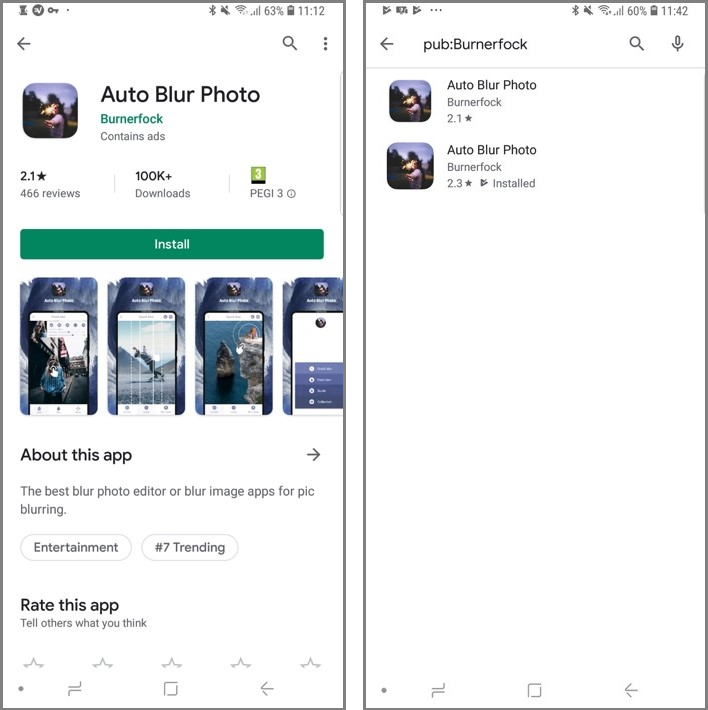
Out of the 22 developer accounts used to publish these apps, we spotted one developer named Burnerfock had published two identical apps named Auto Blur Photo with the same icon and title. However, only one of these apps carried out the previously described malicious behavior. The other sample was free of malicious code and was present in Google Play’s Top App Charts in the Top Trending Apps category, ranking number 7 on the list. We believe that the developer deliberately creates a malicious copy of the trending app in the hope that users will accidentally download the malicious version.
Unlike the previous hidden app malware we discovered, this batch does not have the icon-hiding function hardcoded in the APK. Instead, the switch is controlled remotely via the downloaded configuration file, allowing the malware developer to evade Google Play’s rigorous security testing.
Protection
Symantec and Norton products detect these malicious apps as:
Mitigation
Stay protected from mobile risks and malware by taking these precautions:
- Keep your software up to date.
- Do not download apps from unfamiliar sites.
- Only install apps from trusted sources.
- Pay close attention to the permissions requested by apps.
- Install a suitable mobile security app, such as Norton or Symantec Endpoint Protection Mobile, to protect your device and data.
- Make frequent backups of important data.
Indicators of Compromise
| Hashes | Package | Developer | Download Count |
|---|---|---|---|
| cf334618c708e35294430dcd0233373df334e7b1d2c250baa719de3ca5740140 | com.acaleph.octopus | Kulomylong | 500,000 |
| 1f083fe5d5eb53bc5fa417283b0992b426bff66a917f878e97216ba6588f2004 | com.flatfish.soldiercrab.autoblur.photo | Burnerfock | 100,000 |
| 0441c5d74fd702a4533006e951df4f0af17b0d7571933289044637807e1dba57 | com.jordan.iraq.blur.image.pro | Fisher Dev | 100,000 |
| 3e045e098c26889acf0cd5283a9d06e0cea97a161c31d23f3fe493d396a710df | com.hammergod.picture.photo | kenneth Ortiz | 100,000 |
| fbb334a8dedbc84e4ce9b48606df9e2bfde35ee38ea01bfc489ca25784c35684 | com.yongdegree.face.feature | Fater Dev | 100,000 |
| 0dcfc4612f76755ebaf67c41dc8a64255d3df78e7e8862349ced602fe57175c9 | com.palau.guam.fashion.hairstyles.pic.editor | Goveroy Dev | 100,000 |
| d71fadd872120ea5787964bf66bf8b873e06ff2bd51097ded4b204418fdcbcdc | com.kiribati.zowbat.image.blur.editor.free | Setperal | 100,000 |
| 1e93f794dbd0ceca72c14b76a448b6bad83ab9b496449ddb307e10bb3c0e0596 | com.pottwal.bowhead | Kensendy | 100,000 |
| 6eb5e782e8eecdf85e789d679965711737b700a9f9d0e0f76314d34914908430 | com.maxwell.photocutpro | WWL Dev | 100,000 |
| 3211609433478c95b32ba71a0e91c9c6557e1b8df4d17d000ba0f2619b93db99 | com.yasuo.art | Magicalla Studio | 100,000 |
| fd6fe195c193e4d4fb4d0cd616375a2a0e53eb82b72f339c7b7feb2a7926e2ef | com.estonia.brunei.fashion.hairstyles.pic.editor2019 | Digtal Dev | 100,000 |
| b0f4733366271483976c22a8198a4578ee1ccf8ab782d287c6255154ec36cc9c | com.rwanda.seychelles.latest.hairstyles.free | Lyynforture | 100,000 |
| e3422e09f19266fdc6e669b1ebad105c655a97062081cddc9243e008100a6ca0 | com.positive.photo.collage | Lyynforture | 100,000 |
| b04bfcdb00e27f5a3818b564150dbba04ac42eec92b15f2e9db9084f0c822851 | com.gayligayqi.cut.photo.editor | Superjunia | 100,000 |
| 27cce7478dbe8829bfe114c1b41d57305a62efdbd12333949a6711895964a1ea | com.cyprus.ghana.blur.image.plus | Past Dev | 100,000 |
| f168e313f02255d5d635a9fa4634c1aa4809917684602fadb561e27de00785e7 | com.jiajia.autocut.photo | OOI Dev | 100,000 |
| 7b49250a56dae52dc23cb88d590525761b3c0c4acc17f73911b4dc6e7e11cdc3 | com.hanroom.cutbackground | Richard Media Studio | 50,000 |
| a9c1e1c2e70db3df390ec88d2729208aba41af30b04a44d13b4bd4f525fb90bc | com.oman.mayotte.hairstyles.photo.editorplus | FFmore Dev | 50,000 |
| f2f9fa37ef6c1681a54da31a9e450dd85653a4ca61c4c16eb58f1f401172d01f | com.amazing.photo.cutout | Sistermopub | 10,000 |
| 3ecfd97550f8928acae04b13b608b9c8b7080f7ac59b79b45c7f273cff3e7d76 | loop.photo.com.photoloop | Sistermagci | 10,000 |
| 92239c6590adc226ca70682e349dab78b8e6448ed70fa0a30548b4d2fae3b9ea | com.pop.color | Pumana Dev | 10,000 |
| ba8b26106d5b2d74abeeb62ffbbdbc6b80e80bf7add86a2af57e96dfd6917586 | com.sky.camera.pro.skycamerapro | HCamera Studio | 10,000 |
| 9135a41d998864db84cfa98734e23bb94e71d9f8614f72d3d795a718c8ea821e | com.seisikou.photobackground | Flydog Dev | 1,000 |
| 2fb85618bfff2afda9f665177f9ef2bee208f8ba9ba87cdfee02f22ca5a19c22 | com.kiribati.jordan.blur.image.plus | Past Dev | 5 |
| 492f386f1e8a6a8be47bb920641d7c820a2aabb34f54e1cdfa08f1aad2ffb59b | com.fiji.brunei.photo.blur.background.maker2019 | Goulmook Dev | 1 |










We encourage you to share your thoughts on your favorite social platform.